hi,
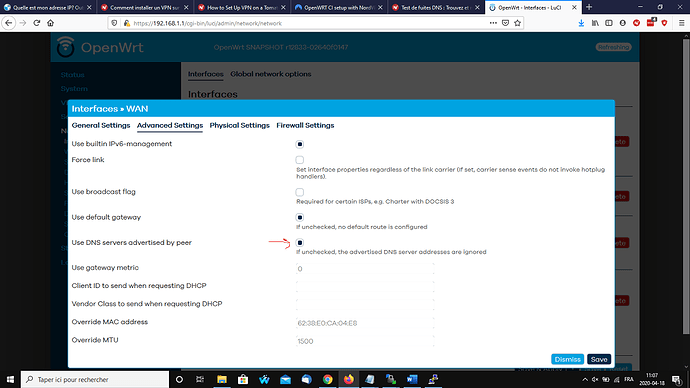
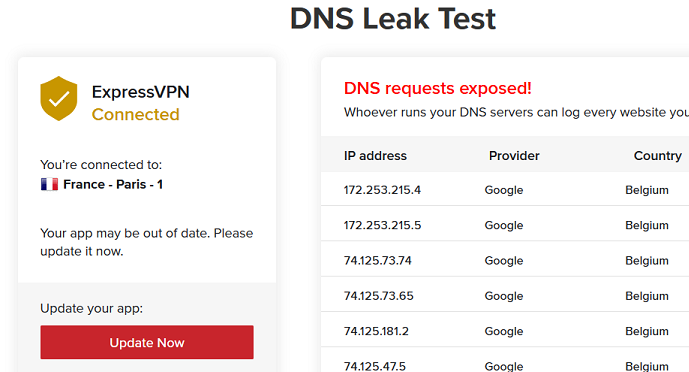
is it possible to find a solution about the vpn dns . I mean, I have express vpn and I need to have their own dns pushed instead of my isp dns or my custom dns... I dont have the esxpress vpn dns cause they are private but They seem to say that I need to choose ''use dns advertised by peer = check''. BUt for now if I tick that, I have my isp dns, if not if I use custom (google etc) I will have them. Yes I will be connected to my vpn but the dns will be my isp or the custom ones. And in that case, problem to stream netflix etc..
any idea or advices?
thanks
That setting on the wan will not help you. You’d need to override the dns on the tunnel. You could try issuing your clients the desired dns servers via dhcp (iirc, dhcp option 6 handles this) - then the client devices don’t even bother with the router for dns). Or you could make an ifup script that sets the desired dns after the tunnel is established (overriding the push).
That doesn’t look like a standard openwrt release - is it just a custom theme, or is this a 3rd party version?
hi,
yes it is davidc502 for wrt linksys serie, but except theme, everything is the same.
mk24
April 18, 2020, 3:56pm
4
Netflix is blocking you watching through the VPN because they know the IP of the expressvpn server and block it. That has nothing to do with DNS.
I found that, this is what I need to have.....
Thanks for your reply Trendy,
I suspect your question may lead to the very point we need to get down into...
To use ExpressVPN or any other vpn provider without leaks, one must direct all DNS queries through the VPN. ExpressVPN further requires that DNS servers be set to google DNS (and that local DNS from ISP be blocked via no-resolve directive etc.) This config then ensures that the vpn sever pushs/translates/or replaces only these google IPs with their own secure DNS at the correct location…
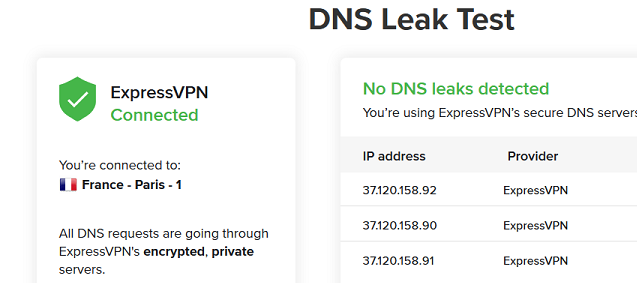
not true, express vpn is one of the best to unblock netflix. I watch netflix without any problem with my other routers, dd wrt, asus wrt with open vpn.
except open wrt.
same setup, according to me, dd wrt vs open wrt and you can see the result on the pics.
here my last setup, I restarted the configuration..
my network:
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd23:32d2:992d::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.dns='8.8.8.8' '8.8.4.4'
network.wan=interface
network.wan.ifname='eth1.2'
network.wan.proto='dhcp'
network.wan.peerdns='0'
network.wan.dns='8.8.8.8' '8.8.4.4'
network.wan6=interface
network.wan6.ifname='eth1.2'
network.wan6.proto='dhcpv6'
network.wan6.reqaddress='try'
network.wan6.reqprefix='auto'
network.wan6.peerdns='0'
network.wan6.dns='2001:4860:4860::8888' '2001:4860:4860::8844'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='0 1 2 3 5t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='4 6t'
network.vpn0=interface
network.vpn0.proto='none'
network.vpn0.ifname='tun0'
network.vpn0.metric='10'
my firewall
root@OpenWrt:~# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan wan6'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.miniupnpd=include
firewall.miniupnpd.type='script'
firewall.miniupnpd.path='/usr/share/miniupnpd/firewall.include'
firewall.miniupnpd.family='any'
firewall.miniupnpd.reload='1'
firewall.bcp38=include
firewall.bcp38.type='script'
firewall.bcp38.path='/usr/lib/bcp38/run.sh'
firewall.bcp38.family='IPv4'
firewall.bcp38.reload='1'
firewall.@zone[2]=zone
firewall.@zone[2].name='vpn0'
firewall.@zone[2].input='REJECT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='REJECT'
firewall.@zone[2].masq='1'
firewall.@zone[2].mtu_fix='1'
firewall.@zone[2].network='vpn0'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='lan'
firewall.@forwarding[1].dest='vpn0'
my DHCP:
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].confdir='/tmp/dnsmasq.d'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.lan.ra_slaac='1'
dhcp.lan.ra_flags='managed-config' 'other-config'
dhcp.lan.ra_management='1'
dhcp.lan.dhcp_option='6,8.8.8.8,8.8.4.4'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
trendy
April 18, 2020, 4:26pm
10
If you are explicitly pushing GoogleDNS to the hosts, it won't work for sure.
This is not the correct place. You can delete them from lan, as you have them configured in wan interface.
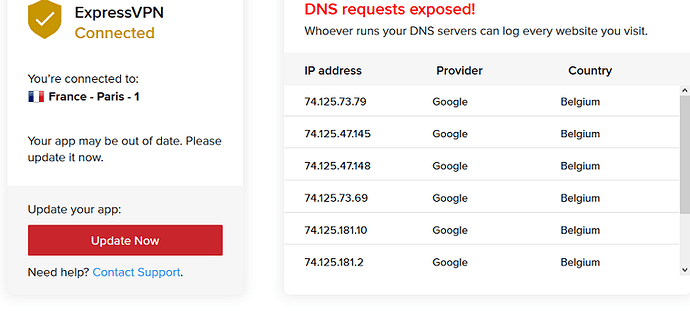
ok thanks, I removed them from lan.... but about vpn status (dns) still the same. Always google one pushed instead of vpn's dns.
trendy
April 18, 2020, 4:36pm
12
You didn't catch the hint to push express vpn dns in dhcp option 6?
btw, don't know if it could help, I scp to my dd wrt router, which is connected to the vpn with full protection according to dns leak test (expressvpn site) and I can watch netflix on it without problem. So I have access to the configuration in winscp, I see some private dns from express vpn..... maybe it could help??
i put that in DHCP option 6 only?
I added in option6, but still same result :
trendy
April 18, 2020, 4:54pm
17
You need to restart the dnsmasq service and force the client to renew the dhcp. They are still using GoogleDNS.
finaly, still the same...
trendy
April 18, 2020, 5:26pm
19
Unless this is an Android device with hardcoded Google DNS, you can verify the nameservers configured.ipconfig /all in windows and cat /etc/resolv.conf in linux.
in windows, I see :
gateway: 192.168.1.1