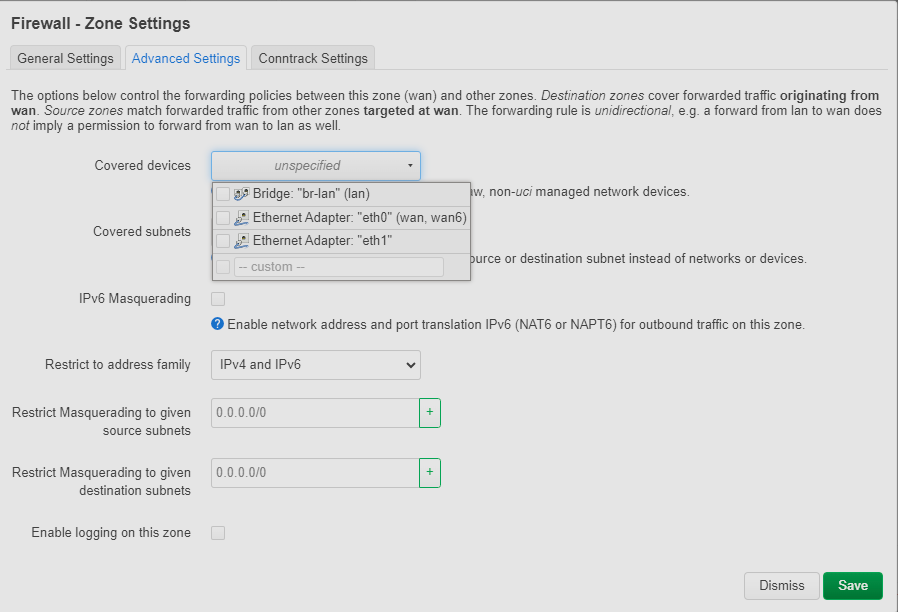
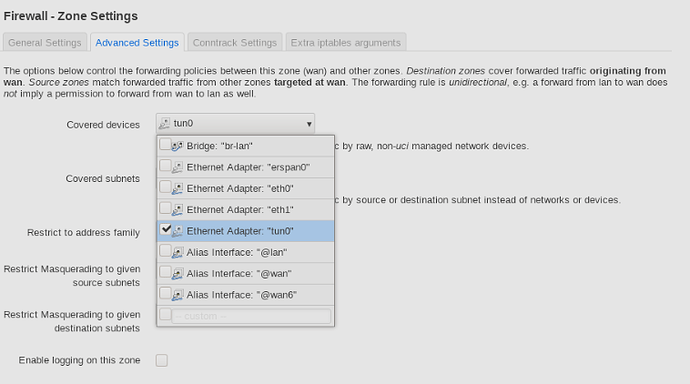
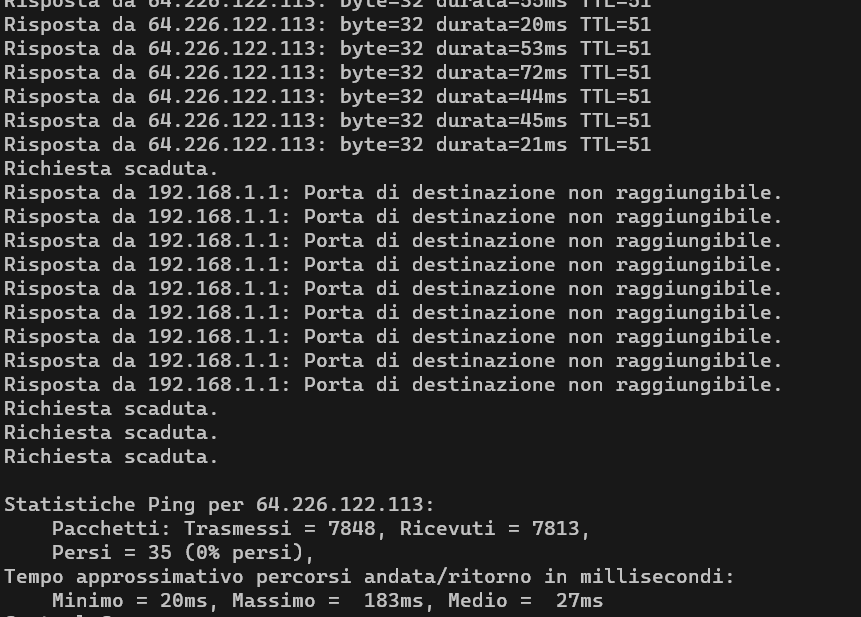
root@OpenWrt:~# logread | grep -i openvpn
Fri Feb 2 14:22:21 2024 daemon.warn openvpn(VPN)[1509]: DEPRECATED OPTION: ncp- disable. Disabling cipher negotiation is a deprecated debug feature that will be removed in OpenVPN 2.6
Fri Feb 2 14:22:21 2024 daemon.warn openvpn(VPN)[1509]: DEPRECATED OPTION: --ci pher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM ). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES -256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-f allback 'AES-256-CBC' to silence this warning.
Fri Feb 2 14:22:21 2024 daemon.notice openvpn(VPN)[1509]: OpenVPN 2.5.8 aarch64 -openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Fri Feb 2 14:22:21 2024 daemon.notice openvpn(VPN)[1509]: library versions: Ope nSSL 3.0.12 24 Oct 2023, LZO 2.10
Fri Feb 2 14:22:21 2024 daemon.warn openvpn(VPN)[1509]: NOTE: the current --scr ipt-security setting may allow this configuration to call user-defined scripts
Fri Feb 2 14:22:21 2024 daemon.notice openvpn(VPN)[1509]: Control Channel MTU p arms [ L:1621 D:1212 EF:38 EB:0 ET:0 EL:3 ]
Fri Feb 2 14:22:26 2024 daemon.err openvpn(VPN)[1509]: RESOLVE: Cannot resolve host address: 87-1-it.cg-dialup.net:443 (Try again)
Fri Feb 2 14:22:26 2024 daemon.notice openvpn(VPN)[1509]: Data Channel MTU parm s [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
Fri Feb 2 14:22:26 2024 daemon.notice openvpn(VPN)[1509]: Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,cipher AES-256 -CBC,auth SHA256,keysize 256,key-method 2,tls-client'
Fri Feb 2 14:22:26 2024 daemon.notice openvpn(VPN)[1509]: Expected Remote Optio ns String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,ciph er AES-256-CBC,auth SHA256,keysize 256,key-method 2,tls-server'
Fri Feb 2 14:22:31 2024 daemon.err openvpn(VPN)[1509]: RESOLVE: Cannot resolve host address: 87-1-it.cg-dialup.net:443 (Try again)
Fri Feb 2 14:22:31 2024 daemon.warn openvpn(VPN)[1509]: Could not determine IPv 4/IPv6 protocol
Fri Feb 2 14:22:31 2024 daemon.notice openvpn(VPN)[1509]: SIGUSR1[soft,init_ins tance] received, process restarting
Fri Feb 2 14:22:31 2024 daemon.notice openvpn(VPN)[1509]: Restart pause, 5 seco nd(s)
Fri Feb 2 14:22:37 2024 daemon.warn openvpn(VPN)[1509]: NOTE: the current --scr ipt-security setting may allow this configuration to call user-defined scripts
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Re-using SSL/TLS cont ext
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Control Channel MTU p arms [ L:1621 D:1212 EF:38 EB:0 ET:0 EL:3 ]
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Data Channel MTU parm s [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,cipher AES-256 -CBC,auth SHA256,keysize 256,key-method 2,tls-client'
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Expected Remote Optio ns String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,ciph er AES-256-CBC,auth SHA256,keysize 256,key-method 2,tls-server'
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: TCP/UDP: Preserving r ecently used remote address: [AF_INET]185.217.71.142:443
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Socket Buffers: R=[21 2992->212992] S=[212992->212992]
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: UDP link local: (not bound)
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: UDP link remote: [AF_ INET]185.217.71.142:443
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: TLS: Initial packet f rom [AF_INET]185.217.71.142:443, sid=e883e9af 478529be
Fri Feb 2 14:22:37 2024 daemon.warn openvpn(VPN)[1509]: WARNING: this configura tion may cache passwords in memory -- use the auth-nocache option to prevent thi s
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: VERIFY OK: depth=1, C =RO, L=Bucharest, O=CyberGhost S.A., CN=CyberGhost Root CA, emailAddress=info@cy berghost.ro
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: VERIFY KU OK
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Validating certificat e extended key usage
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: ++ Certificate has EK U (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: VERIFY EKU OK
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: VERIFY OK: depth=0, C N=rome-rack401.nodes.gen4.ninja
Fri Feb 2 14:22:37 2024 daemon.warn openvpn(VPN)[1509]: WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1569', remote='link-mtu 1553'
Fri Feb 2 14:22:37 2024 daemon.warn openvpn(VPN)[1509]: WARNING: 'keysize' is u sed inconsistently, local='keysize 256', remote='keysize 128'
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Control Channel: TLSv 1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, sign ature: RSA-SHA256
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: [rome-rack401.nodes.g en4.ninja] Peer Connection Initiated with [AF_INET]185.217.71.142:443
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: PUSH: Received contro l message: 'PUSH_REPLY,redirect-gateway def1,route-ipv6 2000::/3,dhcp-option DNS 10.0.0.243,route-gateway 10.12.4.1,topology subnet,ping 10,ping-restart 60,ifco nfig 10.12.4.42 255.255.255.0,peer-id 12'
Fri Feb 2 14:22:37 2024 daemon.warn openvpn(VPN)[1509]: WARNING: You have speci fied redirect-gateway and redirect-private at the same time (or the same option multiple times). This is not well supported and may lead to unexpected results
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Pushed option removed by filter: 'route-ipv6 2000::/3'
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: OPTIONS IMPORT: timer s and/or timeouts modified
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: OPTIONS IMPORT: --ifc onfig/up options modified
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: OPTIONS IMPORT: route options modified
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: OPTIONS IMPORT: route -related options modified
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: OPTIONS IMPORT: --ip- win32 and/or --dhcp-option options modified
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: OPTIONS IMPORT: peer- id set
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: OPTIONS IMPORT: adjus ting link_mtu to 1624
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Outgoing Data Channel : Cipher 'AES-256-CBC' initialized with 256 bit key
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Outgoing Data Channel : Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Incoming Data Channel : Cipher 'AES-256-CBC' initialized with 256 bit key
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: Incoming Data Channel : Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: net_route_v4_best_gw query: dst 0.0.0.0
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: net_route_v4_best_gw result: via 192.168.112.254 dev eth0
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: TUN/TAP device tun0 o pened
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: do_ifconfig, ipv4=1, ipv6=0
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: net_iface_mtu_set: mt u 1500 for tun0
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: net_iface_up: set tun 0 up
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: net_addr_v4_add: 10.1 2.4.42/24 dev tun0
Fri Feb 2 14:22:37 2024 daemon.notice openvpn(VPN)[1509]: /usr/libexec/openvpn- hotplug up VPN tun0 1500 1624 10.12.4.42 255.255.255.0 init
Fri Feb 2 14:22:37 2024 daemon.notice netifd: Interface 'OpenVPN' is enabled
Fri Feb 2 14:22:37 2024 daemon.notice netifd: Interface 'OpenVPN' has link conn ectivity
Fri Feb 2 14:22:42 2024 daemon.notice openvpn(VPN)[1509]: net_route_v4_add: 185 .217.71.142/32 via 192.168.112.254 dev [NULL] table 0 metric -1
Fri Feb 2 14:22:42 2024 daemon.notice openvpn(VPN)[1509]: net_route_v4_add: 0.0 .0.0/1 via 10.12.4.1 dev [NULL] table 0 metric -1
Fri Feb 2 14:22:42 2024 daemon.notice openvpn(VPN)[1509]: net_route_v4_add: 128 .0.0.0/1 via 10.12.4.1 dev [NULL] table 0 metric -1
Fri Feb 2 14:22:42 2024 daemon.notice openvpn(VPN)[1509]: Initialization Sequen ce Completed