olexiiy
February 15, 2024, 6:48am
1
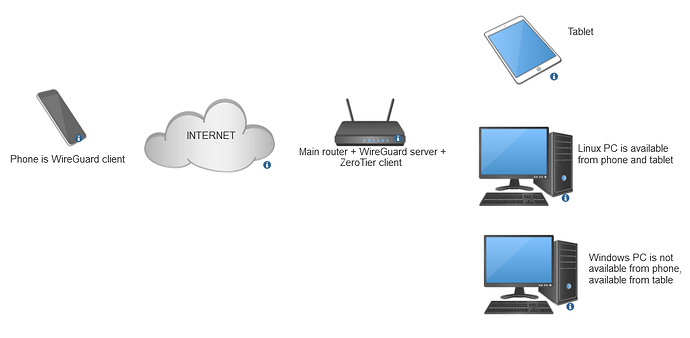
I have a WG server and a ZeroTier client on the router.
Results:
The apple tablet does not respond at all.
The laptop with Windows responds in LAN, but not in WG and ZT.
A PC with LAN on Linux is available, but it is not available with Windows via WG and ZT, this is available with MacOS on LAN and via WG, but not via ZT.
Can you tell me or explain why this is so?
It's very hard to understand your scenarios and the problem you are experiencing. We have no idea what your network topology looks like, nor do we understand how you are testing and where from.
Maybe you could start with a diagram that shows the details of your topology and also provide the configuration of your router.
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
1 Like
olexiiy
February 15, 2024, 7:30am
3
ubus call system board
etwork
cat /etc/{
"kernel": "5.15.137",
"hostname": "xr500",
"system": "ARMv7 Processor rev 0 (v7l)",
"model": "Netgear Nighthawk XR500",
"board_name": "netgear,xr500",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "ipq806x/generic",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
}
}
config/wroot@xr500:~# cat /etc/config/network
ireless
cat /etc
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda8:46c6:c714::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
option stp '1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
option peerdns '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
list dns '8.8.8.8'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
config interface 'WG_0'
option proto 'wireguard'
option private_key 'EGsY/Vd5Lf42qRT+mQKXtsGLN7jFDc6Z46MogeYP8GM='
option listen_port '51820'
list addresses '10.0.0.1/24'
option delegate '0'
config wireguard_WG_0
option description 'mi11i'
option public_key 'CB2/aA21SW+80kqzOCYX9YY5VN+b3YZJkIukBTR2lEM='
option private_key 'IMGxdcMX1ehuAGdN2/6C4Hy/UydNnQLda0b2IaTGpW4='
list allowed_ips '10.0.0.11/32'
option route_allowed_ips '1'
root@xr500:~# cat /etc/config/wireless
/config/dhcp
cat
config wifi-device 'radio0'
option type 'mac80211'
option path 'soc/1b500000.pci/pci0000:00/0000:00:00.0/0000:01:00.0'
option channel '149'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option country 'PA'
option txpower '30'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Wi-Max'
option encryption 'psk2+ccmp'
option dtim_period '3'
option disassoc_low_ack '0'
option key '75941771tv'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '1'
option bss_transition '1'
option proxy_arp '1'
option ieee80211r '1'
option mobility_domain '0013'
option reassociation_deadline '20000'
option ft_over_ds '1'
option ft_psk_generate_local '1'
option ieee80211k '1'
option time_advertisement '2'
option time_zone 'EET-2EEST,M3.5.0/3,M10.5.0/4'
option hidden '1'
config wifi-device 'radio1'
option type 'mac80211'
option path 'soc/1b700000.pci/pci0001:00/0001:00:00.0/0001:01:00.0'
option channel '6'
option band '2g'
option htmode 'HT40'
option cell_density '0'
option country 'PA'
option txpower '30'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'Wi-Max'
option encryption 'psk2+ccmp'
option dtim_period '3'
option disassoc_low_ack '0'
option key '75941771tv'
option ieee80211r '1'
option ft_over_ds '1'
option ft_psk_generate_local '1'
option ieee80211k '1'
option time_advertisement '2'
option time_zone 'EET-2EEST,M3.5.0/3,M10.5.0/4'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '1'
option bss_transition '1'
option proxy_arp '1'
option mobility_domain '0013'
option reassociation_deadline '20000'
config wifi-iface 'wifinet2'
option device 'radio1'
option mode 'mesh'
option encryption 'sae'
option mesh_id 'my-mesh'
option mesh_fwding '1'
option mesh_rssi_threshold '-69'
option dtim_period '3'
option disassoc_low_ack '0'
option key '75941771tv'
option time_advertisement '2'
option time_zone 'EET-2EEST,M3.5.0/3,M10.5.0/4'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '1'
option bss_transition '1'
option proxy_arp '1'
option network 'lan'
option disabled '1'
config wifi-iface 'wifinet3'
option device 'radio0'
option mode 'mesh'
option encryption 'sae'
option mesh_id '5g-mesh'
option mesh_fwding '1'
option mesh_rssi_threshold '-73'
option dtim_period '3'
option disassoc_low_ack '0'
option key '75941771tv'
option time_advertisement '2'
option time_zone 'EET-2EEST,M3.5.0/3,M10.5.0/4'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '1'
option bss_transition '1'
option proxy_arp '1'
option network 'lan'
root@xr500:~# cat /etc/config/dhcp
nfig/fir
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option start '51'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'random-ms7a33'
option ip '192.168.1.111'
option mac '30:9C:23:01:39:08'
ewallroot@xr500:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'WG_0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config rule
option name 'Allow-Admin'
option src 'wan'
option proto 'tcp'
option dest_port '2222 8080 9091'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
list proto 'tcp'
option src 'wan'
option src_dport '2222'
option dest_port '22'
option name 'allow_ssh'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'allow_web'
list proto 'tcp'
option src 'wan'
option src_dport '8080'
option dest_port '80'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Allow_WireGuard'
list proto 'udp'
option src 'wan'
option src_dport '51820'
option dest_ip '192.168.1.1'
option dest_port '51820'
option family 'ipv4'
config zone 'vpn'
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'zt+'
option masq '1'
config rule 'ssh'
option name 'Allow-SSH'
option src 'vpn'
option dest_port '2222'
option proto 'tcp'
option target 'ACCEPT'
option enabled '0'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Allow_ssh_zerotier'
list proto 'tcp'
option src 'vpn'
option src_dport '2222'
option dest_port '22'
option enabled '0'
config forwarding
option src 'vpn'
option dest 'lan'
So the problem is that you cannot reach the windows machine from the phone?
It is very likely to be the windows firewall. By default, it will block connections from other subnets. You need to set the firewall to allow connections from subnets other than the one currently in use (or disable the firewall entirely as a test) and it should work.
1 Like
olexiiy
February 15, 2024, 7:37am
6
I can acces to mac with Wireguard, but cant with ZeroTier.
Is able to remarke traffic from other subnet to local ?
I suspect that is a ZT config issue. I don't use ZT, so I can't help you with that.
No, they are routed protocols.
olexiiy
February 15, 2024, 7:56am
8
I changed WireGuard server IP to 192.168.1.11(lan ip 192.168.1.1)
No. The problem was not the addresses/subnet for wireguard. The wireguard subnet must not overlap with the lan subnet. Please undo your changes.
To repeat:
No changes were necessary on openwrt. The change you need to make is the windows firewall. (Not addresses). You also must undo your wireguard address changes.
olexiiy
February 15, 2024, 8:16am
10
What I have to do there?
I don’t use windows, but there should be settings in the firewall to do what I said earlier:
egc
February 15, 2024, 8:39am
12
That is wrong, Wireguard is a routed protocol so there should be three different subnets, the server, the client and WG should have different subnets.
For Windows just disable the firewall to test.Advanced Firewall (WF.msc), new incoming rule, scope, add VPN subnet to local scope.
Furthermore, although not related to your problem, WireGuard only needs a simple traffic rule to allow traffic for its server port:
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
Instead of:
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Allow_WireGuard'
list proto 'udp'
option src 'wan'
option src_dport '51820'
option dest_ip '192.168.1.1'
option dest_port '51820'
option family 'ipv4'
They should ensure that if the Windows PC is on Wi-Fi that connection is set to a private network.
olexiiy
February 15, 2024, 9:18am
14
This is not work.
But
config zone
option name 'WG'
option input 'REJECT'
option output 'REJECT'
option forward 'ACCEPT'
list device 'WG_0'
option family 'ipv4'
list network 'lan'
option masq '1'
this helps.
Delete the wg firewall zone. It is entirely wrong and probably conflicts with your lan zone.
Make sure both the wireguard and lan networks are covered by the lan firewall zone.
egc
February 15, 2024, 10:48am
17
You are really moving in the wrong direction.
I suggest you go back to your original configuration as you posted
The probable cause of your problem is your windows firewall, the solution is explained in my earlier post.
olexiiy
February 15, 2024, 10:56am
18
Do I have to configure every client ?
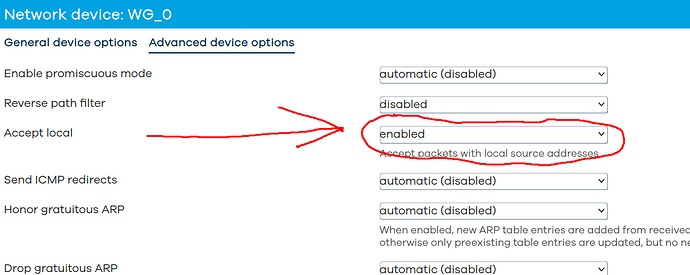
What about this setting?
egc
February 15, 2024, 1:52pm
19
You must configure the firewall on the Windows client.
See my earlier post: Wireguard and Zerotier traffic are blocked - #11 by psherman
First check if that works
There is an alternative solution, if this is the problem, you can SNAT WG server traffic out of br-lan, but you will loose logging and access restriction on your network, if your WG server clients are trusted that is not a great deal
olexiiy
February 15, 2024, 2:02pm
20
If turn off windows firewall, then pc with windows is available.
egc:
clients are trusted
My clients its me with two personal devices.
Source NAT (SNAT)