Hi,
I have two different interfaces, one for WLAN and the other for LAN.
-> I would like to use the Wireguard VPN only for the WLAN interface.
->The LAN connections should just directly connect to the internet without Wireguard.
But the LAN interface stops working as soon as the Wireguard is added.
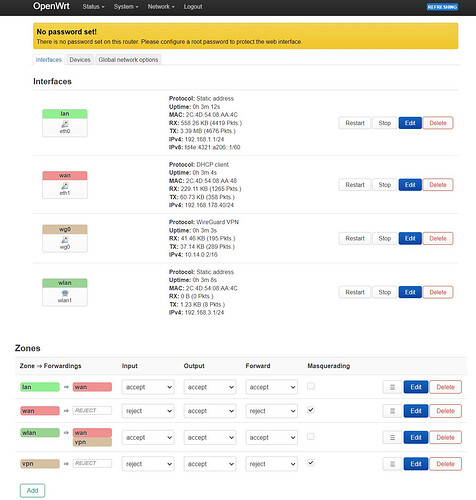
Here is my current setup with interfaces and firewalls:
WLAN + Wireguard = Works
Is it possible to have such a configuration? Where am I going wrong?
Thank you!!
xize
April 4, 2024, 3:07am
2
Hmm, maybe you need to forward the vpn zone to lan?
Edit:
Oh, and maybe the default gateway on the other interfaces need to be unchecked except for lan and wan otherwise it can be wrongly seen as the wrong gateway, this is obviously not what you want.
egc
April 4, 2024, 6:30am
3
Have a look at Policy Based Routing (PBR): https://docs.openwrt.melmac.net/pbr/
1 Like
I'm not sure what you mean by forward vpn zone to lan. Does it help?
I do not want to use vpn for the lan connections.
krazeh
April 4, 2024, 12:45pm
5
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
1 Like
root@OpenWrt:~# ubus call system board
{
"kernel": "5.10.176",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 5 (v7l)",
"model": "ASUS RT-AC58U",
"board_name": "asus,rt-ac58u",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "ipq40xx/generic",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd4e:4321:a206::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config device
option name 'eth0'
option macaddr 'xx:xx:xx:xx:xx:4c'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan'
config device
option name 'eth1'
option macaddr 'xx:xx:xx:xx:xx:48'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
option peerdns '0'
list dns '162.252.172.57'
list dns '149.154.159.92'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
config interface 'wlan'
option proto 'static'
option device 'wlan1'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config interface 'wg0'
option proto 'wireguard'
option private_key 'key here'
list addresses '10.14.0.2/16'
list dns '162.252.172.57'
list dns '149.154.159.92'
config wireguard_wg0
option description 'Delhi-India'
option public_key 'key here'
option private_key 'key here'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host 'in-del.prod.surfshark.com'
option endpoint_port '51820'
root@OpenWrt:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/a000000.wifi'
option channel '1'
option band '2g'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc/a800000.wifi'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt 5G'
option encryption 'psk2'
option key '********'
option network 'wlan'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
option start '100'
option limit '150'
option leasetime '12h'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'wlan'
option interface 'wlan'
option start '100'
option limit '150'
option leasetime '12h'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'lan'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'wlan'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'wlan'
option forward 'ACCEPT'
config forwarding
option src 'wlan'
option dest 'wan'
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wg0'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
config forwarding
option src 'wlan'
option dest 'vpn'
When wireguard goes up, the default route via wan is removed and rewritten via wg0. That's why LAN clients can no longer access the Internet (over wan, because there is no lan=>vpn forwarding).
You must set a metric for wg0 so that you can keep the default routes on both interfaces.
To route WLAN traffic through wg0, you can use the pbr package as suggested by @egc , or use pbr with netifd , which would be elementary in your case.
# /etc/config/network
config interface 'wg0'
option metric '10'
...
config rule
option src '192.168.3.0/24'
option lookup '100'
config route
option target '0.0.0.0/0'
option interface 'wg0'
option table '100'
In 22.03.5 you should be able to setup everything using LuCI.
1 Like
In wg0 interface, set Advanced Settings → Override IPv4 routing table and Override IPv6 routing table to 1000
In wlan interface, also set these to 1000
In Routing → IPv4 Rules add new rule
Incoming interface: wlan
Table 1000
Repeat the same for IPv6
If you need different DNS, you need to reconfigure default dnsmasq instance to listen only on lan and lo interfaces, and another instance with different configuration to listen only on wlan interface. Make sure to set the resolver address in DHCP and DNS → instance → Forwards → DNS Forwards, as it won't work properly if you set it in the interface, and set Ignore resolv file checkbox in Resolv & Hosts Files tab for this instance.
Not sure of your configuration, but for mine there's some kind of race condition between bringing up the interface and running dnsmasq, which results in non-working dnsmasq upon boot. I had to create an empty bridge and put wlan interface into it, only after which it started to work properly. This is true for current snapshot, maybe stable version doesn't have this bug.
Also make sure that Wireguard interface is in WAN firewall zone.
1 Like
Thank you all so much for all the help. As @pavelgl and @egc mentioned the problem was default routing being set to wg0.
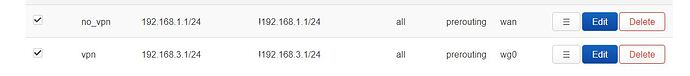
I use the policy based routing and it all works fine now. Here is configuration I'm using currently.
1 Like
system
April 15, 2024, 8:24am
10
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.