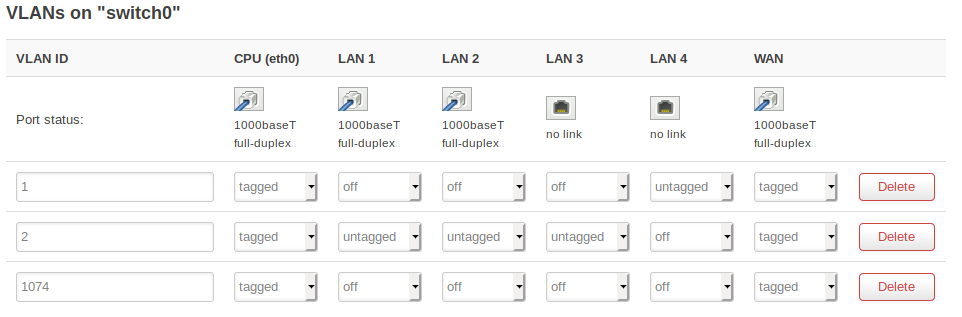
I'm very noob in networking and I want to practice with VLAN setup.
I want to segmentate my network in two vlans in order to separate secure and insecure devices. Main goal is that both subnets can't see each other. I do not know if my approach is the right way and i request advise:
- Router TPLINK Archer C7 - Openwrt 18.06.4
- VLAN 2 associated to interface "GUEST" for "insecure" devices like mobile phones, rasperry pi devices, tv streaming services and external services. (Lan1,Lan2.Lan3,Wlan1 - Subnet 192.168.5.x - Gateway 192.168.5.101)
- VLAN 1 associated to LAN interface for my pc. (Lan4 - Subnet 192.168.1.x - Gateway 192.168.1.1)
- My ISP (Jazztel, Spain) provide internet service thorough a VLAN assigned to 1074 port.
I have used Luci for the setup:
I have some doubts on the WAN setup, i marked all ports as tagged and i do not know if it is a good setup. My intention is to go out by the VLAN 1074 , therefore i mark VLAN1 and VLAN2 as tagged on WAN.
- Network/interfaces: (WAN,LAN,GUEST) I configured LAN and GUEST in the same Firewall zone and i attached LAN in physical settings eth0.1, GUEST to eth0.2-radio0-wlan1 and WAN to eth0.1074.
After setup i made some tests:
- I have internet access from GUEST interface from radio and lan ports.
- I have internet access from LAN interface.
- I have done ping test from GUEST devices and i have response from devices of the LAN interface, therefore I MUST HAVE SOME WRONG SETUP IN MY CONFIG. How can solve it?
- I have done ping test from LAN devices and i have response from GUEST gateway (192.168.1.1) but not from GUEST devices, therefore i think that this is the segmentation behavior that i need for LAN interface.
I hope somebody could help me to solve the problem, or if this is not a correct approach to segment my network, please advise me wihch is the best approach for it. I am learning about networking and i appreciate comments to improve.
cat /etc/config/network | grep -v macaddr
uci show firewall
or make a backup from the web ui can unzip it on a pc then paste whats in etc/config/network in code tags ( < ^ > )
root@OpenWrt:~# cat /etc/config/network | grep -v macaddr
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'XXXXXXXXX:/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option dns '208.67.222.222 208.67.220.220'
option ifname 'eth0.1'
config interface 'wan'
option proto 'dhcp'
option ifname 'eth0.1074'
config device 'wan_dev'
option name 'eth0.2'
config interface 'wan6'
option proto 'dhcpv6'
option ifname 'eth0.1074'
option auto '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1t 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '1074'
option ports '0t 1t'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '2'
option ports '0t 1t 2 3 4'
config interface 'guest'
option proto 'static'
option netmask '255.255.255.0'
option dns '208.67.222.222'
option type 'bridge'
option ifname 'eth0.2'
option ipaddr '192.168.5.101'
option gateway '192.168.5.101'
wan6 is disabled.
Next Firewall settings are default settings, i do not change any from default config:
root@OpenWrt:~# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan guest'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan wan6'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'`Preformatted text`