Hey there! I've been working away at this for a while now, still no luck...
I looked at a bunch of documentation and other posts on the forum, still not sure what I'm missing.
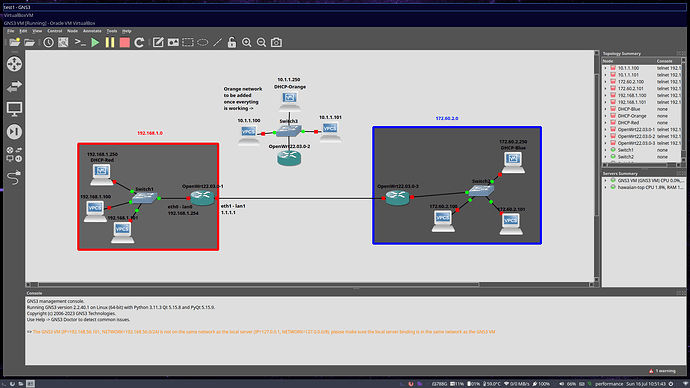
I'm simulating networks using GNS3, I use OpenWRT for my routers and host all instances on a VM. There are currently 2 LANs, 192.168.1.0 and 172.60.2.0, each using an OpenWRT router. I refer to 192.168.1.0 as "Red" and 172.60.2.0 as "Blue."
As for the configs, this is what I have at the moment:
/etc/config/network (Red)
config interface
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1/8'
config globals 'globals'
option ula_prefix 'fd05:321d:f12a::/48'
config interface 'lan0'
option device 'eth0'
option proto 'static'
option ipaddr '192.168.1.254/24'
config interface 'lan1'
option device 'eth1'
option proto 'static'
option ipaddr '1.1.1.1/29'
config route 'routeBlue'
option interface 'lan1'
option target '172.60.2.0/24'
option gateway '1.1.1.2'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
/etc/config/network (Blue)
config interface
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1/8'
config globals 'globals'
option ula_prefix 'fdae:a7dd:eae9::/48'
config interface 'lan0'
option device 'eth0'
option proto 'static'
option ipaddr '172.60.2.254/24'
config interface 'lan1'
option device 'eth1'
option proto 'static'
option ipaddr '1.1.1.2/29'
config route 'routeBlue'
option interface 'lan1'
option target '192.168.1.0/24'
option gateway '1.1.1.1'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
/etc/config/firewall (Red and Blue)
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
confing forwarding
option src 'lan'
option dest 'wan'
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# *** IPv6 stuff that I don't think matters rn since I'm working with IPv4 ***
As for the topography, each LAN has a DHCP server, the router, and some devices (hosts 100 and 101) connected to a switch. The red and blue routers are physically connected and are supposed to communicate over the backbone 1.1.1.0.
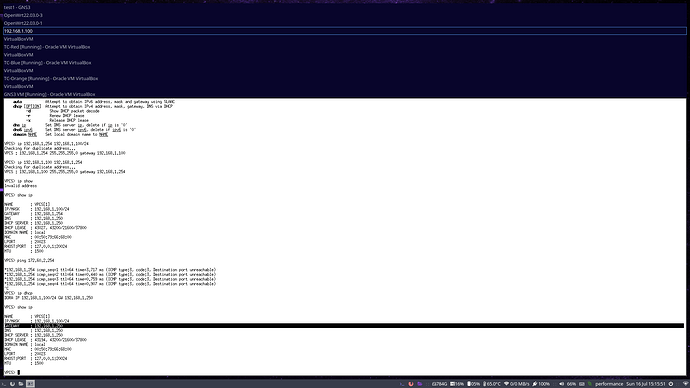
In its current state, hosts 100 and 101 on either LAN can ping each other and their respective routers. The routers can ping each other. However, 100 red cannot ping 100 blue, nor can 100 red ping the blue router, and I don't know how to fix this.
Any and all help is appreciated!