Yes of course. Do you believe there's an answer to my question in the examples?
Hi, couldn't find an answer in this thread or in the README so I'm asking directly. I would like to enable disable policies, same way you check/uncheck the box in luci and the click Apply, from the command line. I guess I would need to edit the relevant policy file and the reload the service, but I wonder if there's another way to do this that I'm missing.
My end goal is to enable/disable certain policies via ssh from a switch in Hassio.
Hello? Do you know how to get IP services to work on the WAN interface?
Hey stangri. You might remember I posted a little while back about my IP leaking, and I was speculating I might have a situation where the service isn't running. Turns out, I happened to catch this in the act for a change. My suspicion is this happened on bootup. Thankfully, I had added a firewall rule that is always present to keep my traffic from going out the WAN, but otherwise I'd have been sending packets out the wrong interface for a while until I noticed. Any thoughts on how to mitigate this? It doesn't seem right that the basic service should ever fail, no matter what error it gets??
thx
Have you tried playing with boot_timeout option?
No, mine is blank. Suggestion for a sane value?
I believe default value is 30 (seconds), I'd start with that.
PS. Unless your wan ip address really is a private IP, then playing with boot_timeout probably won't help you.
It is, the next hop is my VDSL modem
The service is already set to start pretty late, why it fails to create chains in the mangle table on boot, I have no idea.
You can try adding this to the init script and see if it helps:
boot() {
sleep 20
rc_procd start_service
rc_procd service_triggers
}
Did you figure it out? What was the solution?
Yes, I will try to summarize what I think was the issue. I had two policies:
- Redirect
yyy.comtowg0. (IPYYY.YYY.YYY.YYY) - Redirect
10.0.0.0/24towg0. (10.0.0.0/24is the subnet I use for Wireguard)
The TCP handshake went more or less like this:
- Local client
192.168.1.XXXsent SYN toYYY.YYY.YYY.YYY. - Router was masquerading
192.168.1.XXXwith its ownwg0IP10.0.0.ZZZ. - SYN went to the server and a SYN-ACK came back, addressed to
10.0.0.ZZZdue to masquerading. - (conjecture)
10.0.0.ZZZmatched the10.0.0.0/24rule and got sent back towg0. - Router translated
10.0.0.ZZZback to original IP,192.168.1.XXX.
As a result, using tcpdump on wg0, I was seeing both the packet (src YYY.YYY.YYY.YYY dst 10.0.0.ZZZ) AND the packet (src YYY.YYY.YYY.YYY dst 192.168.1.XXX), which was not supposed to be there.
I removed the policy for 10.0.0.0/24 and used a static route instead. As a result, everything works and I am not seeing the packet with dst 192.168.1.XXX when using tcpdump on wg0.
I am not even sure this is possible, but it seems so.
Apologies if I've missed this in the 1000+ post thread.
I'm trying to use two ISPs (no VPNs). I have a slow, expensive, business DSL (interface WAN no inbound filtering, static IPs), and a fast, cheap, consumer cablemodem (interface WAN2 inbound filtering, dynamic IPs) and I'm wanting to setup both on the same router.
responses should go out the circuit they came in on (although I may test to find out if it works without this)
by default, services should use the DSL line (interface WAN), unless the circuit is down, in which case it does no harm to try to use the cablemodem (interface WAN2)
specific services (web browsing) should go out the cablemodem (interface WAN2), unless WAN2 is down, in which case the services should go out WAN
I think I understand how to setup the rules for the specific services, but what I'm missing is how to have two different Internet connections that can route to the entire Internet. I know that having two default routes is not the answer, but I'm not sure what it.
It may be that I'm overthinking this and I just setup the default route on WAN and only things specified by the policies will go to WAN2, and they can go anywhere on the Internet without a default route out WAN2, but I'm not sure, so I wanted to ask.
With so many people working from home, the idea of having two Internet circuits, use one as the default and failover to the other if the first fails should be something that is interesting to many people.
I can write a script that checks the interface health (pinging either my ISP or an upstream service) and executes a command if the link is determined to 'not work', but I then need policy routing to allow such testing to work rather than forcing it over one of the links.
could someone help provide an example of what to do in this sort of situation (I think it would be a very valuable addition to the README)
Apologies if I missed something in the long post, but sounds like you need mwan3 package.
could be, I was under the impression that policy based routing was a better long-term option and everything I found pointed me here. I'll go look over mwan3
Whatever this requirement is, VPR doesn't actively track/mark incoming packets, hence my recommendation to check out mwan3.
Without that requirement, if the WAN2 is your default route and strict enforcement isn't enabled, VPR may work.
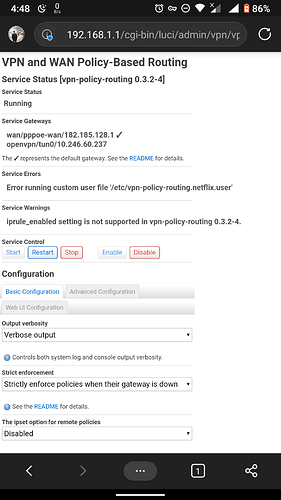
I have a strange issue where config for remote policies does not change to 'dnsmasq.ipset' in VPBR even though I changed it multiple times from LuCI and terminal. It always reverts to disabled and netflix file produces errors.
Further info:
VPBR config:
root@AhmarRouter:~# cat /etc/config/vpn-policy-routing
config vpn-policy-routing 'config'
option enabled '1'
option verbosity '2'
option strict_enforcement '1'
option src_ipset '0'
option resolver_ipset 'dnsmasq.ipset'
option ipv6_enabled '0'
option boot_timeout '1'
option iptables_rule_option 'append'
option webui_enable_column '1'
option webui_protocol_column '0'
option webui_chain_column '0'
option webui_show_ignore_target '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option iprule_enabled '0'
option dest_ipset '0'
config include
option path '/etc/vpn-policy-routing.netflix.user'
config include
option path '/etc/vpn-policy-routing.aws.user'
option enabled '0'
root@AhmarRouter:~# service vpn-policy-routing support
vpn-policy-routing 0.3.2-4 running on OpenWrt 19.07.6. WAN (IPv4): wan/dsl0.10/182.185.128.1.
============================================================
Dnsmasq version 2.80 Copyright (c) 2000-2018 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP DHCPv6 no-Lua TFTP conntrack ipset auth nettlehash DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
default 182.185.128.1 0.0.0.0 UG 0 0 0 pppoe-wan
IPv4 Table 201: default via 182.185.128.1 dev pppoe-wan
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
IPv4 Table 201 Rules:
32761:from all fwmark 0x10000/0xff0000 lookup wan
IPv4 Table 202: default via 10.246.60.237 dev tun0
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
IPv4 Table 202 Rules:
32760:from all fwmark 0x20000/0xff0000 lookup openvpn
============================================================
Mangle IP Table: PREROUTING
-N VPR_PREROUTING
-A VPR_PREROUTING -m set --match-set openvpn dst -c 0 0 -g VPR_MARK0x020000
-A VPR_PREROUTING -m set --match-set wan dst -c 0 0 -g VPR_MARK0x010000
============================================================
Mangle IP Table MARK Chain: VPR_MARK0x010000
-N VPR_MARK0x010000
-A VPR_MARK0x010000 -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_MARK0x010000 -c 0 0 -j RETURN
============================================================
Mangle IP Table MARK Chain: VPR_MARK0x020000
-N VPR_MARK0x020000
-A VPR_MARK0x020000 -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_MARK0x020000 -c 0 0 -j RETURN
============================================================
Current ipsets
create wan hash:net family inet hashsize 1024 maxelem 65536 comment
create openvpn hash:net family inet hashsize 1024 maxelem 65536 comment
============================================================
Your support details have been logged to '/var/vpn-policy-routing-support'. [✓]
For the netflix.user file you may have to run it from shell manually to see what kind of error it produces, for the settings issue, you may have to manually download the luci-app-vpn-policy-routing from https://github.com/stangri/repo.openwrt.melmac.net and force-reinstall it on your router.
There was a new luci packages version stamping introduced a while ago and now the versions I put in the makefile are irrelevant, the version gets inherited from the last commit in the OpenWrt code for the package, so opkg doesn't report a newer version in my repo.
I forced install your luci-app version and now config is working but I am still getting errors on netflix file. I allowed execution of the file with chmod +x and then executed it manually on terminal and it did not produce any errors but when I restart VPBR it shows following:
root@AhmarRouter:~# service vpn-policy-routing restart
Creating table 'wan/pppoe-wan/182.185.128.1' [✓]
Creating table 'openvpn/tun0/10.246.60.237' [✓]
Routing 'Hub' via openvpn [✓]
[✗]
vpn-policy-routing 0.3.2-4 started with gateways:
wan/pppoe-wan/182.185.128.1 [✓]
openvpn/tun0/10.246.60.237
ERROR: Error running custom user file '/etc/vpn-policy-routing.netflix.user'
vpn-policy-routing 0.3.2-4 monitoring interfaces: wan openvpn [✓]
im sorry if my english is bad but i have issue
so i was using openvpn for long time go, but the problem is i can access some web like "e-banking, ecommercie etc"
i cant access web like that from other country with "openvpn"
so can i use vpn-policy for separate traffic when i access web like that use my local isp and the other use tunnel openvpn?
how to configure it?
thanks
VPR does . /etc/vpn-policy-routing.netflix.user and reports its error code. It's an equivalent of . /etc/vpn-policy-routing.netflix.user; echo $?;.
If that returns 0 but the VPR still reports an error, I have no ideas.