I used this page to set up my wireguard "server" on the router: https://openwrt.org/docs/guide-user/services/vpn/wireguard/server
openwrt version: OpenWrt 22.03.5
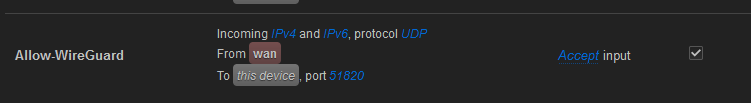
traffic rules for the firewall:
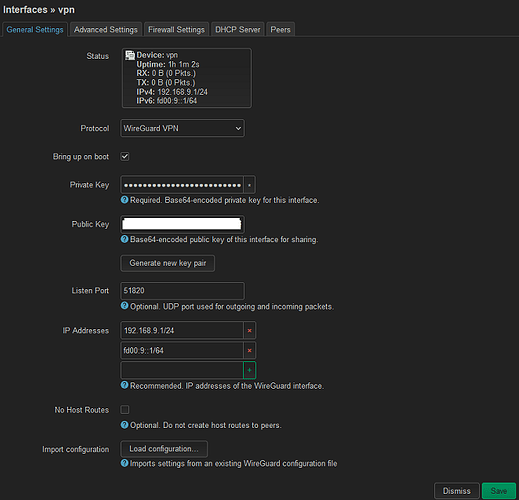
interface:
Client:
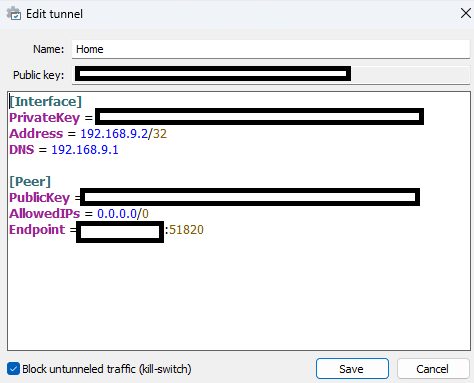
The clients are able to connect and get the 192.168.9.2 IP, however they cant access the internet, and i noticed they are not able to receive any data. tx goes up, and rx stays at 0.
What could be the cause of this?
Do you have a corresponding rule to allow traffic to leave the WireGuard VPN via the WAN? Alternately, if you really trust the VPN, is the WireGuard interface in the lan zone?
What are the contents of /etc/config/network and /etc/config/firewall? Redact any keys and passwords.
1 Like
/etc/config/network
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd46:34b2:3a75::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '94.140.14.14'
list dns '94.140.15.15'
config device
option name 'eth0.2'
option macaddr '<REDACTED>'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config interface 'GUEST'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option device 'eth0.3'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 4'
option vid '3'
option description '3rd port'
config device
option type 'bridge'
option name 'Guest VLAN'
list ports 'eth0.3'
option ipv6 '0'
option macaddr '<REDACTED>'
option mtu '1500'
option txqueuelen '1000'
config interface 'GUEST_WLAN'
option proto 'static'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
option device 'BR-GUEST_WLAN'
config device
option type 'bridge'
option name 'BR-GUEST_WLAN'
option mtu '1500'
option txqueuelen '1000'
list ports 'eth0'
option macaddr '<REDACTED>'
option mtu6 '1500'
option dadtransmits '1'
config interface 'vpn'
option proto 'wireguard'
option private_key '<REDACTED>'
option listen_port '51820'
list addresses '192.168.9.1/24'
list addresses 'fd00:9::1/64'
config wireguard_vpn 'wgclient'
option public_key '<REDACTED>'
option preshared_key '<REDACTED>'
list allowed_ips '192.168.9.2/32'
list allowed_ips 'fd00:9::2/128'
/etc/config/firewall
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
list network 'lan'
list network 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone 'wan'
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guest'
option output 'ACCEPT'
option forward 'REJECT'
list network 'GUEST'
option input 'REJECT'
config forwarding
option src 'guest'
option dest 'wan'
config rule
option name 'Guest DHCP'
list proto 'udp'
option src 'guest'
option dest_port '67'
option target 'ACCEPT'
config rule
option name 'Guest DNS'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
config zone
option name 'guest_wlan'
option output 'ACCEPT'
option forward 'REJECT'
list network 'GUEST_WLAN'
option input 'REJECT'
config forwarding
option src 'guest_wlan'
option dest 'wan'
config rule
option name 'GUEST_WLAN DHCP'
list proto 'udp'
option src 'guest_wlan'
option dest_port '67'
option target 'ACCEPT'
config rule
option name 'GUEST_WLAN DNS'
option src 'guest_wlan'
option dest_port '53'
option target 'ACCEPT'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
Huh. That ought to work, unless I'm missing something.
The default firewall rules permit lan-lan traffic, and both the lan and vpn interfaces are in that lan zone.
Do other devices in your LAN and Guest segments have working outbound Internet connectivity? Is it only the WireGuard peers which are having problems?
Only the wireguard clients are having issues, yes. I have not restarted the router since setting up wireguard, however. I should also note i have only tested the clients on an ISP from a mobile network...
Missed that the first time around.
Is there something which might be intercepting the initial handshake?
Does your router have a public IP address (by DHCP) on its WAN interface? Or does it have an RFC1918 or CGNAT address?
If you're behind an RFC1918 or CGNAT address, you're unlikely to be able to allow incoming traffic.
That's fine. It's how I "pretend I'm not at home" when testing my inbound connections.
Sorry, ive been ninja editing! This is definitely a possibility. How do I verify CGNAT is at play?
What's your router's WAN IP address? If it's 100.64.x.x then you're definitely behind CGNAT. Even if it's not 100.64.x.x, you can easily check by comparing your router's WAN IP address with the response from, say, ifconfig.co
I am getting an IPv6 address from ifconfig.co. The IPv4 is a 68.x.x.x block. (ipv4.icanhazip.com)
No sign of a 100.64.x.x.
Does the 68.x.x.x address from ipv4.icanhazip.com match what your router says is its WAN address? Do the two agree?
And then, assuming the two do agree, does the Endpoint in your Windows client's configuration contain the same 68.x.x.x IP address? Or, if using a DNS name, does the DNS name resolve to the 68.x.x.x IP address?
Yes on the IPv4 side. The IPv6 prefix delegated looks correct, but the address is different. (definitely something I need to get a bit more educated on at some point)
Yes on the wireguard windows client. Endpoint in the wireguard configuration contains my WAN IPv4 address.
You and me both. My ISP does provide IPv6 but I've not set aside enough time to learn how to use it properly. Doesn't help that my router doesn't do PD properly... ugh.
Anyway, that's my problem, not yours.
It might be worth doing some packet-sniffing. On the Windows machine, if you have (or can get) a copy of Wireshark, you can check for outbound traffic leaving the appropriate network interface destined at your router's WAN address on 51820/udp.
On the router, if you have (or can install) tcpdump, you can perform the same check for traffic arriving at the appropriate network interface destined at your router's WAN address on 51820/udp.
Okay, really dumb question time: have you double-checked the private and public keys for both peers? If there's a single typo, it'll prevent any handshakes.
1 Like
Ah! That's it: the keys.
The router has a pre-shared key defined, but the Windows peer does not.
If you're using a pre-shared key it must be present and identical on all peers.
1 Like
Good call on the PSK. Added that but I still have the same issue.
Ran wireshark on the windows client:
It is not getting past handshake init.
Going to see if I can't get tcpdump on the router now.
For the avoidance of doubt, did you add the entry to the Windows tunnel? It should look something like this:

Also, might be worth testing without the PSK at either end for now. Get WG working with the bare minimum config, then add complexity gradually.
Yes
the output for tcpdump on the router, it does see the request, but something is definitely not working with the handshake.
root@OpenWrt:~# tcpdump -n -i eth0.2 | grep "<REDACTED_PHONE_WAN_IP>"
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0.2, link-type EN10MB (Ethernet), capture size 262144 bytes
21:58:15.137469 IP <REDACTED_PHONE_WAN_IP>.12092 > <REDACTED_ROUTER_WAN_IP>.51820: UDP, length 148
21:58:20.133861 IP <REDACTED_PHONE_WAN_IP>.12092 > <REDACTED_ROUTER_WAN_IP>.51820: UDP, length 148
21:58:25.197964 IP <REDACTED_PHONE_WAN_IP>.12092 > <REDACTED_ROUTER_WAN_IP>.51820: UDP, length 148
21:58:30.329073 IP <REDACTED_PHONE_WAN_IP>.12092 > <REDACTED_ROUTER_WAN_IP>.51820: UDP, length 148
Certainly looks like it. I can only suggest stripping the WG config back to the bare minimum needed to establish a tunnel. Once that;'s working, then add the extra stuff back into it, testing each time you make a change.
1 Like