Hi,
just a few days ago I found out OpenWRT while looking for a way to solve my problem: how to connect devices from two houses as if they were in the same network?
To play with the networks and understand (hopefully) how things work, I'm using GNS3 and routers with OpenWrt19.07.2.
I found a similar answer here (GRE tunneling between two OpenWrt routers). However, I still don't know how to set up GRE correct (or I'm missing some very basic stuff - I'm nowbie).
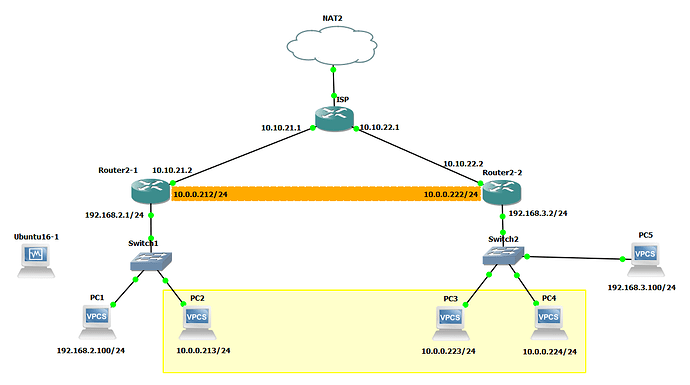
Here is the topology
Router2-1 and Router2-2 are the houses, the part above them belong to my ISP (houses are inside their network, will be able to ping each other, but I dunno what devices are on this part)
My final goal is to make PC2, PC3, PC4 see each other as if being in the same network.
However, as the first stage, I would like to connect Router2-1 and Router 2-2 through GRE tunnel and validate if they can speak to each other.
Router2-1
/etc/config/network
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth1'
option proto 'static'
option ipaddr '10.10.21.2'
option netmask '255.255.255.0'
option gateway '10.10.21.1'
list dns '10.10.21.1'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config interface 'gt'
option proto 'gre'
option peeraddr '10.10.22.2'
option ipaddr '10.10.21.2'
option tunlink 'wan'
/etc/config/firewall
config rule
option src 'wan'
option name 'Allow-GPR'
option family 'ipv4'
option target 'ACCEPT'
option proto 'gre'
Router2-2
/etc/config/network
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.3.2'
config interface 'wan'
option ifname 'eth1'
option proto 'static'
option ipaddr '10.10.22.2'
option gateway '10.10.22.1'
option netmask '255.255.255.0'
list dns '10.10.22.1'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config interface 'gt'
option proto 'gre'
option peeraddr '10.10.21.2'
option ipaddr '10.10.22.2'
option tunlink 'wan'
/etc/config/firewall
config rule
option name Allow-GRE
option src 'wan'
option family 'ipv4'
option target 'ACCEPT'
option proto 'gre'
When I try from Router2-2
root@OpenWrt:/# traceroute 10.10.21.2
traceroute to 10.10.21.2 (10.10.21.2), 30 hops max, 46 byte packets
1 10.10.22.1 (10.10.22.1) 0.430 ms 0.297 ms 0.343 ms
2 10.10.21.2 (10.10.21.2) 0.735 ms 0.610 ms 0.644 ms
If the tunnel is set up correctly, I would expect that only 10.10.21.2 is on the list.
My current questions are:
1. Is my understanding of the traceroute output correct?
2. What is missing in (or wrong with) these configs?
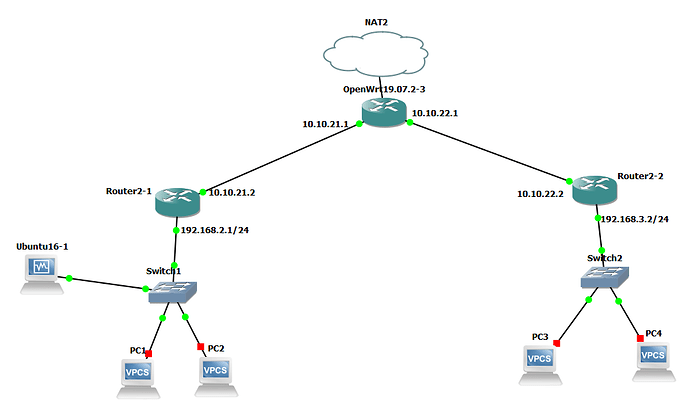
 (I thought I tried this before, probably I did sth else wrong)
(I thought I tried this before, probably I did sth else wrong)