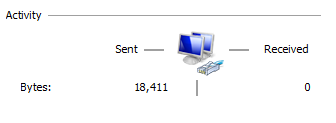
Sorry for yet another WG configuration post, but I couldn't wrap my head around it after reading multiple other threads. Please do correct me if my terminology is wrong!
My setup is quite basic - my Openwrt box is bridged to my ISPs NT box, so WAN is managed via PPOE.
My LAN subnet is 192.168.1.0/24
# /etc/config/network
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
I've setup a new WG interface, and have it configured to reside in the 192.168.9.0/24 subnet, and added a peer which is mean to be my "road-warrior" device. I would like this device to be able to communicate with devices in my LAN, so have added this interface to my LAN zone, and allowed incoming traffic on the defined port.
# /etc/config/firewall
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan WG_TUN'
config rule
option name 'Allow-Wireguard-Inbound'
option target 'ACCEPT'
option src '*'
option proto 'udp'
option dest_port '51820'
As I understood, this peer will be assigned the address 192.168.9.2 and all traffic will be routed through the default gateway (WG_TUN) because of the /32 CIDR
# /etc/config/network
config interface 'WG_TUN'
option proto 'wireguard'
option private_key 'xx1'
option listen_port '51820'
list addresses '192.168.9.1/24'
config wireguard_WG_TUN
option public_key 'xx4'
option description 'R-W'
option preshared_key 'xx3'
list allowed_ips '192.168.9.2/32'
To test my setup, I am trying to connect via a temporary hostspot.
[Interface]
PrivateKey = xx4
Address = 192.168.9.2/32
[Peer]
PublicKey = xx1
PresharedKey = xx3
AllowedIPs = 0.0.0.0/0,::/0
Endpoint = my.host.name:51820
But now, I can't seem to connect/handshake with this setup, and am kinda at a dead end on how to debug this.
[TUN] [Tun.Home] Binding v4 socket to interface 32 (blackhole=false)
[TUN] [Tun.Home] Setting device v4 addresses
[TUN] [Tun.Home] Listening for UAPI requests
[TUN] [Tun.Home] Startup complete
My client logs suggest that it's unable to find my "server" to complete the handshake.
Hints on how to proceed?