My actual scenario is:
The WireGuard client is not used as default routing and I have created policies to selectively use the WireGuard client, as instructed in stangri’s Policy-Based Routing documentation.
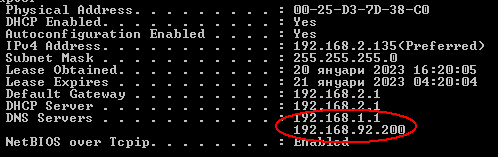
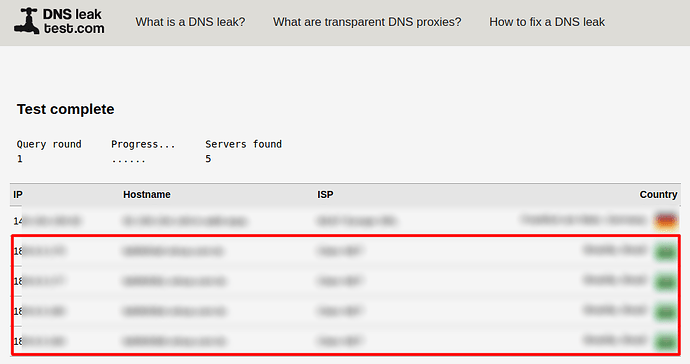
But I'm facing DNS leaks, checked on devices selectively connected to WG;
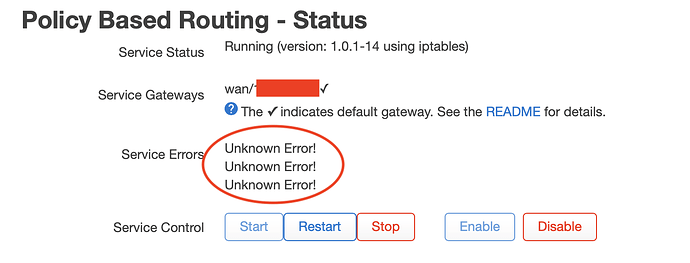
Tried the solution proposed in this post, but with no success so far.
I really would appreciate any help.
Config files info:
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '...::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'wan'
option macaddr '...'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option delegate '0'
config interface 'wg0'
option proto 'wireguard'
option private_key '...'
list addresses '.../16'
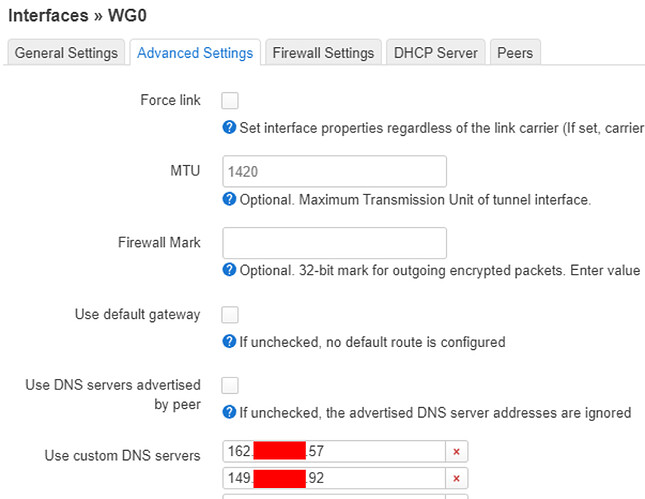
option peerdns '0'
list dns '162...57'
list dns '149...92'
option defaultroute '0'
config wireguard_wg0
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option route_allowed_ips '1'
option endpoint_host '...'
option endpoint_port '51820'
option description '...'
option public_key '...'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'iPhone1'
option dns '1'
option mac 'mac_address_iPhone1'
option ip '192.168.1.21'
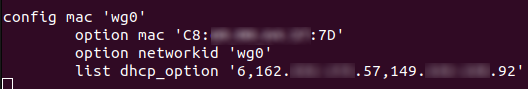
config mac 'wg0'
option mac 'mac_address_iPhone1'
option network 'wg0'
list dhcp_option '6,162...57 149...92'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'vpn'
/etc/config/pbr
config pbr 'config'
option verbosity '2'
option strict_enforcement '1'
option ipv6_enabled '0'
option boot_timeout '30'
option rule_create_option 'add'
option procd_reload_delay '1'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
option enabled '1'
list ignored_interface 'vpnserver'
list ignored_interface 'wgserver'
option webui_show_ignore_target '0'
option resolver_set 'dnsmasq.ipset'
config include
option path '/usr/share/pbr/pbr.user.aws'
config include
option path '/usr/share/pbr/pbr.user.netflix'
config policy
option name 'Ignore Local Traffic'
option interface 'ignore'
option dest_addr '192.168.200.0/24'
config policy
option name 'Plex/Emby Local Server'
option interface 'wan'
option src_port '8096 8920 32400'
option enabled '0'
config policy
option name 'Plex/Emby Remote Servers'
option interface 'wan'
option dest_addr 'plex.tv my.plexapp.com emby.media app.emby.media tv.e>
option enabled '0'
config policy
option name 'WireGuard Server'
option interface 'wan'
option src_port '51820'
option chain 'output'
option proto 'udp'
option enabled '0'
config policy
option name 'iPhone1'
option src_addr 'mac_address_iPhone1'
option interface 'wg0'
config policy
option interface 'wan'
option dest_addr 'flxvpn.net netflix.ca netflix.com netflix.com.au netf...>
option name 'Netflix Domains'
option enabled '0'