Can we limit UPnP based on mac address or something?
I just want to use UPNP for my gaming console as it saves a hassle of setting it up but not allow a wider security issue by leaving it blanket wide for other devices on the network.
What information is in the XML formatted discovery and description events for UPnP?
Could validity of responses or information in these XML's be used with some sort of safe list of services or typical ports?
Yes I know the security floors and I'm aware of the implications of a device becoming compromised leading to further issues.
I'm happy with a balance of security/ connivence I would just like to omit devices that could be compromised it seems Miniupnpd does not have these options.
I just want to enable it for a specific group of trusted devices to minimize the chance of security issues (specifically gaming consoles in this case).
Right. It is done by the int_address option. This is ip based, so you’d need to set dhcp reservations accordingly.
1 Like
Oh ok CDIR notation surprising in a consumer orientated protocol for home use.
I'm guessing by the wiki there is no CDIR IPV6?
It would be nice to be able to tag MAC or IP addresses from the DHCP pool.
1 Like
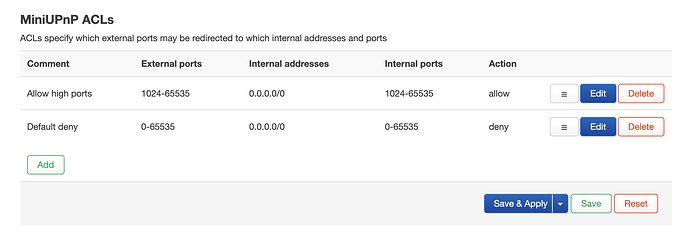
AFAIR you can limit the devices and WAN/on-device ports within the upnp config for OpenWrt. Just make sure your allowed upnp polices are listed above default deny.
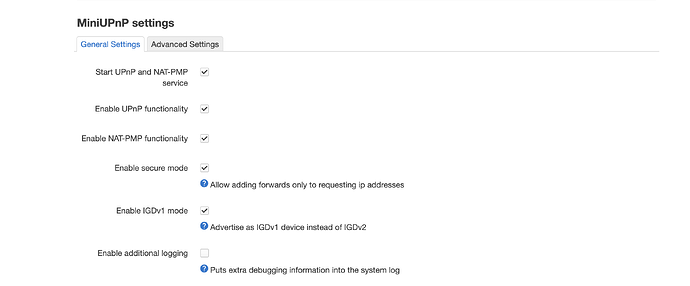
Yes, I've tried the luci-app-upnp app and it actually has the option by default to only allow opening/forwarding a port to the same IP that initiated the request:
Enable secure mode
Also, you can just setup your console with a static IP and limit the allowed range to that specific IP:
Seems to work pretty good on OpenWrt 23.05.3
I know of this feature but I'm wanting to block all devices from using upnp except for specific devices on my network.
Limiting the IP range should have a similar result.
However, you can also not use UPnP at all and forward all ports to your console instead: [Tutorial] How to add a device to DMZ on OpenWrt
Please know that whatever device you set this up for will be exposed to the Internet, so you need to make sure that it's safe.
In general, a console might be added in it, if anything
any game uses certain ports, there is no point in using upnp for the server, you need to open the ports.
If you just need to connect to the server, then you don’t need to open anything at all.
By opening a port for a server, you obviously take a risk, the server must be protected, upnp will not protect it, and it will not work stably through it.
I don’t know where you got this information about upnp, but this is old and false information written by someone when they didn’t know about the vulnerability yet
Problem is when you have multiple consoles as they all default to a specific port without manual intervention.
UPNP simplifies this as they will negotiate their own ports.
I know the security implications of using UPNP but I'm happy to mitigate this using secure mode and hopefully locking UPNP to specific MAC addresses of just consoles on my network.
I could also argue that leaving ports open manually is a security issue as UPNP will close them after a timeout period.
Just set static IPs for your consoles.
Currently I have:
PS5-WIFI: 192.168.1.108
PS5-LAN: 192.168.1.107
Xbox-One: 192.168.1.106
PS4-Wifi: 192.168.1.105
PS4-Wan: 192.168.1.104
Then I set UPNP in strict mode, and use the ACL list in UPNP config in LUCI to only allow those above IP addresses to use it, and deny everything else.
This way I can use whatever console I want wired or wireless and always get an open NAT.
I have been using UPnP on Openwrt with these rules for many years, I usually have the openwrt luci page up on one of my monitors at almost all times so I can always see whats on my network, and I have never seen upnp behave any different than expected, and only creates rules for those consoles when requested and denys everything else.
1 Like