I am curious as well - have you been able to solve this?
The solution here is pretty simple... use the device in standard routed mode, with a wireless uplink. Configure your VPN, and then set the firewall to allow lan > vpn forwarding (optionally remove lan > wan forwarding).
Yes that is what I have currently but for some reason the LAN connection never goes through the VPN tunnel.
I suspect routes are somehow different from. class Linux setup.
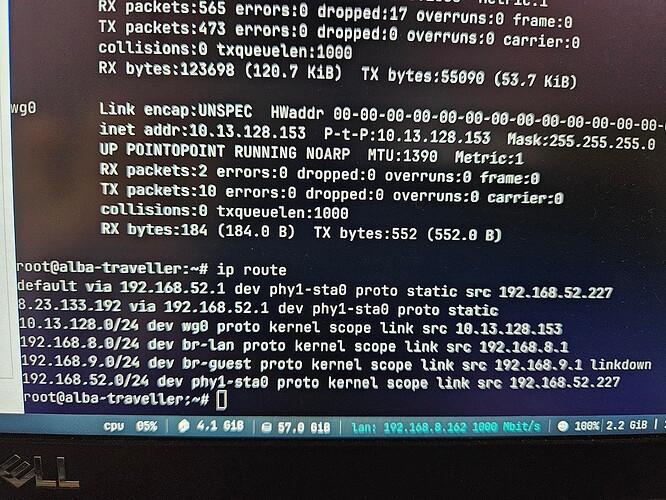
Above, 191.168.8.x is the land, the 8.* is the VPN external address. The second line is a big suspicious...but I am not an expert. Even PRT tells me that the default gateway is still the wwan.
I've taken the liberty of moving your comments to a new thread so we can keep it all tidy and focus on your specific situation.
no, not really. OpenWrt is a linux based OS. More than likely, there is a missing or misconfigured item in your overall configuration (including the firewall).
Let's take a look at your complete configuration:
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
Oh yes sounds good, it's a lot of new stuff for me (but I like to learn so please send me links in case), thanks for going over this with me.
# ubus call system board
{
"kernel": "5.15.127",
"hostname": "XXX",
"system": "ARMv8 Processor rev 4",
"model": "GL.iNet GL-MT3000",
"board_name": "glinet,gl-mt3000",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0-rc3",
"revision": "r23389-5deed175a5",
"target": "mediatek/filogic",
"description": "OpenWrt 23.05.0-rc3 r23389-5deed175a5"
}
}
# /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '??::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config device
option name 'eth1'
option macaddr 'XX:96'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.8.1'
option netmask '255.255.255.0'
option ip6assign '60'
option isolate '0'
config device
option name 'eth0'
option macaddr 'XX:95'
config interface 'tethering6'
option proto 'dhcpv6'
option disabled '1'
option device '@tethering'
config interface 'guest'
option force_link '1'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.9.1'
option netmask '255.255.255.0'
option ip6assign '60'
option multicast_querier '1'
option igmp_snooping '0'
option isolate '0'
option bridge_empty '1'
config rule 'policy_bypass_vpn'
option mark '0x60000/0x60000'
option lookup '53'
option priority '53'
config rule 'policy_via_vpn'
option mark '0x80000/0x80000'
option lookup '52'
option priority '52'
config rule 'policy_dns'
option mark '0x100000/0x100000'
option lookup '51'
option priority '51'
config interface 'wwan'
option proto 'dhcp'
config interface 'wg0'
option proto 'wireguard'
option private_key 'FOO'
option listen_port '53425'
list addresses '10.13.BAR/24'
option mtu '1390'
list dns '9.9.9.9'
list dns '149.112.112.112'
config wireguard_wg0
option description 'Imported peer configuration'
option public_key 'QUUZ'
list allowed_ips '0.0.0.0/0'
option persistent_keepalive '25'
option endpoint_host '8.23.133.192'
option endpoint_port '1443'
# /etc/config/wireless
config wifi-device 'mt798111'
option type 'mtk'
option band '2g'
option htmode 'HE40'
option channel 'auto'
option txpower '100'
option country 'DE'
option disabled '0'
option legacy_rates '0'
config wifi-device 'mt798112'
option type 'mtk'
option band '5g'
option channel 'auto'
option htmode 'HE80'
option txpower '100'
option country 'DE'
option disabled '0'
option legacy_rates '0'
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/18000000.wifi'
option channel 'auto'
option band '2g'
option htmode 'HE40'
option cell_density '0'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/18000000.wifi+1'
option channel '149'
option band '5g'
option htmode 'HE40'
option cell_density '0'
config wifi-iface 'wifinet0'
option device 'radio1'
option mode 'sta'
option network 'wwan'
option ssid 'SSID 5G'
option encryption 'psk2'
option key 'PASS'
# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option rebind_protection '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '24h'
option dhcpv4 'server'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config domain
option name 'console.gl-inet.com'
option ip '192.168.8.1'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'disabled'
option ra 'disabled'
config domain
option name 'my-router'
option ip '192.168.52.1'
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'tethering6'
list network 'wwan'
option masq '1'
config include
option path '/etc/firewall.user'
config include 'nat6'
option path '/etc/firewall.nat6'
option reload '1'
config rule 'process_mark'
option name 'process_mark'
option dest '*'
option proto 'all'
option extra '-m owner --gid-owner 65533'
option target 'MARK'
option set_xmark '0x80000/0x80000'
config rule 'lan_in_conn_mark_restore'
option name 'lan_in_conn_mark_restore'
option src 'lan'
option dest '*'
option set_xmark '0x80000/0x80000'
option target 'MARK'
option extra '-m connmark --mark 0x80000/0x80000 -j CONNMARK --restore-mark'
option enabled '0'
config rule 'out_conn_mark_restore'
option name 'out_conn_mark_restore'
option dest '*'
option set_xmark '0x80000/0x80000'
option target 'MARK'
option extra '-m connmark --mark 0x80000/0x80000 -j CONNMARK --restore-mark'
option enabled '0'
config include 'swap_wan_in_conn_mark'
option type 'script'
option reload '1'
option enabled '0'
option path '/etc/firewall.swap_wan_in_conn_mark.sh'
config rule 'block_dns'
option name 'block_dns'
option src '*'
option device 'br-+'
option dest_port '53'
option target 'REJECT'
option enabled '0'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glblock'
option type 'script'
option path '/usr/bin/gl_block.sh'
option reload '1'
config zone
option name 'guest'
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
list network 'guest'
config rule
option name 'Allow-DHCP'
option src 'guest'
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
config rule
option name 'Allow-DNS'
option src 'guest'
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
config include 'vpn_server_policy'
option type 'script'
option path '/etc/firewall.vpn_server_policy.sh'
option reload '1'
option enabled '1'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config zone
option name 'vpn'
option input 'DROP'
option output 'DROP'
option forward 'DROP'
option mtu_fix '1'
option masq '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'wan'
Looks like you're using a GL-inet device with their firmware installed.
Which specific device are you using?
ubus call system board
If you want to continue to use the gl-inet firmware and/or if your device is unable to run the official OpenWrt firmware, you'll need to ask in the gl-inet forums because of the extent of the changes gl-inet makes to their firmware (relative to pure OpenWrt). But, we can help you determine if your device can run official OpenWrt.
@psherman Well yes I am using one of their boards but I flashed the latest Openwrt release candidate
# ubus call system board
{
"kernel": "5.15.127",
"hostname": "XX",
"system": "ARMv8 Processor rev 4",
"model": "GL.iNet GL-MT3000",
"board_name": "glinet,gl-mt3000",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0-rc3",
"revision": "r23389-5deed175a5",
"target": "mediatek/filogic",
"description": "OpenWrt 23.05.0-rc3 r23389-5deed175a5"
}
}
Maybe that's the problem?
Did you keep settings across the upgrade? Did the rc3 upgrade come from the openwrt.org site?
Yes I kept the settings and yes I downloaded the firmware from the official firmware selector. I did not have any customization before - I opened the package and flashed the firmware.
You should not keep settings across an upgrade to/from vendor firmware.
You need to reset your device to defaults and then configure again from scratch - the gl-inet config files are not compatible with official openwrt.
Ok I'll do that and get back to you.
Ok I reconfigured - this is the configuration that does not work with LAN -> VPN firewall rule.
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd86:7143:ba51::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
config interface 'wwan'
option proto 'dhcp'
option ipaddr '192.168.52.251'
option netmask '255.255.255.0'
option gateway '192.168.52.1'
config interface 'wg0'
option proto 'wireguard'
option private_key '+FOO+'
option listen_port '60333'
list addresses '10.13.128.153/24'
list dns '10.8.0.1'
option mtu '1390'
option force_link '1'
config wireguard_wg0
option description 'Imported peer configuration'
option public_key '+BAR+'
list allowed_ips '0.0.0.0/0'
option persistent_keepalive '25'
option endpoint_host '8.23.133.192'
option endpoint_port '1443'
# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/18000000.wifi'
option channel '1'
option band '2g'
option htmode 'HE20'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/18000000.wifi+1'
option channel '36'
option band '5g'
option htmode 'HE40'
option cell_density '0'
config wifi-iface 'wifinet2'
option device 'radio1'
option mode 'sta'
option network 'wwan'
option ssid 'FOO 5G'
option encryption 'psk2'
option key 'XYZ'
# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'vpn'
You need to enable the “route allowed ips” option in the wg peer stanza. Then restart your wg interface and see if that fixes the issue.
That worked! Marked as solution, big thank yous ![]()
Is it worth contributing this to the wiki? It is quite a small thing to change!
It's already there...
Oh I see, yeah that would probably need a gigantic "IMPORTANT" close to it or something. Easy to miss I am glad we have this entry in the forum now.
Well, almost of the lines in that section are critical... there are only a few optional lines. In general, though, you can simply copy/paste the entire section, rather than line-by-line.
I am now fighting withd avoiding routing traffic into the local Lan to the VPN, do you have any recommendation for that?
I am trying the pbr package but it is not very beginner friendly. Learning a lot though😃
I'm not sure what you mean... traffic between devices on your own network(s) will not traverse the tunnel, unless you are talking about between your VPN router and the wireless uplink (i.e. if your wifi uplink is the trusted lan of your main network)?