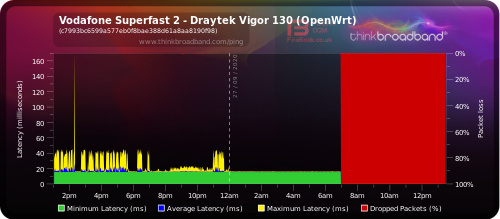
I'm using a ping monitor from thinkbroadband.com. I have the default WAN ping firewall rule enabled covering the WAN zone, which my WAN interfaces are all attached to. I've noticed that after a while my router seems to stop replying to the ping requests on a specific WAN interface in question (pppoe-wanb). This is evident by the graph data
Using tcpdump and filtering ICMP, I can see the echo request packets on the interface. However, no replies are being sent.
pingbox1.thinkbroadband.com is 80.249.99.164.
# tcpdump -i pppoe-wanb src 80.249.99.164
11:17:25.049399 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35938, length 8
11:17:26.049574 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35939, length 8
11:17:27.049500 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35940, length 8
11:17:28.050097 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35941, length 8
11:17:29.049572 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35942, length 8
11:17:30.049467 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35943, length 8
11:17:31.049621 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35944, length 8
11:17:32.049539 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35945, length 8
11:17:33.049502 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35946, length 8
11:17:34.049656 IP pingbox1.thinkbroadband.com > static-87-xx-xx-xx.vodafonexdsl.co.uk: ICMP echo request, id 32865, seq 35947, length 8
As I have multiple WAN interfaces, I have the same monitor on a different WAN eth1.2 (although on the same router) which is working fine. However I suddenly spotted that the echo reply packets for me pppoe-wanb interface are going over eth1.2, looking at tcpdump:
cpc1-xxxxxxx-x-x-xxxxxxx.xx-x.cable.virginm.net - Reverse DNS for my WAN IP
# tcpdump -i eth1.2 icmp
11:22:00.050067 IP static-87-xx-xx-xx.vodafonexdsl.co.uk > pingbox1.thinkbroadband.com: ICMP echo reply, id 32865, seq 35957, length 8
11:22:00.242345 IP pingbox1.thinkbroadband.com > cpc1-xxxxxxx-x-x-xxxxxxx.xx-x.cable.virginm.net: ICMP echo request, id 32834, seq 40106, length 8
11:22:00.242453 IP cpc1-xxxxxxx-x-x-xxxxxxx.xx-x.cable.virginm.net > pingbox1.thinkbroadband.com: ICMP echo reply, id 32834, seq 40106, length 8
11:22:01.049995 IP static-87-xx-xx-xx.vodafonexdsl.co.uk > pingbox1.thinkbroadband.com: ICMP echo reply, id 32865, seq 35958, length 8
11:22:01.242320 IP pingbox1.thinkbroadband.com > cpc1-mapp13-2-0-cust242.12-4.cable.virginm.net: ICMP echo request, id 32834, seq 40107, length 8
11:22:01.242380 IP cpc1-xxxxxxx-x-x-xxxxxxx.xx-x.cable.virginm.net > pingbox1.thinkbroadband.com: ICMP echo reply, id 32834, seq 40107, length 8
11:22:02.049907 IP static-87-xx-xx-xx.vodafonexdsl.co.uk > pingbox1.thinkbroadband.com: ICMP echo reply, id 32865, seq 35959, length 8
I can see that the echo replies for the pppoe-wanb interface, are suddenly going over this WAN. I am using mwan3, because I am multihomed, but what can I do to ensure the ping reply goes over the correct interface?