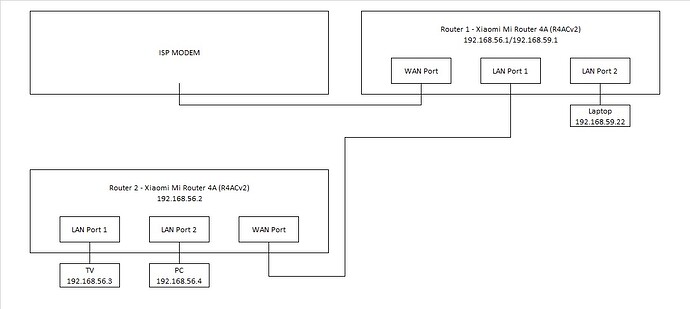
I have the following setup.
and these are the config files of router 1
/etc/config/network
config globals 'globals'
option ula_prefix 'fde3:1af6:376b::/48'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
option enable '1'
config switch_vlan
option device 'switch0'
option ports '6t 4 2'
option vlan '99'
config switch_vlan
option device 'switch0'
option ports '6t 0t'
option vlan '11'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'eth0.1'
option type '8021q'
option ifname 'eth0'
option vid '1'
option ipv6 '0'
config device
option name 'eth0.2'
option type '8021q'
option ifname 'eth0'
option vid '11'
option ipv6 '0'
config device
option name 'br-lan'
option type 'bridge'
option ipv6 '0'
list ports 'eth0.11'
list ports 'eth0.99'
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config device
option name 'phy0-ap0'
option ipv6 '0'
option mtu '1500'
config device
option name 'phy1-ap0'
option ipv6 '0'
option mtu '1500'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.56.2'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.56.1'
config device
option name 'eth0.11'
option type '8021q'
option ifname 'eth0'
option vid '11'
option ipv6 '0'
config device
option name 'eth0.99'
option type '8021q'
option ifname 'eth0'
option vid '99'
option ipv6 '0'
and /etc/config/firewall
config defaults
option syn_flood 1
option input REJECT
option output ACCEPT
option forward REJECT
# Uncomment this line to disable ipv6 rules
# option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://github.com/openwrt/openwrt/issues/5066
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
These are the config files of router 2
/etc/config/network
config globals 'globals'
option ula_prefix 'fde3:1af6:376b::/48'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'eth0.1'
option type '8021q'
option ifname 'eth0'
option ipv6 '0'
config device
option name 'eth0.2'
option type '8021q'
option ifname 'eth0'
option ipv6 '0'
option vid '2'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.99'
option ipv6 '0'
config device
option name 'phy0-ap0'
option ipv6 '0'
option mtu '1500'
config device
option name 'phy1-ap0'
option ipv6 '0'
option mtu '1500'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
option enable '1'
config switch_vlan
option device 'switch0'
option ports '6t 2t'
option vlan '69'
option description 'CAM/NVR/LIFT'
config switch_vlan
option device 'switch0'
option vlan '7'
option ports '6t 2t'
option description 'APT07'
config switch_vlan
option device 'switch0'
option vlan '8'
option ports '6t 2t'
option description 'APT08'
config switch_vlan
option device 'switch0'
option vlan '9'
option ports '6t 2t'
option description 'APT09'
config switch_vlan
option device 'switch0'
option vlan '10'
option ports '6t 2t'
option description 'APT10'
config switch_vlan
option device 'switch0'
option vlan '11'
option ports '6t 2'
option description 'APT11'
config switch_vlan
option device 'switch0'
option vlan '12'
option ports '6t 2t'
option description 'APT12'
config switch_vlan
option device 'switch0'
option ports '6t 2t'
option vlan '13'
option description 'APT13'
config switch_vlan
option device 'switch0'
option ports '6t 0'
option vlan '53'
option description 'wan'
config switch_vlan
option device 'switch0'
option ports '6t 4'
option vlan '99'
option description 'temp'
config interface 'PRIVATE'
option proto 'static'
option device 'eth0.69'
option ipaddr '192.168.50.1'
option netmask '255.255.255.0'
config interface 'APT07'
option proto 'static'
option device 'eth0.7'
option ipaddr '192.168.52.1'
option netmask '255.255.255.0'
config interface 'APT08'
option proto 'static'
option device 'eth0.8'
option ipaddr '192.168.53.1'
option netmask '255.255.255.0'
config interface 'APT09'
option proto 'static'
option device 'eth0.9'
option ipaddr '192.168.54.1'
option netmask '255.255.255.0'
config interface 'APT10'
option proto 'static'
option device 'eth0.10'
option ipaddr '192.168.55.1'
option netmask '255.255.255.0'
config interface 'APT11'
option proto 'static'
option device 'eth0.11'
option ipaddr '192.168.56.1'
option netmask '255.255.255.0'
config interface 'APT12'
option proto 'static'
option device 'eth0.12'
option ipaddr '192.168.57.1'
option netmask '255.255.255.0'
config interface 'APT13'
option proto 'static'
option device 'eth0.13'
option ipaddr '192.168.58.1'
option netmask '255.255.255.0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.59.1'
option netmask '255.255.255.0'
config interface 'wan'
option proto 'dhcp'
option device 'eth0.53'
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config device
option name 'eth0.7'
option type '8021q'
option ifname 'eth0'
option vid '7'
option ipv6 '0'
config device
option name 'eth0.8'
option type '8021q'
option ifname 'eth0'
option vid '8'
option ipv6 '0'
config device
option name 'eth0.9'
option type '8021q'
option ifname 'eth0'
option vid '9'
option ipv6 '0'
config device
option name 'eth0.10'
option type '8021q'
option ifname 'eth0'
option vid '10'
option ipv6 '0'
config device
option name 'eth0.11'
option type '8021q'
option ifname 'eth0'
option vid '11'
option ipv6 '0'
config device
option name 'eth0.12'
option type '8021q'
option ifname 'eth0'
option vid '12'
option ipv6 '0'
config device
option name 'eth0.13'
option type '8021q'
option ifname 'eth0'
option vid '13'
option ipv6 '0'
config device
option name 'eth0.53'
option type '8021q'
option ifname 'eth0'
option vid '53'
option ipv6 '0'
config device
option name 'eth0.69'
option type '8021q'
option ifname 'eth0'
option vid '69'
option ipv6 '0'
config device
option name 'eth0.99'
option type '8021q'
option ifname 'eth0'
option vid '99'
option ipv6 '0'
and /etc/config/firewall
config defaults
option syn_flood '1'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'APT07'
list network 'APT08'
list network 'APT09'
list network 'APT10'
list network 'APT11'
list network 'APT12'
list network 'APT13'
list network 'PRIVATE'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
I am testing VLAN11 at this stage. If router 2 has port 0 tagged and router 1 has port 2 untagged, I can still ping router 2 and the PC on router 2 from the laptop on router 1.
Shouldn't untagging break the trunk and not let traffic through?