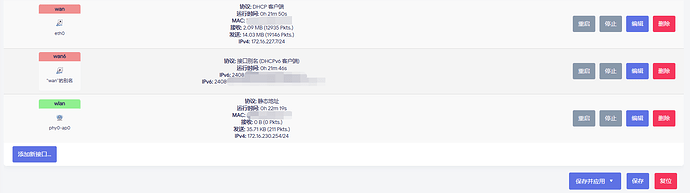
I am using Raspberry Pi 4 Model B to install openwrt. It has only one network port. This is an arm-based hardware and system!
Its upper layer is an x86-based openwrt, which performs pppoe dial-up and obtains an ipv4 and ipv6 public network address, and all devices in x86 openwrt can obtain a public ipv6 address.
I tried to connect my Raspberry Pi to the x86 device, and my Raspberry Pi obtained an intranet ipv4 address and a public ipv6 address assigned by x86, which is good, but my Raspberry Pi's phy0-ap0 did not get a public ipv6 address as I expected. I don't know why this is happening. I am about to collapse. It has consumed too much of my time and I still haven't found the reason, but I am eager to solve this damn problem!
This is my network topology diagram:
Please post as a formatted text </> output of:
ubus call system board
cat /etc/config/nrwork
cat /etc/config/dhcp
cat /etc/config/firewall
from your router.
1 Like
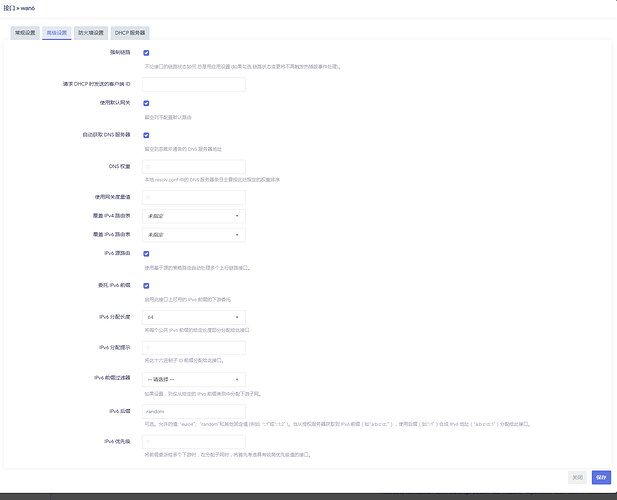
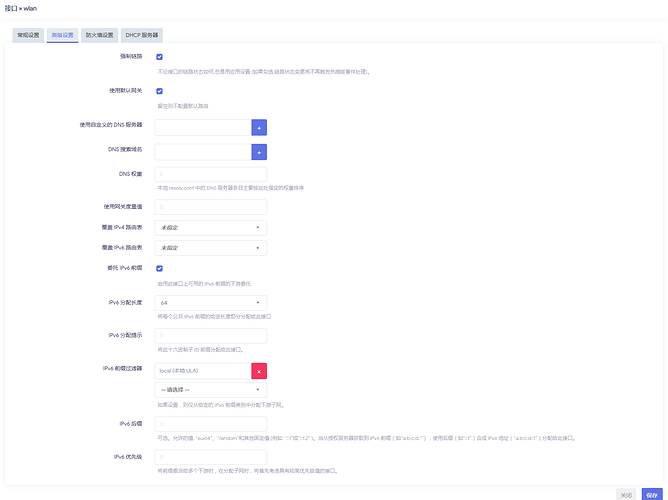
The list ipv6class local prevents other classes such as wan6 being assigned. Remove that. Also delegate_prefix means nothing if the interface is only going to hold a /64 since it can't be further delegated. That setting is if you had another router downstream.
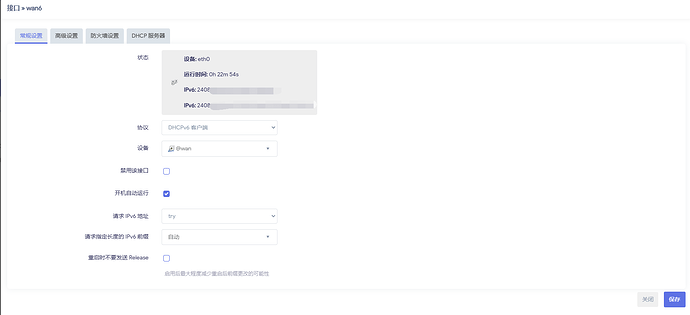
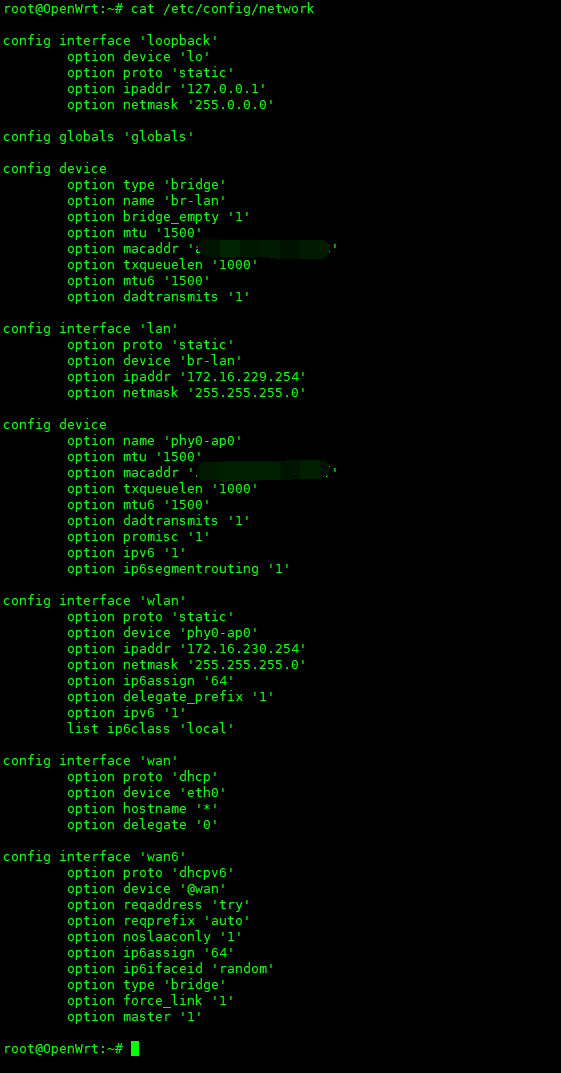
Let me show you the current configuration.
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config device
option name 'phy0-ap0'
option mtu '1500'
option macaddr 'a1:d5:dc:aa:b2:df'
option txqueuelen '1000'
option mtu6 '1500'
option promisc '1'
option ipv6 '1'
option acceptlocal '1'
option arp_accept '1'
option ip6segmentrouting '0'
option drop_unsolicited_na '0'
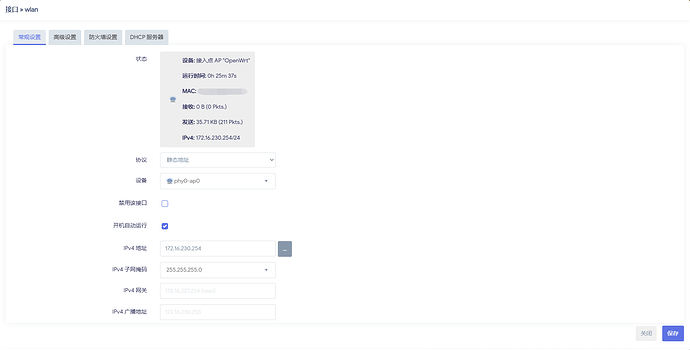
config interface 'wlan'
option proto 'static'
option device 'phy0-ap0'
option ipaddr '172.16.229.254'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6ifaceid 'random'
option defaultroute '0'
config interface 'wan'
option proto 'dhcp'
option device 'eth0'
option ipv6 '1'
config interface 'wan6'
option proto 'dhcpv6'
option device 'eth0'
option reqaddress 'try'
option reqprefix 'auto'
option ndp 'relay'
option master '1'
config device
option name 'eth0'
option promisc '1'
option acceptlocal '1'
option arp_accept '1'
option ip6segmentrouting '1'
I can't find nrwork. I think you mean network.
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.167",
"hostname": "OpenWrt",
"system": "ARMv8 Processor rev 3",
"model": "Raspberry Pi 4 Model B Rev 1.4",
"board_name": "raspberrypi,4-model-b",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.5",
"revision": "r24106-10cc5fcd00",
"target": "bcm27xx/bcm2711",
"description": "OpenWrt 23.05.5 r24106-10cc5fcd00"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config device
option name 'phy0-ap0'
option mtu '1500'
option macaddr 'a1:d5:dc:aa:b2:df'
option txqueuelen '1000'
option mtu6 '1500'
option promisc '1'
option ipv6 '1'
option acceptlocal '1'
option arp_accept '1'
option ip6segmentrouting '0'
option drop_unsolicited_na '0'
config interface 'wlan'
option proto 'static'
option device 'phy0-ap0'
option ipaddr '172.16.229.254'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6ifaceid 'random'
option defaultroute '0'
config interface 'wan'
option proto 'dhcp'
option device 'eth0'
option ipv6 '1'
config interface 'wan6'
option proto 'dhcpv6'
option device 'eth0'
option reqaddress 'try'
option reqprefix 'auto'
option ndp 'relay'
option master '1'
config device
option name 'eth0'
option promisc '1'
option acceptlocal '1'
option arp_accept '1'
option ip6segmentrouting '1'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '0'
option localise_queries '1'
option rebind_protection '0'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option localuse '1'
option sequential_ip '1'
option allservers '1'
option logqueries '1'
option logdhcp '1'
option strictorder '1'
list server '127.0.0.1#35353'
option noresolv '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'wlan'
option interface 'wlan'
option start '1'
option limit '253'
option leasetime '12h'
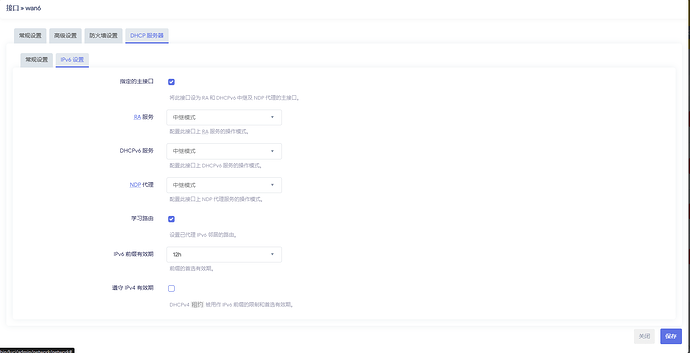
option ra 'relay'
option dhcpv6 'relay'
option ra_management '1'
option preferred_lifetime '2h'
config dhcp 'wan6'
option interface 'wan6'
option ra 'relay'
option dhcpv6 'relay'
option preferred_lifetime '2h'
option master '1'
option ignore '1'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option synflood_protect '1'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'wlan'
config zone
option name 'wan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'passwall'
option type 'script'
option path '/var/etc/passwall.include'
option reload '1'
config include 'passwall_server'
option type 'script'
option path '/var/etc/passwall_server.include'
option reload '1'
Do you mean that when there is another router downstream, in order to prevent the upstream from further delegation, only the downstream router is allowed to delegate the allocation itself? Is that what you mean?
Take away passwall rules and test again.
How does this relate to Passwall? I'm curious because it's just a VPN tool!