Hello. I have a problem with my configuration.
On my network I have :
- a routeur (a Pfsense server)
- a managed switch
- 2 OpenWrt router as "dumb AP" broadcasting the same WiFi (the same SSID and password)
I recently upgraded my 2 OpenWrt box (Xiaomi Mi Router 3G v1) from 19.07.6 to 21.02.1.
On each OpenWrt routeur, I had until the upgrade :
- a VLAN (it's VLAN 3) for my LAN, on untagged port 1 + port 2 + port "wan" + Wifi "lan"
- 2 VLANs (VLAN 50 and 99) for my IOT network and GUEST network, as tagged only on the "wan" port + Wifi "Guest" or Wifi "IOT"
My switch was configure with untagg VLAN 3 (for lan) and tagged VLAN 50 and VLAN 99 for the port my OpenWrt AP were connected.
After upgrading to 21.02.1 I had to reconfigure my VLAN with DSA.
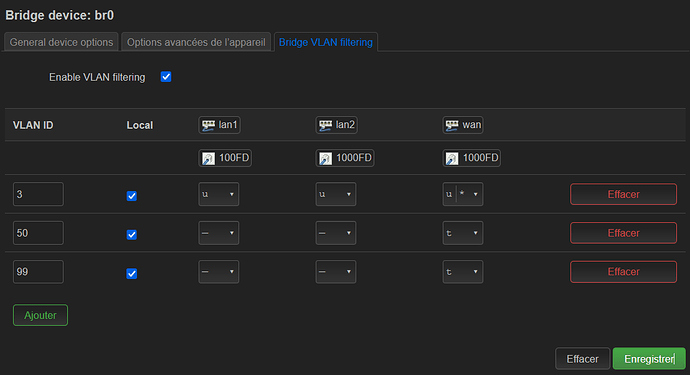
So I first tried to put the same config, by creating a bridge with all of my ports on each OpenWrt AP, and creating untagged VLAN 3 for each ports and tagged VLAN 50 and tagged VLAN 99 on the "wan" port.
I have my Wifi LAN configured as part of the LAN (with VLAN 3) network.
Here is the problem with this configuration : when I connect a WiFi client on the first AP, it works, I get an IP and connection to LAN and internet. But as soon as I connect to the second AP, I cannot get an IP anymore on the second AP and neither ont the first.
Here's the tests I have done :
-
First I thought it was a Fast transition (802.11r) problem so I disabled it, and manually disconnacted from the first AP by turning off Wifi and reconnecting to the second AP : the problem is still here, I cannot get IP from the 2nd AP, and when tring to reconnect to the first AP, I cannot get an IP adress anymore.
-
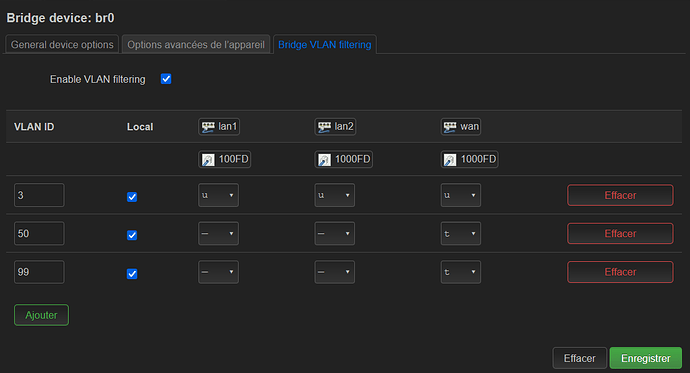
I configured my OpenWrt AP with Egress untagged with and without "PVID" for the VLAN 3 on the "wan" port
or
But the same problem is still here
So I tried to make network captures to understand when I have the problem (after disconnecting from first AP from which I obtained an IP adress and connecting to the second or reconnecting to the first) and not getting one anymore :
Each test have been done with both configuration from screen capture as shown above with the same results
- From the Wifi client Wireshark capture I see the DHCP ask (broadcast) but not response
- From my Pfsense routeur I see the DHCP client asking for an IP and I see the response and the IP sent back
- A capture on the WiFi interface from my OpenWrt I see the DHCP ask (broadcast) but not response
- A capture from the br0 interface I see the DHCP ask (broadcast) but not response
- A capture from the br0.3 (VLAN 3 on the bridge) interface I see the DHCP ask (broadcast) but not response
- A capture from the "wan" interface (from the wan port on which the OpenWrt AP is connacted to the switch) I see the DHCP ask (broadcast) but not response
- I did a port miroring on my central switch from the port on which is connacted my OpenWrt AP to an other port and did a capture of this miroring : I see the DHCP client asking for an IP and I see the response and the IP sent back
So to conclude with both of the confiuration (screen capture) : DHCP asks goes from my client, to the AP, to the Pfsense router, there is a response made, that passes my main switch to the AP but the OpenWrt doesn't see (and doesn't give it to the client) the DHCP response.
But I saw on the ifconfig command that the number of packet on "eth0" interface (I believe this is the CPU swich of my OpenWrt AP on which every ports are connected) was much higher than on "br0"+"wifi".
So I did a packet capture one "eth0" : I saw tons of "broken" LLC packets.
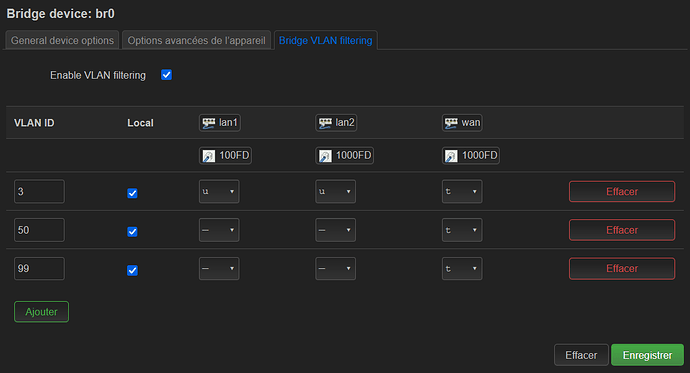
The last thing I did was to put every VLAN on tagged on the OpenWrt AP :
And to tagg every VLAN on my central switch for the port on which the OpenWrt AP is connected.
With this config everything works as expected, I get IP and the amount of packet on "eth0"="br0"+"wifis".
So is this me that didn't understood the way DSA VLAN are supposed to work for untagged VLAN on OpenWrt or is there a bug for untagged VLAN on my OpenWrt routers ?
Thanks and sorry for long post