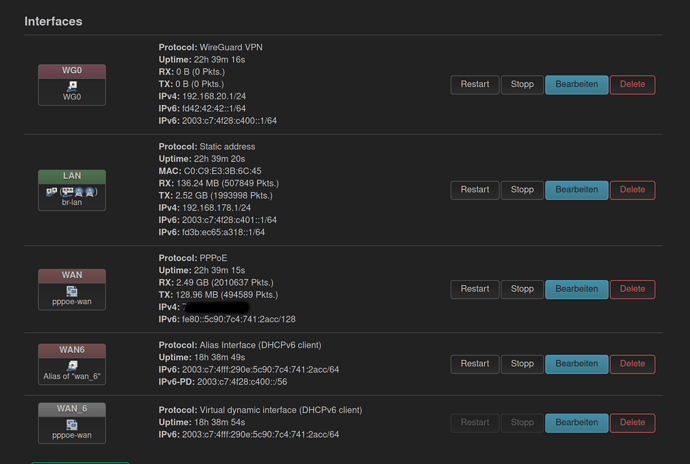
Hello community,
im struggling now for a while with Wireguard and IPv6. My ISP is providing me an ipv6-pd/56 address.
Here you can have a look:
So i have a peer now which is configured as followed:
client PJ
config wireguard_WG0
option description 'PJ'
option public_key 'PUBLIC KEY CLIENT PJ'
option route_allowed_ips '1'
list allowed_ips '192.168.20.8/32'
list allowed_ips 'fd42:42:42::2/128'
and here is the OpenWRT router
config interface 'WG0'
option proto 'wireguard'
option private_key 'PRIVATE KEY ROUTER'
option ip6assign '64'
list addresses '192.168.20.1/24'
list addresses 'fd42:42:42::1/64'
option listen_port '51902'
option mtu '1280'
list ip6class 'wan6'
and here is the Wireguard config on the client side
PJ CLIENT
[Interface]
PrivateKey = PRIVATE KEY
Address = 192.168.20.8/24, fd42:42:42::2/64, fd3b:ec65:a318::2/64, 2003:c7:4f48:4300::2/64
MTU = 1420
[Peer]
PublicKey = PUBLIC KEY ROUTER
Endpoint = mydomain.net:51902
AllowedIPs = 0.0.0.0/0, ::/0
When i try to bring this up i get something like this
interface: wg0
public key: PUBLIC KEY CLIENT
private key: (hidden)
listening port: 56077
fwmark: 0xca6c
peer: PUBBLIC KEY ROUTER
endpoint: [2003:c7:4fff:4988:a80a:61af:c5c6:95db]:51902
allowed ips: 0.0.0.0/0, ::/0
transfer: 0 B received, 888 B sent
FW rules of the router:
root@Home:~# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].synflood_protect='1'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Support-UDP-Traceroute'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='33434:33689'
firewall.@rule[9].proto='udp'
firewall.@rule[9].family='ipv4'
firewall.@rule[9].target='REJECT'
firewall.@rule[9].enabled='false'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].name='VPN'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='REJECT'
firewall.@zone[2].masq='1'
firewall.@zone[2].mtu_fix='1'
firewall.@zone[2].network='WG0'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='VPN'
firewall.@forwarding[1].dest='lan'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].src='VPN'
firewall.@forwarding[2].dest='wan'
firewall.@nat[0]=nat
firewall.@nat[0].name='VPN'
firewall.@nat[0].proto='all'
firewall.@nat[0].src='lan'
firewall.@nat[0].src_ip='192.168.20.0/24'
firewall.@nat[0].target='MASQUERADE'
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].name='WIREGUARD'
firewall.@redirect[0].src='wan'
firewall.@redirect[0].dest='VPN'
firewall.@redirect[0].dest_ip='192.168.178.1'
firewall.@redirect[0].src_dport='51902'
Maybe someone can point in the right direction...
Greetings