For the past several days I've been struggling to implement miniupnpd on my EdgerouterX under OpenWRT.
While I initially presumed my problems getting redirects to map to be due to conflicting custom DSCP tagging scripts - I have since wiped my device, flashed it to 19.07.5 Stable and reconfigured it with regular luci-app-sqm and luci-app-upnp / miniupnpd - only to run into the same issues I had on my previous configuration.
- Manually forwarding all ports to my test device registers any and all as open in my port sniffer, so it does not appear to be an issue with my configuration beyond miniupnpd
I have attempted various configurations to troubleshoot the issue:
- option internal_iface 'lan' or 'LAN' or 'br-lan'
- option external_iface 'wan' or 'WAN' or 'eth0.2'
- option external_ip 'my public IP'
- option igdv1 '1' or '0'
- option ext_perform_stun=yes
- option use_stun = '0' or '1'
- option ipv6_disable '1'
With no success.
My current /etc/config/upnpd is:
config upnpd 'config'
option download '1024'
option upload '512'
option internal_iface 'lan'
option port '5000'
option upnp_lease_file '/var/run/miniupnpd.leases'
option igdv1 '1'
option ext_ip_reserved_ignore '1'
option uuid 'd1ea46d4-56f3-45ca-90b6-a6174b3958f0'
option log_output '1'
option ipv6_disable '1'
option enabled '1'
option enable_upnp '1'
option enable_natpmp '1'
config perm_rule
option action 'allow'
option comment 'Allow high ports'
option ext_ports '0-65535'
option int_ports '0-65535'
option int_addr '192.168.101.21'
My interfaces are:
br-lan Link encap:Ethernet HWaddr 74:83:C2:F8:B2:1A
inet addr:192.168.101.1 Bcast:192.168.101.255 Mask:255.255.255.0
inet6 addr: fd89:5c3:718c::1/60 Scope:Global
inet6 addr: fe80::7683:c2ff:fef8:b21a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1176005 errors:0 dropped:0 overruns:0 frame:0
TX packets:1212812 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:246052289 (234.6 MiB) TX bytes:1382728377 (1.2 GiB)
eth0 Link encap:Ethernet HWaddr 74:83:C2:F8:B2:1A
inet6 addr: fe80::7683:c2ff:fef8:b21a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:2377206 errors:0 dropped:0 overruns:0 frame:0
TX packets:2366111 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1647549162 (1.5 GiB) TX bytes:1648894608 (1.5 GiB)
Interrupt:20
eth0.1 Link encap:Ethernet HWaddr 74:83:C2:F8:B2:1A
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1176109 errors:0 dropped:0 overruns:0 frame:0
TX packets:1194471 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:246072777 (234.6 MiB) TX bytes:1373658255 (1.2 GiB)
eth0.2 Link encap:Ethernet HWaddr 74:83:C2:F8:B2:1B
inet addr:###.###.25.228 Bcast:203.129.25.255 Mask:255.255.254.0
inet6 addr: fe80::7683:c2ff:fef8:b21b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1184505 errors:0 dropped:0 overruns:0 frame:0
TX packets:1169017 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1357846727 (1.2 GiB) TX bytes:255869070 (244.0 MiB)
ifb4eth0.2 Link encap:Ethernet HWaddr 52:6B:3B:A2:5B:67
inet6 addr: ###::####:3bff:fea2:5b67/64 Scope:Link
UP BROADCAST RUNNING NOARP MTU:1500 Metric:1
RX packets:1192925 errors:0 dropped:0 overruns:0 frame:0
TX packets:1192925 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:32
RX bytes:1372579756 (1.2 GiB) TX bytes:1372579756 (1.2 GiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:5333 errors:0 dropped:0 overruns:0 frame:0
TX packets:5333 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:494961 (483.3 KiB) TX bytes:494961 (483.3 KiB)
And the output of my iptables-save command:
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:24:33 2021
*nat
:PREROUTING ACCEPT [8292:578522]
:INPUT ACCEPT [4306:295720]
:OUTPUT ACCEPT [1988:143983]
:POSTROUTING ACCEPT [2203:113806]
:MINIUPNPD - [0:0]
:MINIUPNPD-POSTROUTING - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_postrouting -s 192.168.101.0/24 -d 192.168.101.21/32 -m comment --comment "!fw3: Test (reflection)" -j SNAT --to-source 192.168.101.1
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_lan_prerouting -s 192.168.101.0/24 -d 203.129.25.228/32 -m comment --comment "!fw3: Test (reflection)" -j DNAT --to-destination 192.168.101.21
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -j MINIUPNPD-POSTROUTING
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
-A zone_wan_prerouting -m comment --comment "!fw3: Test" -j DNAT --to-destination 192.168.101.21
-A zone_wan_prerouting -j MINIUPNPD
COMMIT
# Completed on Sun Jan 10 11:24:33 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:24:33 2021
*raw
:PREROUTING ACCEPT [2310802:1581876629]
:OUTPUT ACCEPT [24402:7679978]
:zone_lan_helper - [0:0]
-A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
COMMIT
# Completed on Sun Jan 10 11:24:33 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:24:33 2021
*mangle
:PREROUTING ACCEPT [2310804:1581877238]
:INPUT ACCEPT [13061:1391179]
:FORWARD ACCEPT [2292243:1578532755]
:OUTPUT ACCEPT [24404:7680354]
:POSTROUTING ACCEPT [2316708:1586215167]
-A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sun Jan 10 11:24:33 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:24:33 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:MINIUPNPD - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -j MINIUPNPD
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -j MINIUPNPD
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sun Jan 10 11:24:33 2021
root@MAGI01:~# ^C
root@MAGI01:~# iptables-save
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:27:30 2021
*nat
:PREROUTING ACCEPT [42:5559]
:INPUT ACCEPT [22:1431]
:OUTPUT ACCEPT [14:936]
:POSTROUTING ACCEPT [2:142]
:MINIUPNPD - [0:0]
:MINIUPNPD-POSTROUTING - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -j MINIUPNPD-POSTROUTING
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
-A zone_wan_prerouting -j MINIUPNPD
COMMIT
# Completed on Sun Jan 10 11:27:30 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:27:30 2021
*raw
:PREROUTING ACCEPT [947:174102]
:OUTPUT ACCEPT [328:61085]
:zone_lan_helper - [0:0]
-A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
COMMIT
# Completed on Sun Jan 10 11:27:30 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:27:30 2021
*mangle
:PREROUTING ACCEPT [949:174206]
:INPUT ACCEPT [348:31678]
:FORWARD ACCEPT [592:138988]
:OUTPUT ACCEPT [331:61721]
:POSTROUTING ACCEPT [923:200709]
-A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sun Jan 10 11:27:30 2021
# Generated by iptables-save v1.8.3 on Sun Jan 10 11:27:30 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:MINIUPNPD - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -j MINIUPNPD
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -j MINIUPNPD
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sun Jan 10 11:27:30 2021
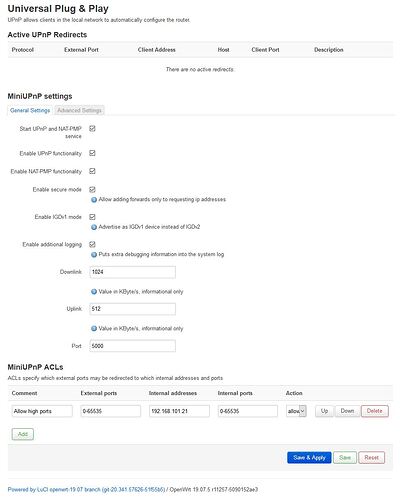
In LUCI my UPnP panel never shows any active redirects:
And my System log constantly shows:
Sun Jan 10 10:31:58 2021 daemon.debug miniupnpd[5591]: level=0 type=8
Sun Jan 10 10:31:58 2021 daemon.debug miniupnpd[5591]: ifindex = 7 192.168.101.1
Sun Jan 10 10:31:58 2021 daemon.debug miniupnpd[5591]: ST: urn:dial-multiscreen-org:service:dial:1 (ver=1)
Sun Jan 10 10:31:58 2021 daemon.info miniupnpd[5591]: SSDP M-SEARCH from 192.168.101.21:63735 ST: urn:dial-multiscreen-org:service:dial:1
Sun Jan 10 10:31:58 2021 daemon.debug miniupnpd[5591]: level=0 type=8
Sun Jan 10 10:31:58 2021 daemon.debug miniupnpd[5591]: ifindex = 7 192.168.101.1
Sun Jan 10 10:31:58 2021 daemon.debug miniupnpd[5591]: ST: urn:dial-multiscreen-org:service:dial:1 (ver=1)
Sun Jan 10 10:31:58 2021 daemon.info miniupnpd[5591]: SSDP M-SEARCH from 192.168.101.21:61160 ST: urn:dial-multiscreen-org:service:dial:1
Sun Jan 10 10:31:59 2021 daemon.debug miniupnpd[5591]: level=0 type=8
Sun Jan 10 10:31:59 2021 daemon.debug miniupnpd[5591]: ifindex = 7 192.168.101.1
Sun Jan 10 10:31:59 2021 daemon.debug miniupnpd[5591]: ST: urn:dial-multiscreen-org:service:dial:1 (ver=1)
Sun Jan 10 10:31:59 2021 daemon.info miniupnpd[5591]: SSDP M-SEARCH from 192.168.101.21:61160 ST: urn:dial-multiscreen-org:service:dial:1
Sun Jan 10 10:32:00 2021 daemon.debug miniupnpd[5591]: level=0 type=8
Sun Jan 10 10:32:00 2021 daemon.debug miniupnpd[5591]: ifindex = 7 192.168.101.1
Sun Jan 10 10:32:00 2021 daemon.debug miniupnpd[5591]: ST: urn:dial-multiscreen-org:service:dial:1 (ver=1)
Sun Jan 10 10:32:00 2021 daemon.info miniupnpd[5591]: SSDP M-SEARCH from 192.168.101.21:61160 ST: urn:dial-multiscreen-org:service:dial:1
Sun Jan 10 10:32:01 2021 daemon.debug miniupnpd[5591]: level=0 type=8
Sun Jan 10 10:32:01 2021 daemon.debug miniupnpd[5591]: ifindex = 7 192.168.101.1
Sun Jan 10 10:32:01 2021 daemon.debug miniupnpd[5591]: ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1 (ver=1)
Sun Jan 10 10:32:01 2021 daemon.info miniupnpd[5591]: SSDP M-SEARCH from 192.168.101.21:65279 ST: urn:schemas-upnp-org:device:InternetGatewayDevice:1
Sun Jan 10 10:32:01 2021 daemon.info miniupnpd[5591]: Single search found
Sun Jan 10 10:32:01 2021 daemon.debug miniupnpd[5591]: SendSSDPResponse(): 0 bytes to 192.168.101.21:65279 ST: HTTP/1.1 200 OK
Any help would be appreciated since I am quite lost here
Thanks