[EDITED on 2021/10/19 21h00 to reflect comments I got]
So I was trying to repurpose my old router Archer C7v2 in a WAP having two different SSIDs: one for safe clients and one for guests. The two SSIDS were to be on two different subnets while the DHCP, firewalling and QoS is handled by upstream pfSense.
I found some info in the documentation and the forum but most of the guys in the forum dropped the ball before marking the thread as solved.
All was done in LuCi.
Prerequisite
If you want to understand why you do these steps, I would recommend that you read these pages. If you just want it working, just follow the steps.
- Network basics
- Bridge VLAN filtering
- TP-Link Archer C7 specific page
- Wireless Acces Point / Dumb Acces Point
Port mapping
I said that all is done in LuCi. That's true. But if later one is to go in CLI, knowing the port mapping is mandatory to avoid going in circles because logical ports and physical ports are not the same.
This is taken from the TP-Link Archer C7 specific page.
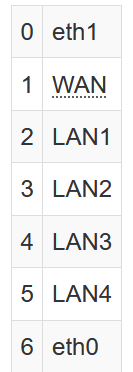
One may notice that the WAN port is labeled "1" whereas it's the 6th column to show in LuCI while one of the two cores is labeled as "6" while it is the 2nd column in LuCi.
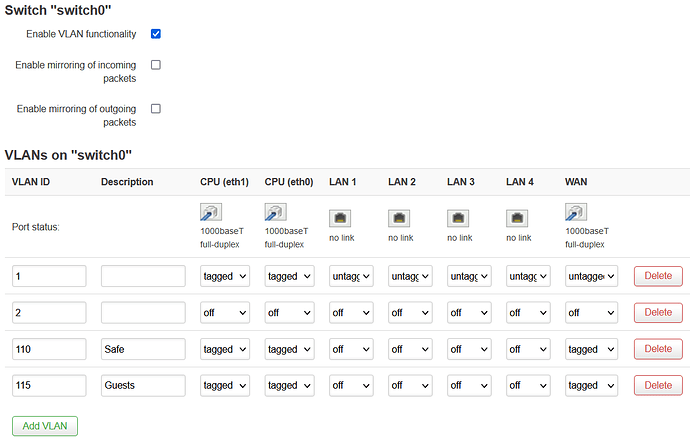
Configuring the VLANs on the switch
Now because I set this as an WAP only, I decided to use the WAN port as my uplink to the router so that's the one that is tagged for trunking all the traffic
By default, the LAN ports are on CPU(eth1) while the WAN port is on CPU(eth0). As it's used as a dumb switch, all ports are linked together and the traffic is processed by both cores.
The VLAN 2 could have been deleted alltogether.
As for me, the VLAN IDs are 110 = Safe device and 115 = Guests, but you set according to fit with your router that is handling the DHCP.
In the top menu, select /Network/Switch and set these:
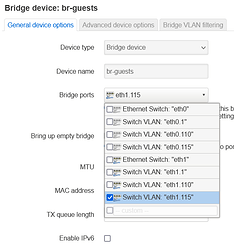
Creating the bridges
In the top menu, select /Network/Interfaces and from there, the /Devices tab.
- At the bottom of the page, choose Add device configuration.
- At "Device type"; choose Bridge device
- At "Device-name"; type an br-xxxx like br-safe or br-unsafe or br-wifi or br-guests;
- At "Bridge-ports", select the Switch VLAN "eth1.xxx" corresponding to the bridge you are creating. i.e. my unsafe Wifi is on VLAN 115 so I select eth1.115;
- Unless you are using it, uncheck "Enable IPv6"
- Click "Save"
- Repeat and create another bridge for your other VLAN accordingly.
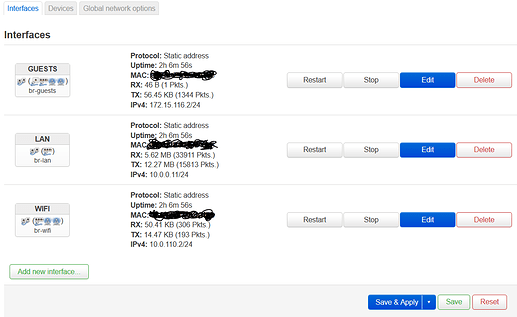
Creating the interfaces
In the top menu, select /Network/Interfaces and stay on the Interfaces tab.
- If you have not already, delete the WAN and WAN6 interfaces;
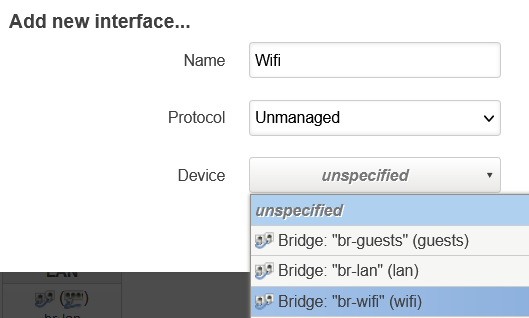
- At the bottom of the page, click on Add new interface;
- Assign a name to describe this subnet i.e. Wifi, Guests, Unsafe, Private...
- In Protocol, choose Unmanaged
- In Device, select the bridge corresponding to this interface
- Click Create interface
If you want to correlate this to the configuration in /etc/config/network, it looks like:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd54:7407:331c::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.0.0.11'
option gateway '10.0.0.1'
list dns '10.0.0.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1 2 3 4 5 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '110'
option pvid '110'
option ports '0t 1t 6t'
option description 'Safe'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '115'
option pvid '115'
option ports '0t 1t 6t'
option description 'Unsafe'
config device
option type 'bridge'
option name 'br-wifi'
option ipv6 '0'
list ports 'eth1.110'
config interface 'wifi'
option device 'br-wifi'
option proto 'none'
config device
option type 'bridge'
option name 'br-guests'
option ipv6 '0'
list ports 'eth1.115'
config interface 'guests'
option proto 'none'
option device 'br-guests'
config device
option name 'eth1.110'
option type '8021q'
option ifname 'eth1'
option vid '110'
option ipv6 '0'
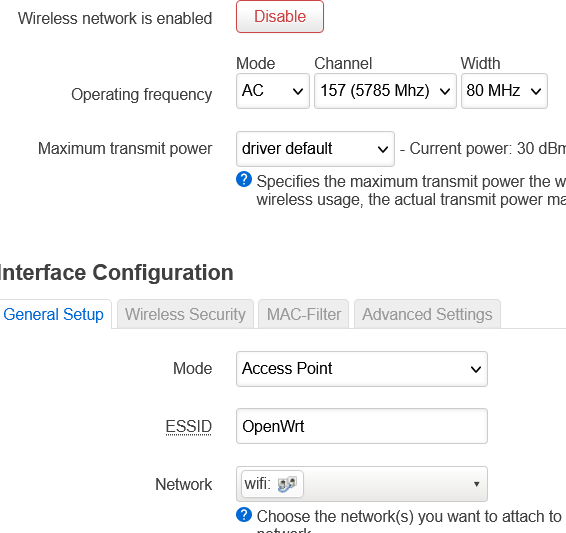
Linking the radios to the related interfaces
Now it you are using both 2.4GHz and 5GHz and you have one subnet for private devices and one subnet for guests devices, you will need 4 SSIDs. Here, I will just show onne radio.
In the top menu, select /Network/Wireless
- For one of the SSIDs, click Edit ;
- In Network, select the interface corresponding to this SSID.
- click Save
- Repeat for all the SSIDs.
- click Save & Apply
That's it
Thanks to @trendy and @mk24 for helping me in my "rookieness"