Couple questions?
- I have a pretty basic setup - wrt router(192.168.1.2) wan port connected via ethernet cable to isp
gateway (192.168.1.1) lan port. (Its default config with wrt router ip changed to 192.168.2.1).
Trying to do some basic routing as a test but the rules seem to be getting ignored. Basically I'm
trying to match mac address and drop incoming or outgoing packets. Relevant snippet below
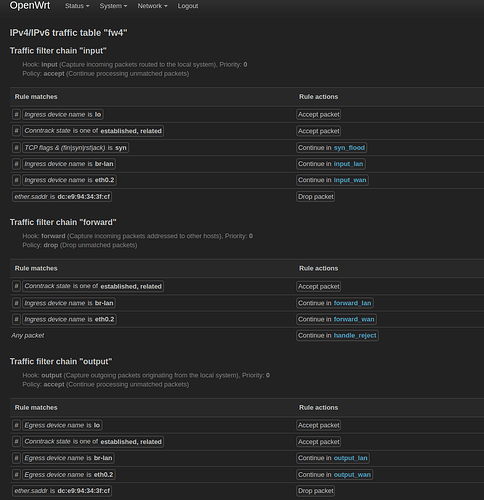
Table inet fw4 { # handle 1
chain input { # handle 1
type filter hook input priority filter; policy accept;
iifname "lo" accept comment "!fw4: Accept traffic from loopback" # handle 119
ct state established,related accept comment "!fw4: Allow inbound established and related flows" # handle 120
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets" # handle 121
iifname "br-lan" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic" # handle 122
iifname "eth0.2" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic" # handle 123
ether saddr dc:e9:94:34:3f:cf drop # handle 167
}
- can I have boolean NOT and OR conditions on a rule?
for example "accept every packet except ping"
!meta nfproto ipv4 icmp type { echo-request } accept(NOT) not sure about syntax there.
OR
`ether saddr = 00:00:5e:00:53:00 OR meta nfproto ipv4 icmp type { echo-request } accept (OR) not sure about syntax either.