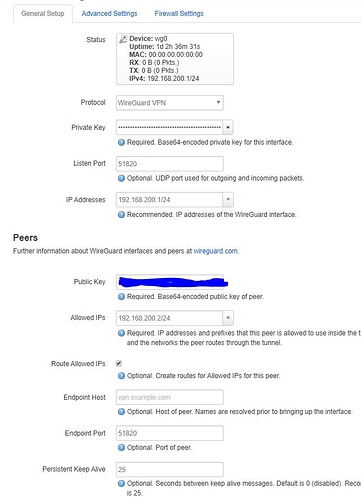
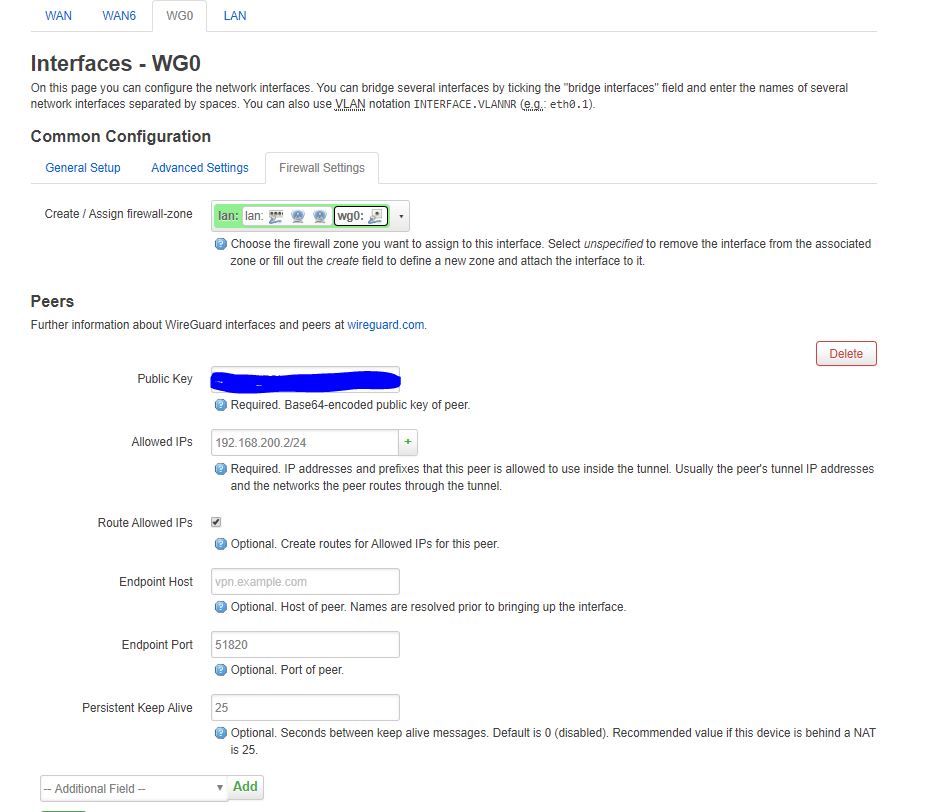
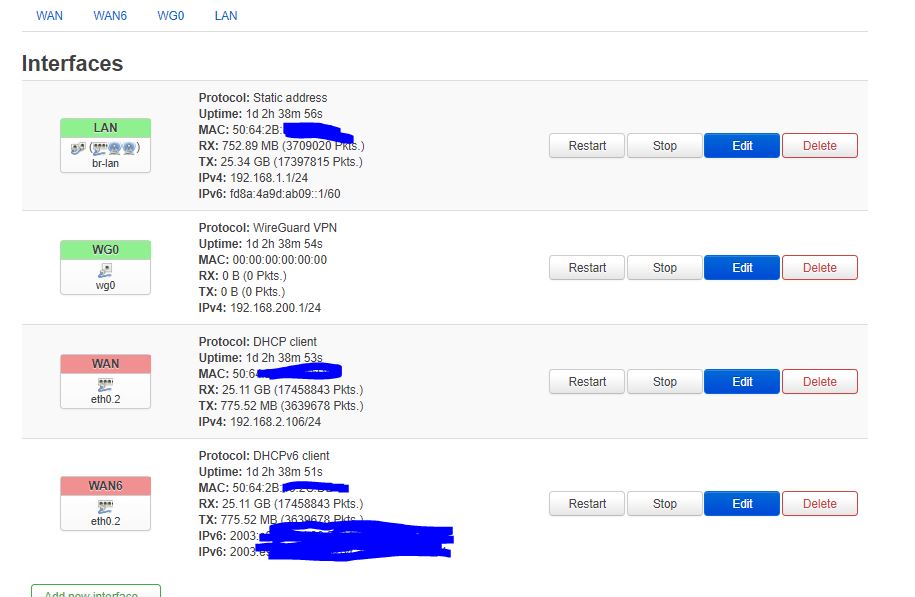
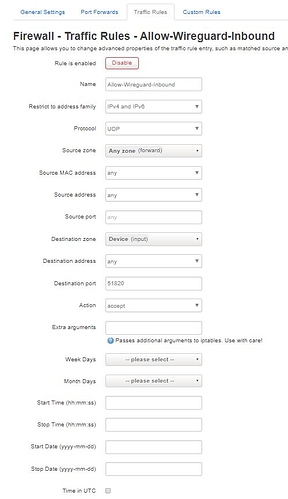
Here is the output
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
22:55:22.857051 ethertype IPv4, IP (tos 0x0, ttl 54, id 49023, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:22.857051 IP (tos 0x0, ttl 54, id 49023, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:28.146161 ethertype IPv4, IP (tos 0x0, ttl 54, id 29483, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:28.146161 IP (tos 0x0, ttl 54, id 29483, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:33.311519 ethertype IPv4, IP (tos 0x0, ttl 54, id 42064, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:33.311519 IP (tos 0x0, ttl 54, id 42064, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:38.610300 ethertype IPv4, IP (tos 0x0, ttl 54, id 38133, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:38.610300 IP (tos 0x0, ttl 54, id 38133, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:43.790562 ethertype IPv4, IP (tos 0x0, ttl 54, id 47247, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
22:55:43.790562 IP (tos 0x0, ttl 54, id 47247, offset 0, flags [none], proto UDP (17), length 176)
80.187.118.129.10062 > 192.168.2.106.51820: [udp sum ok] UDP, length 148
And
root@OpenWrt:~# wg show
interface: wg0
public key: XXX
private key: (hidden)
listening port: 51820
peer: XXX
allowed ips: 192.168.200.2/32
persistent keepalive: every 25 seconds
root@OpenWrt:~#