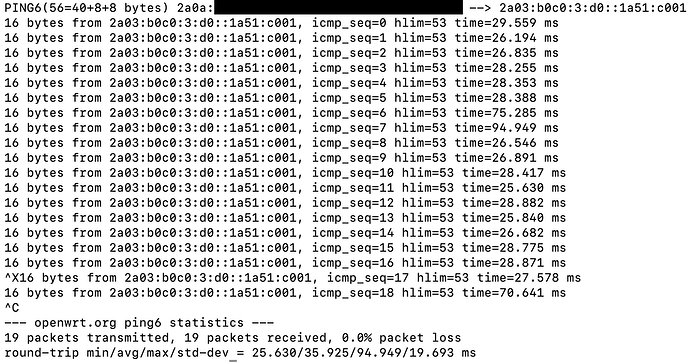
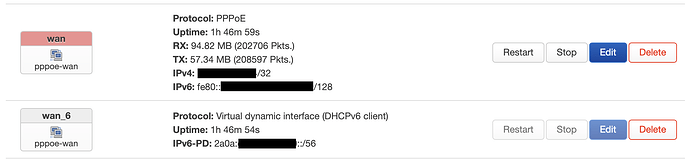
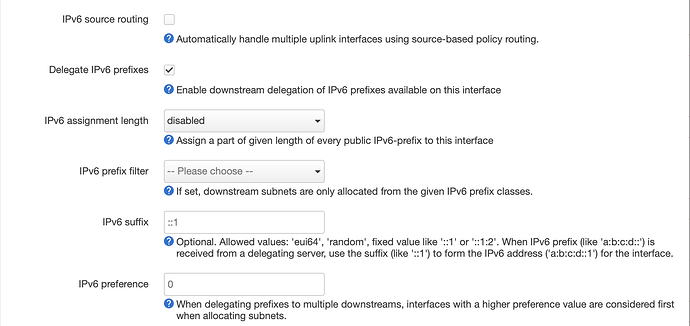
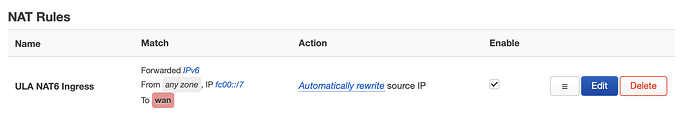
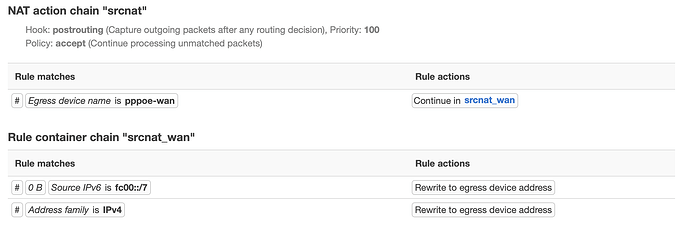
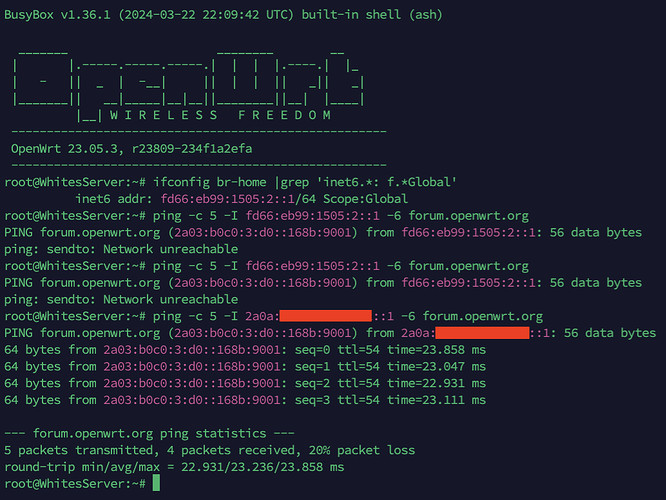
I got the same ping: sendto: Network unreachable when I set my wan6 interface to use sourcefiltering:
root@LEDE:~# uci set network.wan6.sourcefilter=1
root@LEDE:~# ifup wan6
root@LEDE:~# ping -c 5 -I fd2c:e7de:cb6b:1::1 -6 forum.openwrt.org
PING forum.openwrt.org (2a03:b0c0:3:d0::168b:9001) from fd2c:e7de:cb6b:1::1: 56 data bytes
ping: sendto: Network unreachable
and then when I return it to not do source filtering, we're good again:
root@LEDE:~# uci set network.wan6.sourcefilter=0
root@LEDE:~# uci commit
root@LEDE:~# ifup wan6
root@LEDE:~# ping -c 5 -I fd2c:e7de:cb6b:1::1 -6 forum.openwrt.org
PING forum.openwrt.org (2a03:b0c0:3:d0::168b:9001) from fd2c:e7de:cb6b:1::1: 56 data bytes
64 bytes from 2a03:b0c0:3:d0::168b:9001: seq=0 ttl=48 time=102.839 ms
64 bytes from 2a03:b0c0:3:d0::168b:9001: seq=1 ttl=48 time=105.631 ms
64 bytes from 2a03:b0c0:3:d0::168b:9001: seq=2 ttl=48 time=100.852 ms
64 bytes from 2a03:b0c0:3:d0::168b:9001: seq=3 ttl=48 time=99.696 ms
64 bytes from 2a03:b0c0:3:d0::168b:9001: seq=4 ttl=48 time=99.882 ms
--- forum.openwrt.org ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 99.696/101.780/105.631 ms
That suggests that your IPv6 wan is not actually turning off sourcefilter.
For DHCPv6, it works, and it's driven by /lib/netifd/proto/dhcpv6.sh which sets an environment variable NOSOURCEFILTER=1 for /usr/sbin/odhcp6c to pass through to /lib/netifd/dhcpv6.script, which manages the routes.
In my case, the net difference in the routing tables is visble in the default IPv6 route. You want something like this:
# ip -6 route |grep ^default
default via fe80::ae4b:c8ff:fe4d:b8f2 dev wan metric 512
to get the default route for all source addresses. If you see default from xyz::/56 ... then you've got source filtering.
Anybody know how to get the equivalent of sourcefilter disabled for pppoe-provisioned IPv6?
Maybe there's something you can do with /lib/netifd/ppp6-up by adding a callout script in /etc/ppp/ip-up.d ?
Or, looking at the ppp6-up script, it seems to be creating the virtual interface, it is mentioning dhcpv6 so maybe there's just something we missed with how to set the sourcefilter variable?