Got a network/routing problem that is stumping me at the moment:
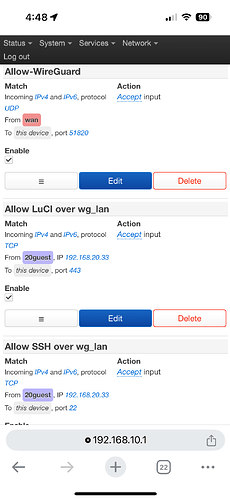
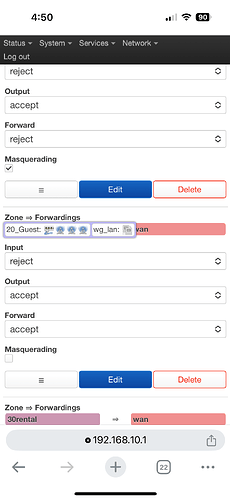
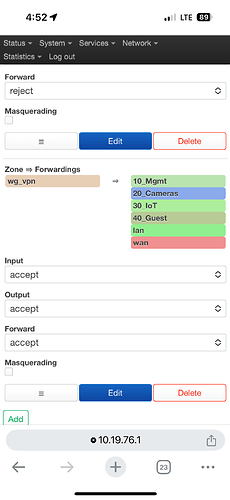
I have at home (Site A) a wan-zone interface that I use to policy route through (Site B). The other endpoint (Site B) has the vpn interface in a firewall zone set input/output/forward as reject/accept/accept. That fw zone has the vpn interface, and the bridge interface for the network I’m connected to. The tunnel allows me to route through the remote endpoint(A > B = go), but the remote endpoint can’t access my home (B > A = no-go).
Now I’m physically at that remote endpoint (Site B), and connecting my vpn profile on my phone can’t connect to my home. Turn off Wi-Fi and use cellular, the vpn connection handshake completes and I’m golden, so it’s something to do with the tunnel that exists between the sites.
I’ve added a route on this Site B endpoint for my home Site A subnet, as well as adding my home subnets to the allowed IPs of the peer connection. No go.
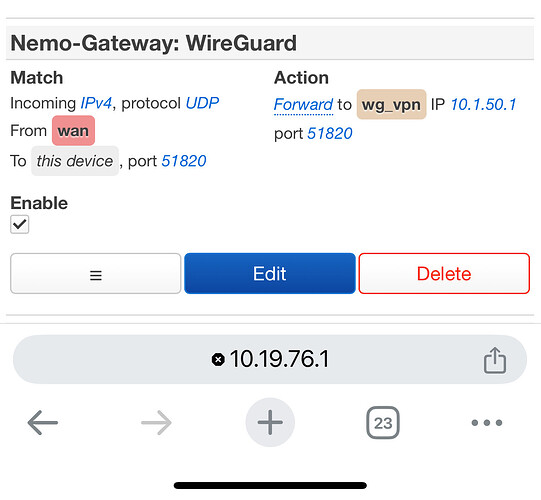
I have a fw port forward at Site A set as “from:wan zone, to: this device port 51820, forward to vpn zone:interface ip:51820”. Likewise, another device in my home network runs a wg vpn server listening on 51820, mapped to wan 51823; connecting to this vpn server also fails while connected at Site B.
I feel like it’s something obvious and simple that I’m missing. Anyone have an answer?