Hello folks,
I am now reading and googling for days, but I cannot solve my problems to have at least some basic VLAN setup running (and also knowing, why it is running).
Here is my setup:
- A two-nic-router, having one port for WAN and the other one for LAN. Internet works.
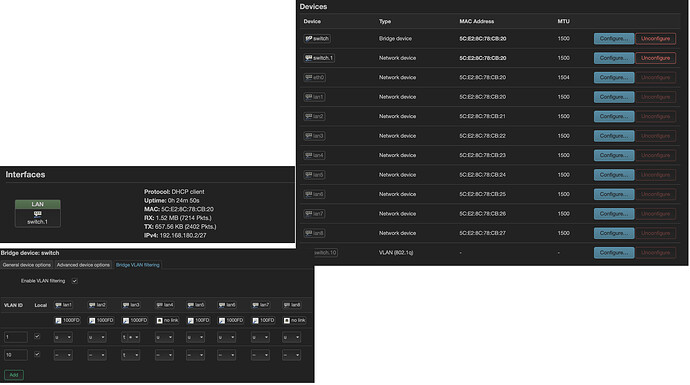
- A 8-port-router, which is connected to the LAN port of the router and having an TP-Link connected to port 1. The Interface "switch.1" is defined as DHCP Client and is getting its IP address by a static assignment in the router ("static lease").
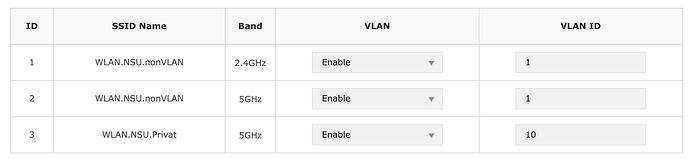
- A TP Link Access Point, having one SSID "nonVLAN" with VLAN1 and "Privat" with VLAN10.
When I connect to the nonVLAN (ID 1) the Laptop is getting an IP address and can access the Internet.
When I connect to Laptop to the second SSID Privat (ID 10) no IP address is assigned.
I am clicking around in LuCi, but actually, I do not know, what I am doing. I have a very basic understanding, what a VLAN is, what a Trunk Port with multiple VLAN IDs is and what an Access Port with only one VLAN ID is. But I do not get, when I need to Bridge Ports and when to create interfaces and when to use the VLAN filtering tab in a Bridge device...
And I am looking for answers to do this in LuCi.
The Setup:
The Access Point:
The Switch:
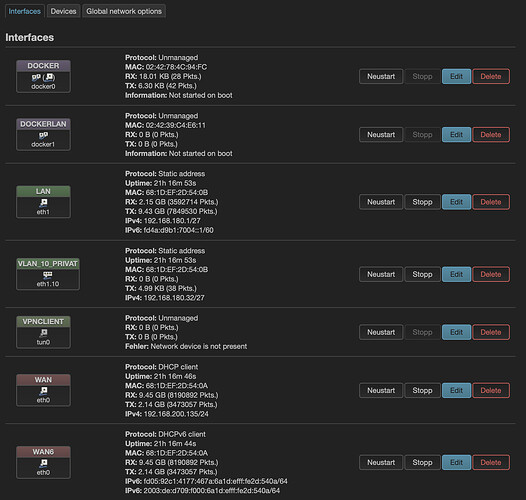
The Router:
Let's start with the router to make sure it is properly configured (everythign starts there):
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/dhcp
cat /etc/config/firewall
Okay, let's start:
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd4a:d9b1:7004::/48'
config interface 'lan'
option proto 'static'
option ip6assign '60'
option ipaddr '192.168.180.1'
option device 'eth1'
option netmask '255.255.255.224'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
config interface 'dockerlan'
option device 'docker1'
option proto 'none'
option auto '0'
config device
option type 'bridge'
option name 'docker1'
config interface 'VPNClient'
option proto 'none'
option device 'tun0'
config interface 'docker'
option device 'docker0'
option proto 'none'
option auto '0'
config device
option type 'bridge'
option name 'docker0'
config device
option type '8021q'
option ifname 'eth0'
option vid '7'
option name 'eth0.7'
config device
option type '8021q'
option ifname 'eth1'
option vid '10'
option name 'eth1.10'
config interface 'vlan_10_privat'
option proto 'static'
option device 'eth1.10'
option ipaddr '192.168.180.32'
option netmask '255.255.255.224'
It's intended, to have all VLANs in the network 192.168.180.x range with a limited subnet, not the default /24 (255.255.255.0).
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option start '20'
option limit '30'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option mac '5C:E2:8C:78:CB:20'
option dns '1'
option ip '192.168.180.2'
option name 'Switch01'
config host
option name 'AccessPoint'
option dns '1'
option mac '28:87:BA:D1:96:A0'
option ip '192.168.180.3'
config host
option name 'NAS'
option dns '1'
option mac '00:11:32:D8:87:CA'
option ip '192.168.180.10'
config host
option name 'ZigBee'
option dns '1'
option mac 'B8:27:EB:E2:3D:73'
option ip '192.168.180.12'
config host
option name 'Xbox'
option dns '1'
option mac '28:16:A8:D3:04:F9'
option ip '192.168.180.80'
config host
option name 'WohnzimmerTVLAN'
option dns '1'
option mac '78:5D:C8:23:F6:11'
option ip '192.168.180.81'
config host
option name 'WohnzimmerAppleTV'
option dns '1'
option mac 'F0:B3:EC:66:A5:64'
option ip '192.168.180.85'
config host
option name 'HDHomerun'
option dns '1'
option mac '00:18:DD:41:06:C0'
option ip '192.168.180.87'
config dhcp 'vlan_10_privat'
option interface 'vlan_10_privat'
option leasetime '12h'
option start '33'
option limit '62'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vlan_10_privat'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'WAN-Login'
option src 'wan'
option dest_port '22'
option proto 'tcp'
option target 'ACCEPT'
config rule
option name 'WAN-Login-LuCi'
option src 'wan'
option dest_port '80'
option proto 'tcp'
option target 'ACCEPT'
config rule
option name 'WAN-AdGuard-Login'
option src 'wan'
option dest_port '3000'
option target 'ACCEPT'
config rule
option src 'wan'
option target 'ACCEPT'
option name 'WAN-Netdata-Login'
option dest_port '19999'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
config zone 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option name 'docker'
option forward 'REJECT'
option log '1'
list device 'docker0'
list device 'docker1'
list network 'dockerlan'
list network 'docker'
option masq '1'
config zone
option name 'vpnclient'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'VPNClient'
config forwarding
option src 'lan'
option dest 'vpnclient'
config rule
option name 'DockertoDockerAny'
option src 'docker'
option dest 'docker'
option target 'ACCEPT'
config forwarding
option src 'lan'
option dest 'docker'
config rule
option name 'Docker-to-WAN'
option src 'docker'
option target 'ACCEPT'
option dest '*'
The address on this interface is incorrect... you've specified the network ID, but that cannot be assigned to a host. You can use 192.168.180.33
Your main LAN DHCP pool size is too large. When using a /27 subnet, you can have at most 30 hosts (including the router itself). The limit must be less than 29. Therefore, if you start at 20, you must have a limit of 11 or lower.
Similarly, the limit here is too large... it must be 29 or less. I think that it is okay for the start position here to be 34, but not 33 since that is the router's address.
Try fixing those things and see if it works. If not, we'll next want to look at the switch.
Wow, I haven‘t noticed this. I thought, I assign the last valid address, not the total number. I haven‘t read this exactly. I have changed two things:
- The DHCP ranges have been corrected, giving the total number, not the last one before the broadcast.
- Changed the address of the Private VLAN to 192.168.180.33 (instead of .32).
This solved two things:
- I now get a connection via the Private SSID with an IP address of the router defined range.
- I get internet access, as the Private VLAN is assigned to the LAN zone.
Yes... the way it works is as follows:
- Start = starting offset relative to the network's first host address
- Limit = size of the DHCP pool (maximum number of hosts served by DHCP)
So the end = start + limit - 1.
In a /24 network, the start position is the same as the last octet of the address... so start = 50 on 192.168.1.0/24 --> 192.168.1.50 would be the first address in the DHCP pool.
So actually, I said earlier that it may be okay to have the start at 33... I am not entirely sure if that's right since it is supposed to be an offset from the first host address.