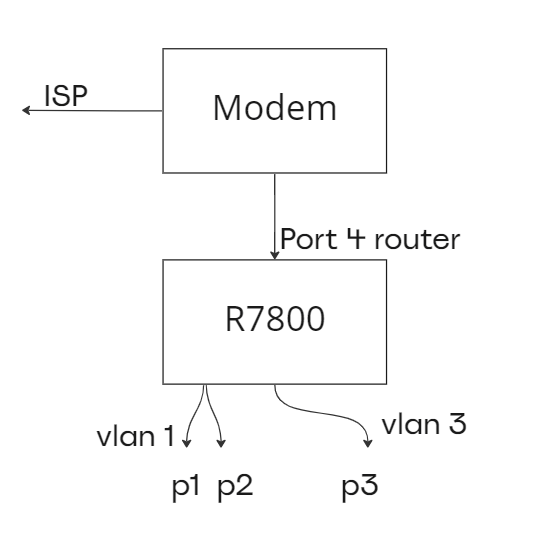
The problem I am facing is that I have a VLAN on port 1, 2, 4 and another VLAN on port 3 of the router.
Port 4 is connected to a modem with a 1GBPS connection.
Firmware version and router:
OpenWRT version: openwrt-22.03
Router: Netgear Nighthawk X4S R7800
Here is a schematic overview:
Vlan 1 is getting their IP addresses from the DHCP from the modem (192.168.1.1/24). Vlan 3 is getting their IP addresses on another subnet from the R7800 router (192.168.3.1/24).
The router has internet, VLAN 1 has internet, VLAN 3 is getting DHCP addresses in the correct range. But no internet for Vlan3. WAN port is not being used.
This is the setup for the VLANs (only 1 image allowed ![]() ):
):
| VLAN ID | CPU (eth0) | CPU (eth1) | LAN 1 | LAN 2 | LAN 3 | LAN 4 | WAN |
|---|---|---|---|---|---|---|---|
| 1 | t | t | u | u | off | u | off |
| 2 | t | t | off | off | off | off | u |
| 3 | t | t | off | off | u | off | off |
I am unsure how to debug what is missing right now. Maybe I have to do something with VLAN filtering in the bridges, but I believe that is if you just toss all interfaces in 1 bridge.
So it is probably some routing / firewall issue. I tried to add some similar rules that were already in place for lan, enabling masquerading but so far no luck.
In my previous setup using DD-WRT this IPTABLES entry did the trick:
iptables -t nat -I POSTROUTING -o `get_wanface` -j SNAT --to `nvram get wan_ipaddr`
If someone could point me in the right direction that would be great.