I have configured Wireguard on a Belking RT3200 installed with the latest OpenWRT 22.03.
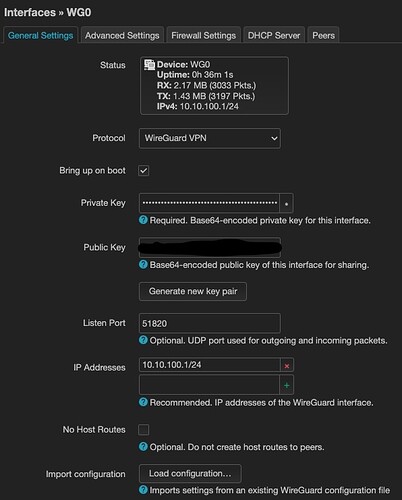
I configured wireguard using Luci and have not modified manually any config file or used the command line in any way.
All peer configurations are entered in Luci and the config is transferred to the peer devices scanning the qrcode generated by Luci
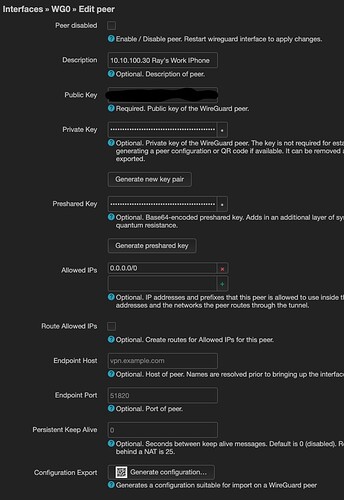
Each peer use different Private & Public keys as well as different pre-shared keys.
All keys are generate using the Generate keys buttons available in Luci.
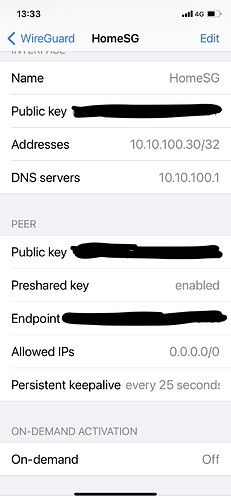
In addition to the Config transferred scanning the qrcode, I enter manually in the peers wireguard app different ip addresses and configure the DNS to point to the openwrt wireguard address.
I restart the openwrt wireguard interface in between each configuration changes.
I have configured successfully wireguard on a first peer using wireguard for android.
I routed all peer traffic via the openwrt endpoint using Allowed IP Address 0.0.0.0/0.
The Android peer functioned as expected.
I configured an additional peer using wireguard for IOS.
I routed all peer traffic via the openwrt endpoint using Allowed IP Address 0.0.0.0/0
The new IOS peer function as expected.
The previously configured Android peer is able to connect to the openwrt endpoint but i can no longer access my internal network or the Internet.
Traffic seem to go from the peer to openwrt but only few bytes seem to come back.
I created again an additional wireguard peer on MacOs.
In the same way the Mac could access the internal network and internet, but now the previously configured Android and IOS peers no longer function.
I erased the Android peer and reconfigured it from scratch on both openwrt and the Android peer, now the Android peer is functioning fine but the IOS and MAC peers are not able to use the wireguard tunnels.
It seem thus that only the last per configured work properly while previous peer stop functionning once I configure a new one.
Any idea what I am doing wrong ?
My Openwrt Wireguard Config
My Luci Android Peer Config
My Luci IOS Peer Config
My Android peer wireguard app config
My IOS peer wireguard app config
I hid my keys andpublic IP addresses and port, however each peer has different public, private and preshared keys. The public IP Address is accessible and all peers point to the same address and use the same port.
Thanks for any comment that would help understand the issue.
Regards
-R