Hi everyone,
I have got a weird issue since I installed 23.05 and it was working fine in 22.03. This is my current setup:
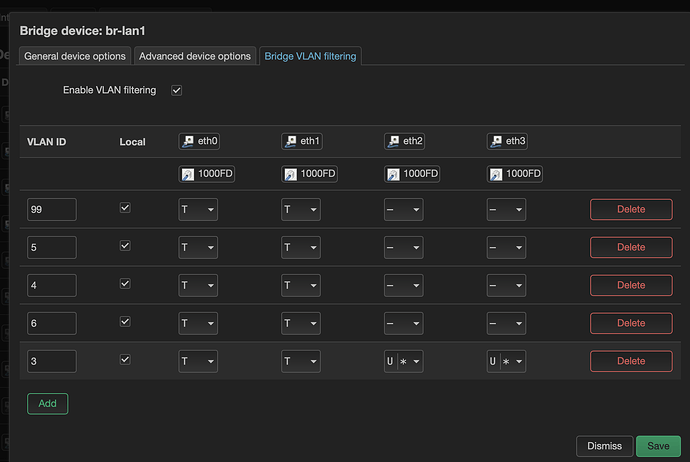
This is my main router and I tagged eth0 and eth1. These 2 ports connect to other 2 dumb APs which work fine. The problem is eth2 and eth3, even though I have untagged to the same VLANID, but they are not able to ping each other and also other devices that is on the same VLAN. Though other devices (connected through those 2 dumb APs can see these devices.
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd5c:9b09:e4de::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option device 'br-lan1.99'
option ipaddr '192.168.25.1'
option delegate '0'
option ipv6 '0'
config device
option type 'bridge'
option name 'br-lan1'
option ipv6 '0'
list ports 'eth0'
list ports 'eth1'
list ports 'eth2'
list ports 'eth3'
config bridge-vlan
option device 'br-lan1'
option vlan '99'
list ports 'eth0:t'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan1'
option vlan '5'
list ports 'eth0:t'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan1'
option vlan '4'
list ports 'eth0:t'
list ports 'eth1:t'
config interface 'GUEST'
option proto 'static'
option device 'br-lan1.4'
option ipaddr '192.168.8.1'
option netmask '255.255.255.0'
option auto '0'
config interface 'IOT'
option proto 'static'
option ipaddr '192.168.30.1'
option netmask '255.255.255.0'
option device 'br-lan1.6'
option auto '0'
config interface 'PARENTAL_ZONE'
option proto 'static'
option device 'br-lan1.5'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
config interface 'wan'
option proto 'dhcp'
option device 'wan.10'
option hostname '*'
option peerdns '0'
list dns '1.1.1.1'
config device
option type 'bridge'
option name 'wan'
list ports 'eth4'
option ipv6 '0'
config bridge-vlan
option device 'wan'
option vlan '10'
list ports 'eth4:t'
config bridge-vlan
option device 'br-lan1'
option vlan '6'
list ports 'eth0:t'
list ports 'eth1:t'
config interface 'docker'
option device 'docker0'
option proto 'none'
option auto '0'
config device
option type 'bridge'
option name 'docker0'
config route
option target '172.20.0.0/16'
option gateway '192.168.31.8'
option interface 'IOT'
option disabled '1'
config bridge-vlan
option device 'br-lan1'
option vlan '3'
list ports 'eth0:t'
list ports 'eth1:t'
list ports 'eth2:u*'
list ports 'eth3:u*'
config interface 'iot'
option proto 'static'
option device 'br-lan1.3'
option ipaddr '192.168.31.1'
option netmask '255.255.255.0'
and
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
option drop_invalid '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'WAN'
list network 'wan'
config forwarding 'lan_wan'
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config rule
option name 'Block PS4 connection'
list src_ip '192.168.31.10'
option dest 'wan'
option target 'REJECT'
option src 'iot'
list proto 'all'
config rule
option name 'Block IoT devices'
list proto 'all'
option src 'lan'
list src_ip '192.168.31.105'
list src_ip '192.168.31.147'
option dest 'wan'
option target 'REJECT'
option enabled '0'
config zone
option name 'GuestZone'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
list network 'GUEST'
config zone
option name 'IOTZone'
option output 'ACCEPT'
option input 'REJECT'
option forward 'REJECT'
list network 'IOT'
config forwarding
option src 'lan'
option dest 'IOTZone'
config forwarding
option src 'GuestZone'
option dest 'wan'
config rule
option dest_port '53 67 68'
option target 'ACCEPT'
option src 'GuestZone'
option name 'Guest DHCP and DNS'
config forwarding
option src 'IOTZone'
option dest 'wan'
config rule
option name 'IOT DHCP and DNS'
option src 'iot'
option target 'ACCEPT'
option dest_port '53 67 68'
config zone
option name 'ParZone'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'Parental_Zone'
list network 'PARENTAL_ZONE'
config forwarding
option src 'ParZone'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'ParZone'
config rule
option name 'Parental Zone'
option src 'ParZone'
option target 'ACCEPT'
option dest_port '53 67 68'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option proto 'udp'
option target 'ACCEPT'
option dest_port '59588'
config zone
option output 'ACCEPT'
option name 'Wireguard'
option input 'ACCEPT'
option forward 'ACCEPT'
list network 'vpn'
config rule
option src 'Wireguard'
option target 'ACCEPT'
option dest_port '53'
option name 'Wireguard DNS'
config forwarding
option src 'lan'
option dest 'Wireguard'
config redirect 'adguardhome_dns_53_lan'
option proto 'tcp udp'
option src_dport '53'
option target 'DNAT'
option dest_port '53'
option name 'Adguard Home Guest'
option src 'GuestZone'
option dest 'GuestZone'
option dest_ip '192.168.8.1'
config redirect 'adguardhome_dns_53_iot'
option proto 'tcp udp'
option src_dport '53'
option target 'DNAT'
option dest_port '53'
option name 'Adguard Home IOT'
option src 'iot'
option dest 'IOTZone'
option dest_ip '192.168.31.1'
config redirect 'adguardhome_dns_53_guest'
option proto 'tcp udp'
option src_dport '53'
option target 'DNAT'
option dest_port '53'
option name 'Adguard Home LAN'
option src 'lan'
option dest 'lan'
option dest_ip '192.168.25.1'
config redirect
option dest 'Wireguard'
option target 'DNAT'
option src 'Wireguard'
option dest_ip '192.168.9.1'
option name 'Adguard Home VPN'
list proto 'tcp'
list proto 'udp'
option src_dport '53'
option dest_port '53'
config zone
option name 'Cloudflare'
option input 'REJECT'
option masq '1'
option output 'REJECT'
option forward 'REJECT'
list network 'Cloudflare'
config forwarding
option src 'Wireguard'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'Cloudflare'
config forwarding
option src 'GuestZone'
option dest 'Cloudflare'
config forwarding
option src 'IOTZone'
option dest 'Cloudflare'
config forwarding
option src 'ParZone'
option dest 'Cloudflare'
config forwarding
option src 'Wireguard'
option dest 'Cloudflare'
config redirect
option dest 'ParZone'
option target 'DNAT'
option name 'Adguard Home Parental'
option src 'ParZone'
option dest_ip '192.168.20.1'
list proto 'tcp'
list proto 'udp'
option src_dport '53'
option dest_port '53'
config forwarding
option src 'Wireguard'
option dest 'GuestZone'
config forwarding
option src 'Wireguard'
option dest 'IOTZone'
config forwarding
option src 'Wireguard'
option dest 'ParZone'
config forwarding
option src 'Wireguard'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'GuestZone'
config forwarding
option src 'Wireguard'
option dest 'docker'
config forwarding
option src 'lan'
option dest 'docker'
config forwarding
option src 'docker'
option dest 'wan'
config forwarding
option src 'docker'
option dest 'IOTZone'
config forwarding
option src 'docker'
option dest 'Cloudflare'
config forwarding
option src 'IOTZone'
option dest 'docker'
config rule
option name 'Allow-IOT-mDNS'
option family 'ipv4'
option src 'iot'
option src_port '5353'
list dest_ip '224.0.0.251'
option dest_port '5353'
option target 'ACCEPT'
list proto 'tcp'
list proto 'udp'
config rule
option name 'Allow-IOT-mDNS6'
option family 'ipv6'
option src 'iot'
option src_port '5353'
list dest_ip 'ff02::fb'
option dest_port '5353'
option target 'ACCEPT'
list proto 'tcp'
list proto 'udp'
config rule
option name 'For Google Cast'
option src 'iot'
option dest 'lan'
option target 'ACCEPT'
list proto 'tcp'
list proto 'udp'
list dest_ip '192.168.25.106'
list src_ip '192.168.31.8'
option enabled '0'
config rule
option src 'iot'
list src_ip '192.168.31.8'
option target 'ACCEPT'
option dest_port '443'
option name 'Allow Wifi Proxy '
option dest 'lan'
list dest_ip '192.168.25.6'
list dest_ip '192.168.25.3'
list dest_ip '192.168.25.1'
option enabled '0'
config nat
option name 'HA To IOT'
option family 'ipv4'
option target 'SNAT'
option device 'br-lan1.6'
list proto 'all'
option src '*'
option enabled '0'
config zone 'docker'
option output 'ACCEPT'
option name 'docker'
list network 'docker'
option input 'REJECT'
option forward 'REJECT'
config rule
option name 'Allow Docker Host'
option src 'iot'
list src_ip '192.168.31.8'
option dest 'lan'
option target 'ACCEPT'
option enabled '0'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config include 'bcp38'
option type 'script'
option path '/usr/lib/bcp38/run.sh'
config zone
option name 'iot'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'iot'
config forwarding
option src 'lan'
option dest 'iot'
config forwarding
option src 'iot'
option dest 'docker'
config forwarding
option src 'iot'
option dest 'wan'
config forwarding
option src 'docker'
option dest 'iot'
TIA