I am sorry to bother the gods of openwrt, but I have spent an entire day (and night) trawling the web for answers and experimenting to no avail.
I have 2 IP cameras that I will put in my baby's and toddler's rooms to monitor their sleep. I am a little paranoid about the cameras 'phoning home'. We have a decent router/gateway from our ISP already, so I bought a lightweight router that is running OpenWrt. There are obviously guides online (e.g. forum post and youtube guide) of others trying the same thing, but they usually:
a. configure it all in the one OpenWrt router, or
b. they only require communications one way (i.e. IOT --> LAN only).
I want to be able to send and receive data from the IOT devices from my regular home LAN, I just don't want them to be connecting to the internet at all.
If I set up the OpenWrt router with an IOT WLAN, I am able to:
[x] block the IOT devices from the internet
[x] ping IOT subnet --> LAN devices
[ ] ping LAN devices --> IOT subnet 
This is because the IOT devices are on a different subnet (e.g. 192.168.3.1/24). I can have everything on the same subnet if I make my OpenWrt device behave as a 'dumb' WAP, but then I am unable to block the IOT WLAN from the internet via OpenWrt's firewall or my ISP's MAC filtering of the OpenWrt ethernet connection entirely.
From all of my research thus far, what I need is to configure my IOT zone/interface/WLAN to use my ISP Router as the remote/external DHCP server, so that my cameras get a static IP address that I can work with; but then use the OpenWrt router to block traffic destined for subnets outside of my home's main one (i.e. 192.168.0.1/24)
TL;DR: How can I configure a OpenWrt 'interface' (e.g. my IOT WLAN) to forward/relay DHCP messages to my upstream/ISP router but still use the OpenWrt's cool firewall features for everything else? I had tried this and bricked my router and had to start again.
┌─────┐
│ WWW │
└──┬──┘
│
┌─────────────┴──────────────┐ ┌───────────────────────┐
│ ISP Router │ │ OpenWrt Box │
│ 192.168.0.1/24 │ ethernet │WAN Port's MAC Address │
│ Basic controls possible ├──────────┤is assigned 192.168.0.3│
│ (set static ip addresses, │ patch │by the ISP Router │
│ mac filtering, etc.) │ cable │ │
│ │ │ │
└─┬─────────────┬─────────┬──┘ └─────┬──────────────┬──┘
│ Home WLAN │ │ │ IOT WLan │
│ │ │ │ │
│ │ │ │ │
┌──────┴──────┐ ┌────┴───┐ ┌──┴─┐ ┌────────┴──────┐ ┌────┴────────────┐
│ │ │ │ │ │ │ Camera 1 │ │ Camera 2 │
│ My laptop │ │My phone│ │etc.│ │ 192.168.0.201 │ │ 192.168.0.202 │
│ │ │ │ │ │ │ (ideally) │ │ (ideally) │
└─────────────┘ └────────┘ └────┘ └───────────────┘ └─────────────────┘
So far I have left LAN as default. WAN is the interface that is connected to my main home LAN, so I have set 'Input' to accept. The 'home' zone is simply set to everything to do with subnet 192.168.0.1/24, and 'iot' is everything to do with my specific wifi SSID for IOT devices.
Again, this works swimmingly, except that I cannot access my IOT devices from my main/external LAN because it is on a different subnet (e.g.
192.168.3.1/24)
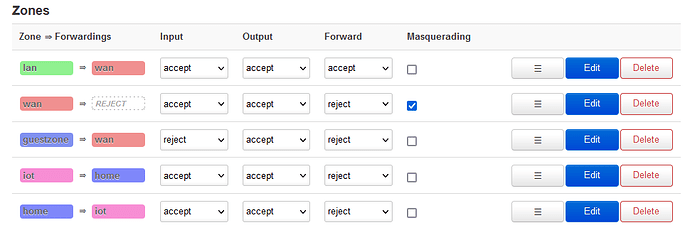

 IOT devices are blocked from the internet via the OpenWrt Router's firewall (see below)
IOT devices are blocked from the internet via the OpenWrt Router's firewall (see below)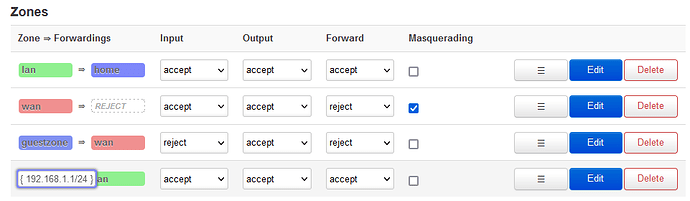
 . When I turn the VPN client on my PC (say
. When I turn the VPN client on my PC (say