Goal
I want to setup a virtual networking lab to test out OpenWRT configurations without having to purchase multiple routers and switches, nor disrupt my current network. Currently I want to simulate having an edge router connected to an access point, first with a single network interface/subnet, then with multiple network interfaces/subnets isolating traffic using VLAN.
I have limited knowledge of networking, even more so with Linux, and only a layperson's understanding of layer 2 vs layer 3. However I do have some experience with a single "all-in-one" OpenWRT router running multiple subnets (LAN vs Guest), DDNS, Wireguard, etc., and experimented successfully with a physical mesh network of multiple OpenWRT devices using a wired back-haul to the AP. I thought this would be relatively simple to do with Oracle Virtualbox after I watched many of the excellent OneMarcFifty videos on YouTube on using Virtualbox, configuring Access Points, and using VLANs.
I am using Virtualbox on Kubuntu with a single bridge connection for external network access, a host only network to easily manage the routers, and multiple internal networks to act as virtual switches. I assumed these internal networks work like an actual switch per the Virtualbox documentation:
Once there is more than one active virtual network card with the same internal network ID, the Oracle VM VirtualBox support driver will automatically wire the cards and act as a network switch. The Oracle VM VirtualBox support driver implements a complete Ethernet switch and supports both broadcast/multicast frames and promiscuous mode.
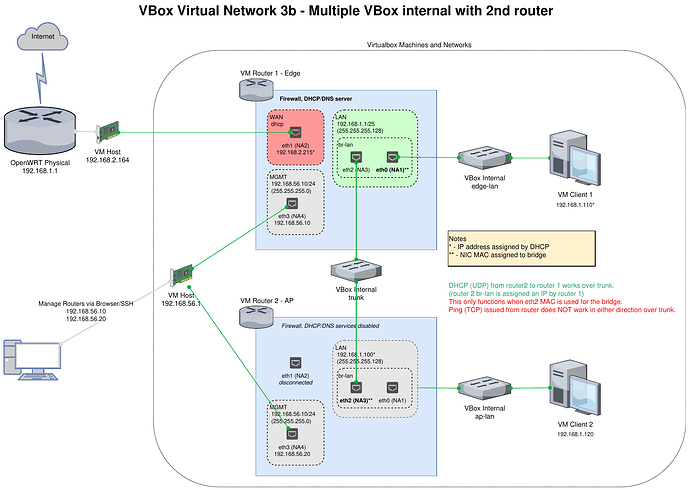
The Problem
Two Ethernet devices (aka ports) are bridged together in OpenWRT. Each port is configured in VBox to be connected to a different virtual internal network. Each of these networks also has a single client VM connected. The OpenWRT bridge auto-configures to use the MAC address of the first Ethernet device (can also be explicitly set).
The connection between VM Client 1 and OpenWRT functions normally when connected using the port that has the same MAC as bridge (br-lan). However, VM Client 2 is connected to the other port which has a different MAC than br-lan. This client successfully obtains an IP address using DHCP (UDP) from OpenWRT (confirmed through Luci, not coming from VirtualBox), but no TCP traffic is working. The router cannot ping client 2 or vice versa.
Is this a VBox limitation or a misconfiguration of OpenWRT?
Would this configuration work with actual hardware?
The Configuration
I want to get to the configuration in the 2nd diagram (3b) for my lab, but for troubleshooting it is easier to work with the simpler configuration in the first (3a). For the OpenWRT router the only difference in configuration is which internal network is assigned to eth2; this is done in Vbox, not OpenWRT.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config device
option name 'br-lan'
option type 'bridge'
option ipv6 '0'
list ports 'eth0'
list ports 'eth2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.128'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'eth1'
option ipv6 '0'
config device
option name 'eth2'
option ipv6 '0'
config device
option name 'eth3'
option ipv6 '0'
config interface 'MGMT'
option proto 'static'
option device 'eth3'
option ipaddr '192.168.56.10'
option netmask '255.255.255.0'
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'MGMT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
For context, this is how I first configured the lab. This is more difficult to diagnose since it involves a 2nd router. Router 2 could not obtain a DHCP address from router 1 unless I set router 2 br-lan to use the MAC of device eth2. This leads me to believe I am facing a Virtualbox limitation.