I'm trying to add dynamic VLANs to an SSID with RADIUS assignment and for the most part, everything seems to be working except my devices connecting via wireless on any VLAN other than the default (VLAN1) are not able to get IPs.
I am able to use any VLAN assigned to a physical port and it works fine. Assignments to VLAN1 work with no problems on the wireless network.
If I manually assign the VLAN's network interface to the wireless SSID, all VLANs can work.
My environment is as follows:
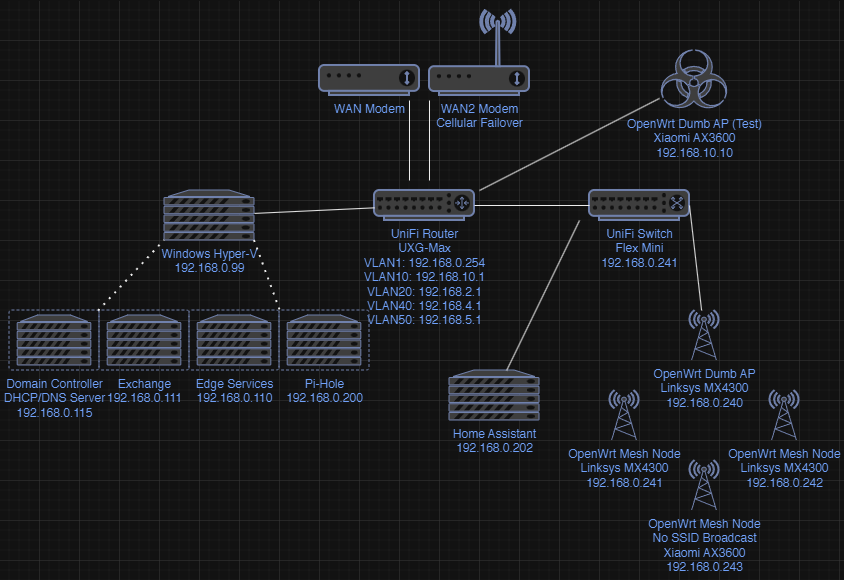
Xiaomi AX3600 running OpenWrt SNAPSHOT r28228+8-207bfee855
Code includes two modifications from master: 1) PR 16070 is brought in for Linksys MX4300 support. 2) ath11k is patched to support AP-VLAN
built with full wpad-openssl
Device is a dumb AP connected to a UniFi UXG-Max gateway.
This device is the DHCP server for VLANs 10, 20, 40, and 50
Windows 2019 DHCP server sits on the other side of this gateway running DHCP for VLAN1
Radius is running locally since the one built into UniFi won't let me default unknown clients to authenticate with a VLAN1 assignment. In system logs I am able to see the authentications running successfully and appropriately applying VLAN assignments. If I remove the hostapd vlan file I can see the vlans being auto-applied to the wlan interface as clients attempt to connect.
In these configs, I have 3 SSIDs setup across two different radios for the sake of testing. It includes a duplicate configuration for the sake of testing on both ath10k and ath11k (since ath11k is using an unofficial patch), and a 2nd SSID riding on ath11k 5ghz without dynamic vlan, tied directly to one of the afflicted vlans (successfully).
OpenWrt-10:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd1f:1574:f95d::/48'
config interface 'lan'
option device 'br-vlan1'
option proto 'none'
config interface 'mgmt'
option proto 'static'
option device 'br-vlan10'
option ipaddr '192.168.10.10'
option netmask '255.255.255.0'
option gateway '192.168.10.1'
list dns '192.168.10.1'
config device
option type 'bridge'
option name 'br-vlan1'
option igmp_snooping '1'
list ports 'lan1'
list ports 'lan3'
list ports 'wan'
config device
option type 'bridge'
option name 'br-vlan10'
option igmp_snooping '1'
list ports 'wan.10'
config interface 'kids'
option proto 'none'
option device 'br-vlan20'
config interface 'Google'
option proto 'none'
option device 'br-vlan40'
config interface 'iot'
option proto 'none'
option device 'br-vlan50'
config device
option type '8021q'
option ifname 'wan'
option vid '1'
option name 'wan.1'
config device
option type '8021q'
option ifname 'wan'
option vid '20'
option name 'wan.20'
config device
option type '8021q'
option ifname 'wan'
option vid '40'
option name 'wan.40'
config device
option type '8021q'
option ifname 'wan'
option vid '50'
option name 'wan.50'
config device
option type '8021q'
option ifname 'wan'
option vid '10'
option name 'wan.10'
config device
option type 'bridge'
option name 'br-vlan20'
option igmp_snooping '1'
list ports 'lan2'
list ports 'wan.20'
config device
option type 'bridge'
option name 'br-vlan40'
list ports 'wan.40'
option igmp_snooping '1'
config device
option type 'bridge'
option name 'br-vlan50'
list ports 'wan.50'
option igmp_snooping '1'
OpenWrt-10:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'soc@0/20000000.pci/pci0000:00/0000:00:00.0/0000:01:00.0'
option band '5g'
option channel '36'
option htmode 'VHT80'
option country 'US'
option cell_density '0'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc@0/c000000.wifi'
option band '5g'
option channel '36'
option htmode 'HE80'
option country 'US'
option cell_density '0'
config wifi-device 'radio2'
option type 'mac80211'
option path 'platform/soc@0/c000000.wifi+1'
option band '2g'
option channel '1'
option htmode 'HE20'
option disabled '1'
config wifi-iface 'wifinet0'
option device 'radio1'
option ifname 'wlan0'
option mode 'ap'
option ssid 'test1'
option encryption 'psk2'
option key '11111111'
option auth_server '192.168.10.10'
option auth_secret 'wowsecret'
option vlan_file '/etc/config/hostapd0.vlan'
option dynamic_vlan '2'
option vlan_naming '0'
option vlan_bridge 'br-vlan'
config wifi-iface 'wifinet1'
option device 'radio1'
option mode 'ap'
option ssid 'test2'
option encryption 'psk2'
option key '11111111'
option network 'kids'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'test_9887'
option encryption 'psk2'
option key '11111111'
option ifname 'wlan1'
option auth_server '192.168.10.10'
option auth_secret 'wowsecret'
option vlan_file '/etc/config/hostapd1.vlan'
option dynamic_vlan '2'
option vlan_naming '0'
option vlan_bridge 'br-vlan'
OpenWrt-10:~# cat /etc/config/hostapd0.vlan
1 wlan0.1 br-vlan1
20 wlan0.20 br-vlan20
40 wlan0.40 br-vlan40
50 wlan0.50 br-vlan50
10 wlan0.10 br-vlan10
OpenWrt-10:~# cat /etc/config/hostapd1.vlan
1 wlan1.1 br-vlan1
20 wlan1.20 br-vlan20
40 wlan1.40 br-vlan40
50 wlan1.50 br-vlan50
10 wlan1.10 br-vlan10
OpenWrt-10:~# brctl show
bridge name bridge id STP enabled interfaces
br-vlan20 7fff.88c397c155eb no wlan0.20
wan.20
phy1-ap0
lan2
wlan1.20
br-vlan10 7fff.88c397159787 no wlan0.10
wan.10
wlan1.10
br-vlan1 7fff.88c397c155eb no wlan1.1
wan
wlan0.1
lan3
lan1
br-vlan50 7fff.88c397159787 no wan.50
wlan1.50
wlan0.50
br-vlan40 7fff.88c397159787 no wan.40
wlan1.40
wlan0.40
Any education here would be appreciated!