shafr
February 23, 2024, 8:57am
1
Hello there. I was using Openwrt before with my old router with a separate IOT wifi-interface & firewall zone.
However, I've switched to a TP-Link Archer AX23 v1 router with OpenWrt 23.05.2 and I'm not able to make it work - for some reason clients on IOT wifi are not getting IP addresses. (something with DHCP).
Can anyone give a hint where should I look at further ?
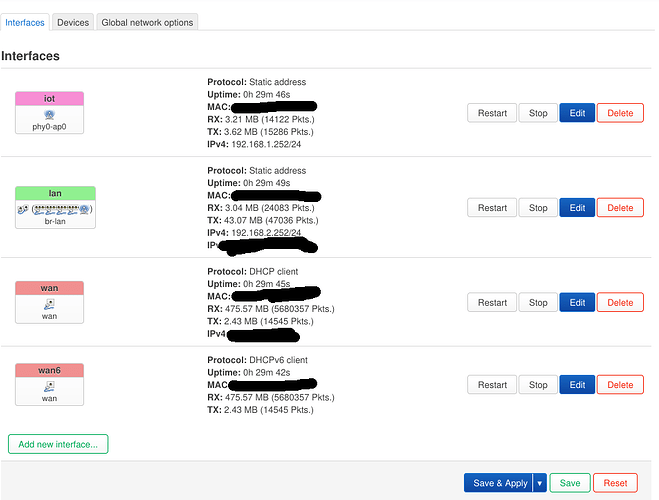
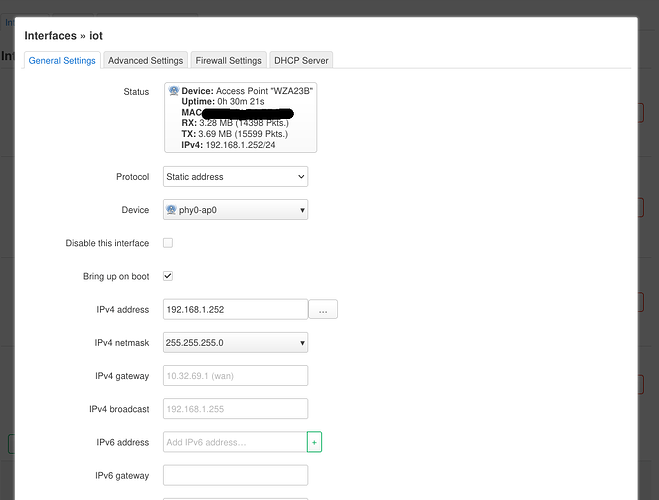
Here's how I was configuring it:
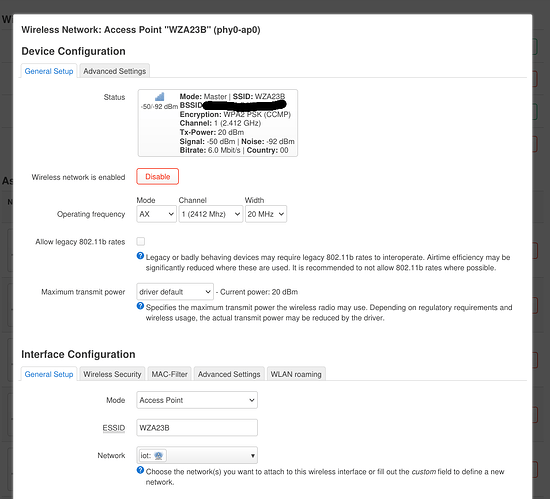
I've designated one of 2 Wireless networks for IOT = WZA23B.
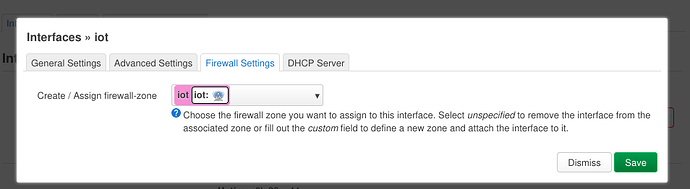
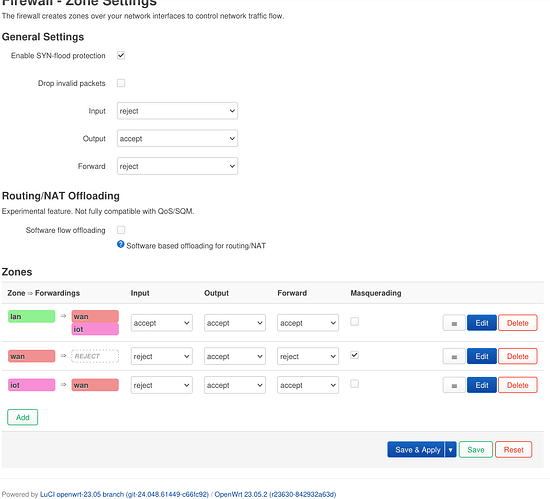
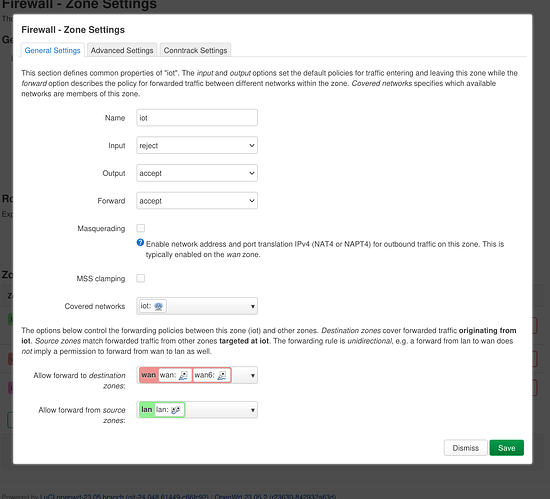
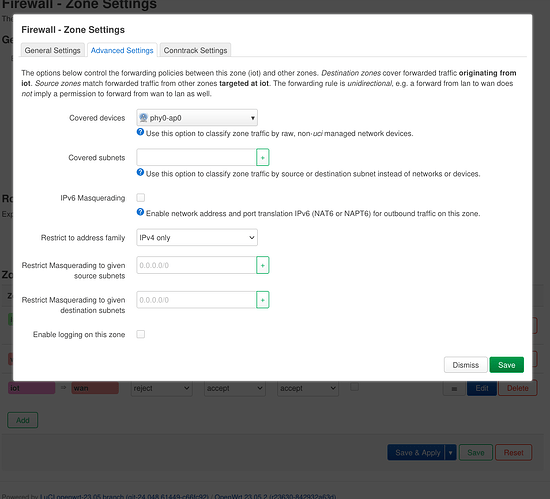
I've created firewall zone that would only work with phy0-ap0.
I've created interface for the same Device.
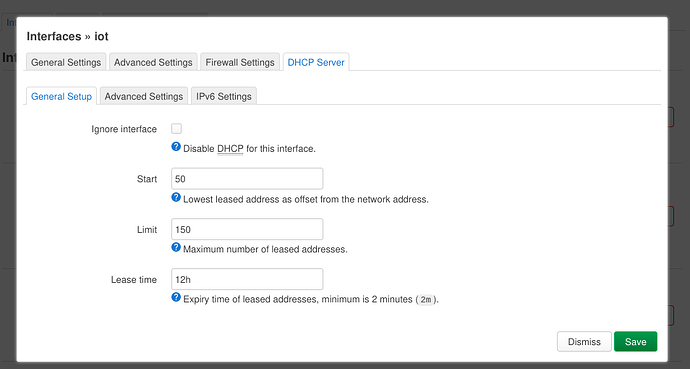
I've created DHCP & DNS routing rules.
When I'm using same "lan" firewall zone with WZA23B network, it works, but not with IOT.
I would try to add more screenshots of configuration below
trendy
February 23, 2024, 9:13am
11
shafr:
I've created firewall zone that would only work with phy0-ap0.
I've created interface for the same Device.
These 2 are not needed and possibly are the cause of the problem.phy0-ap0 from the firewall, dhcp, or interface.
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
ubus call system board; \
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
netstat -lnp | grep 67; ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
1 Like
shafr
February 23, 2024, 12:30pm
12
trendy:
Thank you for helping out.
If I look in the connection logs from linux machine:
37769.204599] wlp1s0: send auth to <redacted> (try 1/3)
[437769.206631] wlp1s0: authenticated
[437769.208599] wlp1s0: associate with <redacted> (try 1/3)
[437769.210890] wlp1s0: RX AssocResp from <redacted> (capab=0x31 status=0 aid=24)
[437769.212221] wlp1s0: associated
[437773.135809] wlp1s0: deauthenticating from <redacted> by local choice (Reason: 3=DEAUTH_LEAVING)
Here's a configuration that you've asked for:
ubus call system board; \
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
netstat -lnp | grep 67; ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
{
"kernel": "5.15.137",
"hostname": "TpLink6",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "TP-Link Archer AX23 v1",
"board_name": "tplink,archer-ax23-v1",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '<redacted>'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.0.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'iot'
option proto 'static'
option device 'phy0-ap0'
option ipaddr '192.168.1.252'
option netmask '255.255.255.0'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '1'
option band '2g'
option htmode 'HE20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'WZA23B'
option encryption 'psk2'
option key '<redacted>'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0+1'
option channel '36'
option band '5g'
option htmode 'HE80'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'WZA25B'
option encryption 'psk2'
option key '<redacted>'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
-------------------------
package firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'iot'
option input 'REJECT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'iot'
config forwarding
option src 'iot'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'iot'
udp 0 0 0.0.0.0:67 0.0.0.0:* 5534/dnsmasq
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
3: wan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
inet <redacted>/24 brd <redacted> scope global wan
valid_lft forever preferred_lft forever
10: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/16 brd 192.168.255.255 scope global br-lan
valid_lft forever preferred_lft forever
default via 10.32.69.1 dev wan src <redacted>
<redacted>/24 dev wan scope link src <redacted>
192.168.0.0/16 dev br-lan scope link src 192.168.1.1
local <redacted> dev wan table local scope host src <redacted>
broadcast 10.32.69.255 dev wan table local scope link src <redacted>
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.255.255 dev br-lan table local scope link src 192.168.1.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
trendy
February 23, 2024, 1:14pm
13
lan and iot networks are overlapping. Change lan subnet mask to 255.255.255.0 and iot address to 192.168.2.252
This is still here.
This is not assigned to any network, should be in iot.
There is no DHCP section for iot, so DHCP is not running there.guide for guest . Simply change the name from guest to iot and adapt the SSID name and pass.
1 Like
shafr
August 13, 2024, 7:39am
14
So much time had passed.
1 Like
system
August 23, 2024, 7:40am
15
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.