Dear Forum, I'm struggling with configuring my home network using Virtual LANs.
Router is a TP-Link Archer C7 AC1750, where only LAN Port 1 is in use. Devices are connected to a 8-port Netgear managed switch, whereas Port 1 is supposed to be used as trunk port.
My idea is to create the following networks:
Home
VLAN ID 67
192.168.67.0/24
DHCP
DMZ (such as NAS)
VLAN ID 10
192.168.10.0/24
Static
Guest
VLAN ID 254
192.168.254.0/25
DHCP
Management (such as switch)
VLAN ID 1
192.168.255.0/28
Static
root@openwrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd5c:dc7e:d327::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option dns '192.168.254.253'
option ifname 'eth1.1'
config interface 'wan'
option proto 'static'
option broadcast '192.168.178.255'
option ipaddr '192.168.254.254'
option netmask '255.255.255.252'
option gateway '192.168.254.253'
option ifname 'eth0.2'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
option auto '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 6t'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 2t'
option vid '10'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 2t'
option vid '67'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '254'
option ports '0t 2t'
config interface 'Home'
option proto 'static'
option ifname 'eth1.67'
option ipaddr '192.168.67.1'
option netmask '255.255.255.0'
option broadcast '192.168.67.255'
config interface 'DMZ'
option proto 'static'
option ifname 'eth1.10'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option broadcast '192.168.10.255'
config interface 'Guest'
option proto 'static'
option ifname 'eth1.254'
option ipaddr '192.168.254.1'
option netmask '255.255.255.128'
option broadcast '192.168.254.127'
config interface 'Mgmt'
option proto 'static'
option ipaddr '192.168.255.1'
option netmask '255.255.255.240'
option ifname 'eth1.1'
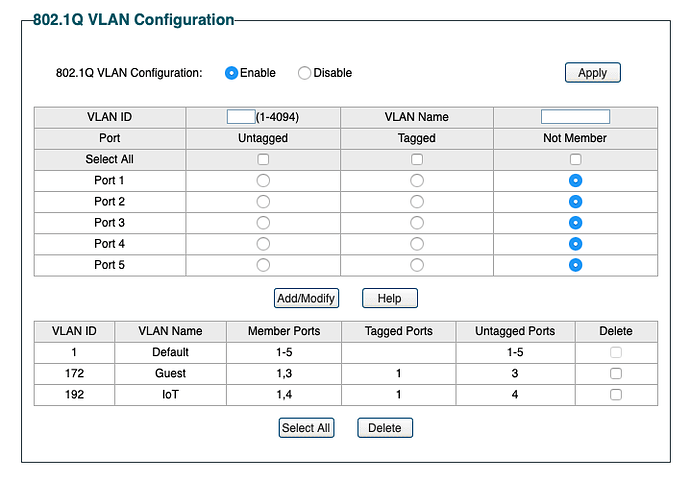
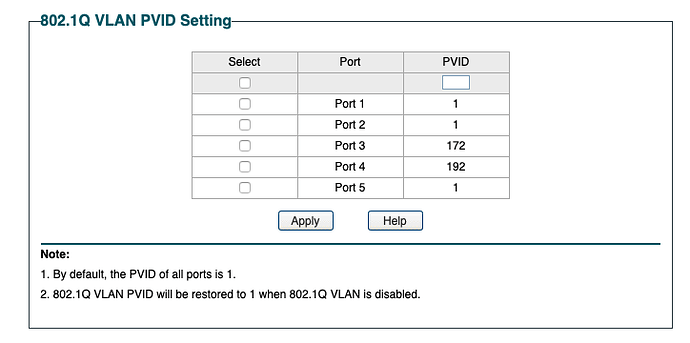
Switch port configuration:
Port 1:
PVID 1
All VLANs untagged
Ports 2-4:
PVID 67
1 Untagged
10 & 67 Tagged
Port 5:
PVID 10
1 Untagged
10 & 67 Tagged
Port 6:
PVID 1
1 Untagged
Ports 7 & 8:
PVID 254
1 Untagged
254 Tagged
Now, for instance, I want a PC to join VLAN 67 and get an address assigned from that network. Still it's assigned an address from the default LAN (.1.0), instead. What's wrong with my configuration?
I kindly ask for your understanding, since it's the first time I create such kind of networks from scratch by myself.
Thanks in advance for any precious answer.