Hello I'm new to operwrt. I have configured openvpn client in openwrt via ovpn file. This works well so far, but automatically connects all devices to vpn. However, I only want to connect 2 devices via vpn. I can't manage this with policy-based routing, as no rules are working for me. Tun0 is displayed as the default gateway. I have written pull-filter ignore "redirect-gateway" in the ovpn file, but then I cannot connect to the vpn at all. What options do I have to connect only 2 devices to vpn via openwrt? thx in advance
How are you trying to do it - using the pbr package or creating custom ip rules/routing tables?
Either way we'll need to see the configuration(s) before we can help.
You mean there is a connection to the vpn server but you can't access the internet through it, right?
Thx for answering. Yes, i'm trying the pbr package. I thought it was easier then rules/routing. When i write in the ovpn file the line "pull-filter ignore "redirect-gateway" i can access internet but only without vpn and in pbr default gateway switches to wan/eth0.2/192.168.1.1 (without the pull-filter ignore "redirect-gateway" i can access only trough vpn and the default gateway in pbr is vpntun/tun0/10.8.0.3). The pbr rules had no effects, neither with or without pull-filter ignore "redirect-gateway".
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdfa:16fa:457d::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
config interface 'wg0'
option proto 'wireguard'
option private_key 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx='
list addresses '10.5.0.2/32'
option defaultroute '0'
option peerdns '0'
list dns '103.86.96.100'
list dns '103.86.99.100'
option auto '0'
config wireguard_wg0
option description 'nvpn_it217.conf'
option public_key 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx ='
list allowed_ips '0.0.0.0/0'
option endpoint_host 'it217.nordvpn.com'
option endpoint_port '51820'
option persistent_keepalive '25'
config interface 'vpntun'
option proto 'none'
option peerdns '0'
list dns '103.86.96.100'
list dns '103.86.99.100'
option device 'tun0'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config forwarding
option src 'lan'
option dest 'wan'
config zone
option name 'vpnfw'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'vpntun'
list network 'wg0'
config forwarding
option src 'vpnfw'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'vpnfw'
root@OpenWrt:~# cat /etc/config/pbr
config pbr 'config'
option verbosity '2'
option strict_enforcement '1'
option ipv6_enabled '0'
list ignored_interface 'vpnserver'
list ignored_interface 'wgserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
option resolver_set 'dnsmasq.ipset'
option enabled '1'
config include
option path '/usr/share/pbr/pbr.user.aws'
option enabled '0'
config include
option path '/usr/share/pbr/pbr.user.netflix'
option enabled '0'
config policy
option name 'Plex/Emby Local Server'
option interface 'wan'
option src_port '8096 8920 32400'
option enabled '0'
config policy
option name 'Plex/Emby Remote Servers'
option interface 'wan'
option dest_addr 'plex.tv my.plexapp.com emby.media app.emby.media tv.emby.media'
option enabled '0'
config policy
option name 'xia'
option src_addr '192.168.2.162'
option interface 'vpntun'
root@OpenWrt:~# ip route
default via 192.168.1.1 dev eth0.2 proto static src 192.168.1.2
10.8.0.0/24 dev tun0 proto kernel scope link src 10.8.0.3
82.102.21.35 via 192.168.1.1 dev eth0.2 proto static
192.168.1.0/24 dev eth0.2 proto kernel scope link src 192.168.1.2
192.168.2.0/24 dev br-lan proto kernel scope link src 192.168.2.1
I’ve no experience with openVPN, but I use wireguard with pbr and it works great.
A couple of things I’ve encountered personally or seen on the forums that have caused issues -
-
Are you just using pbr? Or do you have another package like mwan3 installed? mwan3 and pbr do not play well together out of the box.
-
Have you set metrics on your wan and/or tun0 gateways? Setting a higher metric in the interface options for a gateway gives it a lower priority. Try giving your tun0 a higher metric, which should allow your wan to become the default gateway (it will be the gateway with a checkmark at the top of pbr in luci). Then you should be able to create a rule that only allows what you want to use the vpn.
Hi. Have mwan3 installed. Try to remove it. Will try to give tun0 higher metric, i dont have it set wright now.
Have wireguard to, but actually disabled. How do you set it up wireguard with pbr? To make it working wan must be the default gateway in pbr wright?
Thx man. You made my day. Uninstalled mwan3 package and now its working. Thank you so much.
Me, personally, I’ve setup 3 networks. Lan, IoT, and guest. The way I use pbr is I have rules for my lan to use wan, the IoT to use a wireguard vpn, and my guest network to use a different wireguard vpn. I’ve set my wan to a metric of ‘0’ (which I think it defaults to anyway, but just in case I manually do it), my wg vpn interface for IoT gets a metric of ‘10’, and my wireguard vpn for guest gets a metric of ‘20’. I also have a 3rd wireguard vpn that is on my lan network and that gateway gets ignored in pbr.
Fantastic! Yea, mwan3 and pbr fight over route tables as they have their own way of doing things, so having both causes many issues.
Good guess!
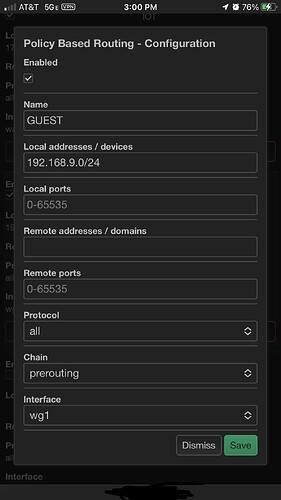
Just for interest. Can you send me a screenshot how do you use rules for using wan, so maybe i give it a try? Thx in advance.
I keep it pretty simple, by keeping everything default and just defining the address/network and the interface. Depending on your use case, you can define single ip’s, hostnames, ports, etc.
Edit: so, if for example, your lan network is 192.168.1.0/24, make that the address and the interface should be wan.
Thx. I switch over to wireguard to now. It's working like a charm now.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.