arrmo
August 28, 2021, 1:04am
1
Hi,
OK, pulling my hair out - this one is not making sense to me. I have split out two sub-networks ... for wireless, and lan. LAN is using VLAN - DHCP works (for a client connecting over that specific VLAN), ssh ... all good. And LuCI sort of starts, shows the "LuCI - Lua Configuration Interface" message ... but then just stops. Never pulls up the login screen. I can access LuCI from wireless, just not over LAN / VLAN. I was thinking this was a network config issue, but again - ssh is fine, ping, etc. Just not LuCI.
Any special settings that I'm missing for having LuCI work with a VLAN (or different subnet perhaps)?
Thanks!
We need to see the config files, otherwise we can only guess.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
arrmo
August 28, 2021, 4:41am
3
Sure - below. Thanks!
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '::::/48'
config interface 'lan'
option proto 'static'
option ip6assign '60'
option gateway '192.168.2.1'
list ipaddr '192.168.250.1/24'
option device 'br-lan.250'
list dns '192.168.2.1'
config device
option name 'internet'
option macaddr '----'
config interface 'wan'
option device 'internet'
option proto 'dhcp'
config interface 'wan6'
option device 'internet'
option proto 'dhcpv6'
config interface 'wgRouter'
option proto 'wireguard'
option private_key '----'
list addresses '----'
config wireguard_wgRouter
option description '----'
option persistent_keepalive '25'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option route_allowed_ips '1'
option public_key '----'
option preshared_key '----'
option endpoint_host '----
config interface 'wlan'
option proto 'static'
option ipaddr '192.168.251.1'
option netmask '255.255.255.0'
option gateway '192.168.2.1'
option device 'br-wlan'
config device
option type 'bridge'
option name 'br-wlan'
config device
option type 'bridge'
option name 'br-lan'
option ipv6 '0'
list ports 'ethernet1'
list ports 'ethernet2'
list ports 'ethernet3'
list ports 'ethernet4'
config bridge-vlan
option device 'br-lan'
option vlan '250'
list ports 'ethernet1:t'
list ports 'ethernet2:t'
list ports 'ethernet3:t'
list ports 'ethernet4:t'\
# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11g'
option path 'mbus@f1000000/mbus@f1000000:pcie@82000000/pci0000:00/0000:00:01.0/0000:01:00.0'
option htmode 'HT20'
option channel 'auto'
option country 'US'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid '---'
option encryption 'psk2+ccmp'
option key '---'
option network 'wlan'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11a'
option path 'mbus@f1000000/mbus@f1000000:pcie@82000000/pci0000:00/0000:00:02.0/0000:02:00.0'
option country 'US'
option cell_density '0'
option htmode 'HT40'
option channel 'auto'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid '---'
option key '---'
option ieee80211w '1'
option encryption 'psk2+ccmp'
option network 'wlan'
# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option rebind_protection '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ra_management '1'
list ra_flags 'none'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'WLAN'
option interface 'WLAN'
option start '100'
option limit '150'
option leasetime '12h'
list ra_flags 'none'
config dhcp 'wlan'
option interface 'wlan'
option start '100'
option limit '150'
option leasetime '12h'
list ra_flags 'none'
# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wlan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wgRouter'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
FYI, I was thinking the issue was not including eth0 in the bridge, but nope - that didn't help. So odd that ssh works fine, just not LuCI.
Hegabo
August 28, 2021, 5:09am
4
Is it the same computer that you use to test both VLANs? If not, could you try it?
Could it possibly something to do with the browser or the cache?
What address(es) are you using in your web browser to attempt to connect to LuCI?
arrmo
August 28, 2021, 11:21am
6
Hi,
I can get to LuCI over WiFi, at http://192.168.251.1 , but http://192.168.250.1/ fails (or "stalls out"). I can ssh to 192.168.250.1 just fine though ... only LuCI fails.
And yes, all from the same PC. I also did try clearing the browser cache, all site data for that (troubled) IP.
Make sense?
Thanks!
arrmo
August 28, 2021, 3:16pm
7
OK, this may not mean anything, but "Forbidden" seems interesting to me
GET / HTTP/1.1
Host: 192.168.250.1
Connection: keep-alive
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
If-None-Match: "64d-20a-6128f525"
If-Modified-Since: Fri, 27 Aug 2021 14:22:29 GMT
HTTP/1.1 304 Not Modified
Connection: Keep-Alive
Keep-Alive: timeout=20
ETag: "64d-20a-6128f525"
Last-Modified: Fri, 27 Aug 2021 14:22:29 GMT
Date: Sat, 28 Aug 2021 03:52:07 GMT
GET /cgi-bin/luci/ HTTP/1.1
Host: 192.168.250.1
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.250.1/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
HTTP/1.1 403 Forbidden
Connection: Keep-Alive
Transfer-Encoding: chunked
Keep-Alive: timeout=20
X-LuCI-Login-Required: yes
Content-Type: text/html; charset=UTF-8
Cache-Control: no-cache
Expires: 0
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
Thanks!
ubus call system board; uci show uhttpd; iptables-save -c
arrmo
August 28, 2021, 3:43pm
9
vgaetera:
ubus call system board
Sure!
ubus call system board
{
"kernel": "5.10.60",
"hostname": "-----",
"system": "Feroceon 88FR131 rev 1 (v5l)",
"model": "Linksys EA3500 (Audi)",
"board_name": "linksys,ea3500",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "SNAPSHOT",
"revision": "r17435-97e32e9702",
"target": "kirkwood/generic",
"description": "OpenWrt SNAPSHOT r17435-97e32e9702"
}
}
uci show uhttpd
uhttpd.main=uhttpd
uhttpd.main.listen_http='0.0.0.0:80' '[::]:80'
uhttpd.main.listen_https='0.0.0.0:443' '[::]:443'
uhttpd.main.redirect_https='0'
uhttpd.main.home='/www'
uhttpd.main.max_requests='3'
uhttpd.main.max_connections='100'
uhttpd.main.cert='/etc/uhttpd.crt'
uhttpd.main.key='/etc/uhttpd.key'
uhttpd.main.cgi_prefix='/cgi-bin'
uhttpd.main.lua_prefix='/cgi-bin/luci=/usr/lib/lua/luci/sgi/uhttpd.lua'
uhttpd.main.script_timeout='60'
uhttpd.main.network_timeout='30'
uhttpd.main.http_keepalive='20'
uhttpd.main.tcp_keepalive='1'
uhttpd.main.ubus_prefix='/ubus'
uhttpd.main.rfc1918_filter='1'
uhttpd.defaults=cert
uhttpd.defaults.days='730'
uhttpd.defaults.key_type='ec'
uhttpd.defaults.bits='2048'
uhttpd.defaults.ec_curve='P-256'
uhttpd.defaults.country='ZZ'
uhttpd.defaults.state='Somewhere'
uhttpd.defaults.location='Unknown'
uhttpd.defaults.commonname='OpenWrt'
iptables-save -c
# Generated by iptables-save v1.8.7 on Sat Aug 28 03:04:58 2021
*nat
:PREROUTING ACCEPT [110211:21597305]
:INPUT ACCEPT [18487:1276894]
:OUTPUT ACCEPT [9401:649472]
:POSTROUTING ACCEPT [843:59107]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[110211:21597305] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[59223:11333855] -A PREROUTING -i br-lan.250 -m comment --comment "!fw3" -j zone_lan_prerouting
[50988:10263450] -A PREROUTING -i br-wlan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i internet -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i wgRouter -m comment --comment "!fw3" -j zone_wan_prerouting
[14297:1408178] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[1:341] -A POSTROUTING -o br-lan.250 -m comment --comment "!fw3" -j zone_lan_postrouting
[4:1338] -A POSTROUTING -o br-wlan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o internet -m comment --comment "!fw3" -j zone_wan_postrouting
[13454:1349071] -A POSTROUTING -o wgRouter -m comment --comment "!fw3" -j zone_wan_postrouting
[5:1679] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[110211:21597305] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[13454:1349071] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[13454:1349071] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sat Aug 28 03:04:58 2021
# Generated by iptables-save v1.8.7 on Sat Aug 28 03:04:58 2021
*mangle
:PREROUTING ACCEPT [158232:29649235]
:INPUT ACCEPT [33603:2589120]
:FORWARD ACCEPT [37801:7498410]
:OUTPUT ACCEPT [39889:5767701]
:POSTROUTING ACCEPT [77691:13266452]
[0:0] -A FORWARD -o internet -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i internet -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[21058:1095016] -A FORWARD -o wgRouter -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i wgRouter -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sat Aug 28 03:04:58 2021
# Generated by iptables-save v1.8.7 on Sat Aug 28 03:04:58 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[4506:354636] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[29097:2234484] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[4075:525779] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[109:5668] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[12162:833240] -A INPUT -i br-lan.250 -m comment --comment "!fw3" -j zone_lan_input
[12860:875465] -A INPUT -i br-wlan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i internet -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i wgRouter -m comment --comment "!fw3" -j zone_wan_input
[37801:7498410] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[0:0] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[37767:7491170] -A FORWARD -i br-lan.250 -m comment --comment "!fw3" -j zone_lan_forward
[34:7240] -A FORWARD -i br-wlan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i internet -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i wgRouter -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[4506:354636] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[35383:5413065] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[9124:2570695] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1:341] -A OUTPUT -o br-lan.250 -m comment --comment "!fw3" -j zone_lan_output
[5:1666] -A OUTPUT -o br-wlan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o internet -m comment --comment "!fw3" -j zone_wan_output
[26253:2840363] -A OUTPUT -o wgRouter -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[109:5668] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[1:341] -A zone_lan_dest_ACCEPT -o br-lan.250 -m comment --comment "!fw3" -j ACCEPT
[5:1666] -A zone_lan_dest_ACCEPT -o br-wlan -m comment --comment "!fw3" -j ACCEPT
[37801:7498410] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[37801:7498410] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[25022:1708705] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[25022:1708705] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[6:2007] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[6:2007] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[12162:833240] -A zone_lan_src_ACCEPT -i br-lan.250 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[12860:875465] -A zone_lan_src_ACCEPT -i br-wlan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o internet -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o internet -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o wgRouter -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[64054:10338773] -A zone_wan_dest_ACCEPT -o wgRouter -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o internet -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o wgRouter -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[0:0] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[26253:2840363] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[26253:2840363] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i internet -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i wgRouter -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Aug 28 03:04:59 2021
FYI, from some other poking I did, I tried changing to uhttpd.main.rfc1918_filter='0' ... no delta.
Thanks!
1 Like
Using the same port numbers, tagged and untagged sounds like a bad idea.
arrmo
August 28, 2021, 7:20pm
11
That may be, no argument - but trying to understand. As uhttpd is listening on 0.0.0.0, is it really a concern? I would have thought this would be OK, but I may be wrong!
Sure, will remove DNS, NP! But why gateways? Again, just to understand.
That's not real, just confirmed. Fat-fingered that somehow when I pasted it. Sorry!
Will let you know when I remove the gateways and DNS. Appreciate it!
arrmo
August 28, 2021, 7:26pm
12
Removed gateways, and DNS - exactly the same. Dang it!
BTW, are gateways not needed, because LAN is automatically forwarded to WAN? Again, just to understand.
As above, DHCP works, as does ping, ssh. Just not LuCI. Weird.
Thanks!
arrmo
August 28, 2021, 11:21pm
13
FYI, a bit more info on this - went to another machine, set up the same VLAN (i.e. 250) => same thing ... DHCP works, ssh, just gets "stuck" with LuCI. Will keep digging!
Actually, bumped into one more oddity - ssh works great, but scp fails. Huh? LOL!
Thanks!
SLIGHT UPDATE (that may help?) - I decided to grab another router, give it a try. It works! Here is the difference,
Thanks!
arrmo
August 29, 2021, 9:57pm
14
OK, close
But (of course there's a but
Thanks!
There are 2 recommended approaches:
Use unique port numbers and do not share ports among VLANs.
A specific port number can only be shared when all its entries are tagged.
arrmo
August 30, 2021, 2:36am
16
Thanks! Sorry, a couple dumb questions - I may be getting confused by some of the terminology (and yes, it's on me VLAN link ... similar, but still leaving me a bit perplexed.
vgaetera:
Split ports and do not overlap the same port numbers among different VLANs.
I think you're meaning / saying that if a port is tagged or untagged (either one!) in one VLAN, make sure it's off in all the others. Do I have that right? I'm OK with that, just making sure.
vgaetera:
Port numbers can overlap for a specific port only when all its entries are tagged.
OK, so not allowed is a port with tagged in one VLAN, untagged in another ... correct?
Where I am getting messed up I think - all the examples also show WAN => but this doesn't exist in my case. And I admit, I'm not 100% how the "CPU" plays into this.
Thanks again!
1 Like
arrmo
August 30, 2021, 2:40am
18
BTW, here is my routing table => really not getting an IP on the WAN side
# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.250.0 * 255.255.255.0 U 0 0 0 br-lan
192.168.251.0 * 255.255.255.0 U 0 0 0 br-wlan
Thansk!
There are multiple threads on the forum about bugs of built-in switches.above .
1 Like
arrmo
August 30, 2021, 2:50am
20
Will do some more digging - and trying now the notes above. Thanks!
My struggle is that somewhere along the way I lose my uplink. Let me reset the router, walk through slowly to see where that is. Appreciate the pointers!
1 Like
Regarding the tagged and untagged networks...
The 802.1q spec allows you to use zero or one untagged and zero, one, or many tagged networks on any given port. You are allowed to use untagged + tagged on the same port. However, there are some who will recommend that a trunk port should never contain an untagged network. This is a matter of personal/professional opinion, and its s often based on the fact that an untagged network has some level of ambiguity (regarding the actual VLAN it belongs to) once it is downstream of the respective switch port, and can thus lead be prone to human error with the configuration of any downstream devices.
The other consideration is that if you have any non-VLAN aware devices (i.e. unmanaged switches, most end devices such as computers, STBs, etc.), you should only connect those to access ports (i.e. a port with an untagged network + zero tagged networks).
With respect to your specific issue, some lower end/older devices have switch chips that don't properly support the full 4095 VLAN IDs. For those, I think it is often limited to a range of 1-16. So try again with your VLAN IDs within that range.
I would recommend configuring an access port on your router for each of the VLANs so that you can literally just plug your computer into a port, test a specific VLAN, then move to the next port and test the next VLAN and so on. This helps troubleshoot the VLANs in the most straightforward way. Then, once all has been verified with the VLAN configuration in general, you can make a trunk port and then do the same on the managed switch on the other end -- thus verifying that the trunk is configured correctly as well as the managed switch.
1 Like
 . I ran tcpdump on the OpenWrt side, watching the LuCI (Port 80) traffic, then looked at it in Wireshark. Thoughts?
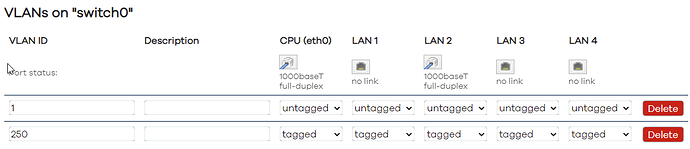
. I ran tcpdump on the OpenWrt side, watching the LuCI (Port 80) traffic, then looked at it in Wireshark. Thoughts? . On the second router (with "Switch"), I can get VLAN working ... ssh, DHCP, scp, LuCI. All good on the LAN side. And the switch setup is like this (seems standard from what I have found),
. On the second router (with "Switch"), I can get VLAN working ... ssh, DHCP, scp, LuCI. All good on the LAN side. And the switch setup is like this (seems standard from what I have found),