I'm using an Archer C7 v5 as a dummy AP in my network.
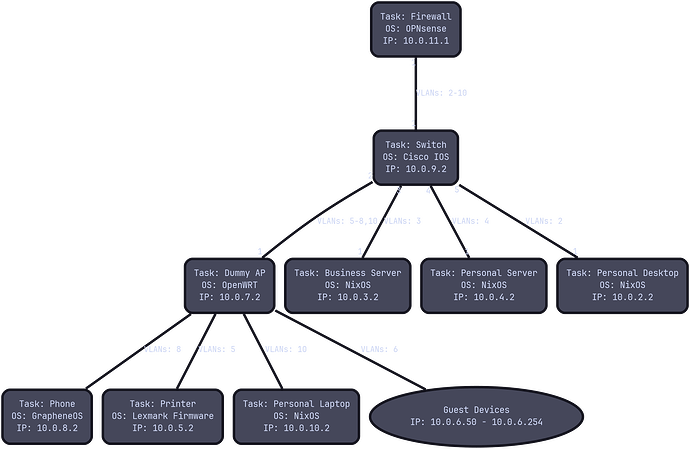
This is my topology:
This is my /etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '5'
option ports '0t 2t'
config switch_vlan
option device 'switch0'
option vlan '6'
option ports '0t 2t'
config switch_vlan
option device 'switch0'
option vlan '7'
option ports '0t 2t'
config switch_vlan
option device 'switch0'
option vlan '8'
option ports '0t 2t'
config device
option name 'br_printer'
option type 'bridge'
list ports 'eth0.5'
config device
option name 'br_guest'
option type 'bridge'
list ports 'eth0.6'
config device
option name 'br_skynet'
option type 'bridge'
list ports 'eth0.8'
config interface 'printer'
option device 'br_printer'
option proto 'none'
config interface 'guest'
option device 'br_guest'
option proto 'none'
config interface 'management'
option device 'eth0.7'
option proto 'static'
option ipaddr '10.0.7.2'
option netmask '255.255.255.0'
option gateway '10.0.7.1'
option dns '10.0.7.1'
config interface 'skynet'
option device 'br_skynet'
option proto 'none'
This is my /etc/config/wireless:
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option disabled '0'
config wifi-iface 'radio0_skynet'
option device 'radio0'
option network 'skynet'
option mode 'ap'
option ssid 'skynet'
option encryption 'sae'
option key <some-password>
option hidden '1'
config wifi-iface 'radio0_guest'
option device 'radio0'
option network 'guest'
option mode 'ap'
option ssid 'skynet-guest'
option encryption 'sae'
option key <some-password>
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option disabled '0'
config wifi-iface 'radio1_printer'
option device 'radio1'
option network 'printer'
option mode 'ap'
option ssid 'skynet-printer'
option encryption 'sae'
option key <some-password>
option hidden '1'
And these are the relevant port configurations on the switch that sits between OPNsense and OpenWRT:
interface GigabitEthernet1/0/1
switchport trunk encapsulation dot1q
switchport trunk native vlan 99
switchport trunk allowed vlan 2-10
switchport mode trunk
!
interface GigabitEthernet1/0/2
switchport trunk encapsulation dot1q
switchport trunk native vlan 99
switchport trunk allowed vlan 5-8
switchport mode trunk
!
interface GigabitEthernet1/0/3
switchport trunk encapsulation dot1q
switchport trunk native vlan 99
switchport trunk allowed vlan 3
switchport mode trunk
spanning-tree portfast trunk
!
interface GigabitEthernet1/0/4
switchport access vlan 4
switchport mode access
!
interface GigabitEthernet1/0/5
switchport access vlan 2
switchport mode access
There's some slight deviation between the code and diagram, but it shouldn't be problematic as it's not on the path that I'm having trouble getting data to travel. That deviation is just that the laptop and phone have their own VLANs in the diagram but share a VLAN in the config file, and also the port to my business server is a trunk in the switch config but not in the diagram. Probably not relevant, just noting.
Today I updated to OpenWRT 24.10.1, initially by using auc but that did something very weird. It locked me out of the OpenWRT management VLAN (7) yet left the rest of the network intact. I spent many hours trying to get the management VLAN back to no avail. Then I had a look around online and noticed auc is being phased out for owut as well as opkg for apk. At this point I worried that maybe I was doing things in a way that's no longer recommended, so I figured I'd manually flash to 24.10.1, so I did that via failsafe mode and scp. Still the problem persistent. At this point I've cut my config down to something very minimal, no wireless and just a management VLAN:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '7'
option ports '0t 2t'
config interface 'management'
option device 'eth0.7'
option proto 'static'
option ipaddr '10.0.7.2'
option netmask '255.255.255.0'
option gateway '10.0.7.1'
option dns '10.0.7.1'
But still I can't access the management VLAN. I'm also sure my firewall rules in OPNsense aren't blocking anything, as I can see with the OPNsense packet capture tool that when I ping from a device with appropriate firewall rules packets show up on VLAN 7.
If anyone can give me some advice on how to troubleshoot regaining access to VLAN 7, that would be helpful.