My setup;
Raspberry Pi 4 Model B Rev 1.2 on OpenWrt 21.02-SNAPSHOT r15955-64ddac2c1c
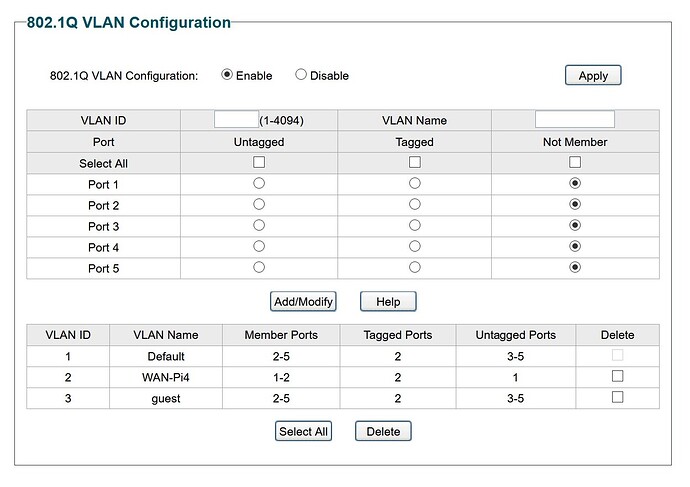
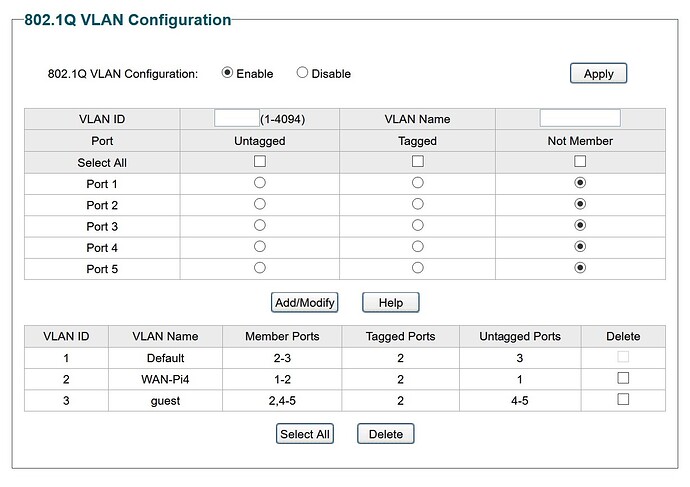
Managed switch SG105E;
Vlan 1 LAN
Vlan 2 WAN
Vlan 3 guest
I use Linksys Velops MX5300 as WiFi nodes (AP’s) the normal lan is in bridge mode, so OpenWrt is regulating this as normal, the guest network however is not as easy.
The guestnetwork is “fixed” on the nodes, even on bridge mode and is using the following settings:
Network 192.168.3.0/24
DHCP is on starts at 192.168.3.100
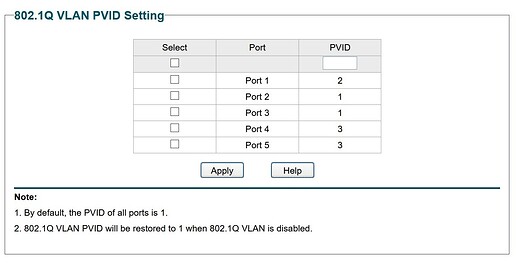
On vlan id 3
All not editable..
I have set my OpenWrt guest network the same way, so 192.168.3.0/24 on vlan id 3 and force dhcp.
All seems ok, the clients are getting an ip in the correct range, but I can connect to my lan (10.0.1.0/24)
I think this Is because the nodes are having there own ip address from Openwrt to make a connection.
Node 1 10.0.1.16 (set static)
Node 2 10.0.1.17 (set static)
Node 3 10.0.1.18 (set static)
How can I make traffic from the guest network, that is coming from this three ip’s route through my guest network (eth0.3) so it’s respecting the rules for guest?
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd58:122c:b677::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '10.0.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth0.1'
option peerdns '0'
list dns '84.200.69.80'
list dns '84.200.70.40'
config interface 'wan'
option proto 'dhcp'
option ifname 'eth0.2'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config interface 'vpnclient'
option proto 'none'
option ifname 'tun0'
config interface 'guest'
option proto 'static'
option netmask '255.255.255.0'
option ifname 'eth0.3'
option ipaddr '192.168.3.1'
option type 'bridge'
If I connect a client to the router first as lan client en then as guest client it tells me;
root@OpenWrt-Pi4:~# logread -f | grep dhcp
Fri Apr 9 16:21:37 2021 daemon.info dnsmasq-dhcp[27031]: DHCPREQUEST(br-lan) 10.0.1.123 48:26:2c:d9:a7:a6
Fri Apr 9 16:21:37 2021 daemon.info dnsmasq-dhcp[27031]: DHCPACK(br-lan) 10.0.1.123 48:26:2c:d9:a7:a6 Tanaka-Wasabi
Fri Apr 9 16:21:43 2021 daemon.info dnsmasq-dhcp[27031]: DHCPREQUEST(br-guest) 192.168.3.131 3a:f5:bf:44:69:f8
Fri Apr 9 16:21:43 2021 daemon.info dnsmasq-dhcp[27031]: DHCPACK(br-guest) 192.168.3.131 3a:f5:bf:44:69:f8 Tanaka-Wasabi
My Firewall settings;
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'guest'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config rule
option src 'guest'
option name 'guest printing'
option dest 'lan'
list dest_ip '10.0.1.104'
option target 'ACCEPT'
list proto 'all'
config include
option path '/etc/firewall.user'
config zone
option name 'vpnclient'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'vpnclient'
option masq '1'
config forwarding
option src 'lan'
option dest 'vpnclient'
config forwarding
option src 'guest'
option dest 'vpnclient'
config redirect
option target 'DNAT'
option name 'NAS SSL'
option src 'wan'
option src_dport '5051'
option dest 'lan'
option dest_ip '10.0.1.2'
option dest_port '5051'
config redirect
option target 'DNAT'
option name 'Cloudstation'
option src 'wan'
option src_dport '6690'
option dest 'lan'
option dest_ip '10.0.1.2'
option dest_port '6690'
config redirect
option target 'DNAT'
option name 'Snapshot'
option src 'wan'
option src_dport '5566'
option dest 'lan'
option dest_ip '10.0.1.2'
option dest_port '5566'