Hello,
I just flashed a Netgear R6100 router with OpenWrt 22. My goal is to set up a client VPN connection on this router via ProtonVPN.
I followed the steps of this tutorial : [Link to ProtonVPN tutorial for OpenWrt]
However, it doesn't work. OpenVPN seems to establish the VPN connection, but I just can't reach internet with the devices connected to the router.
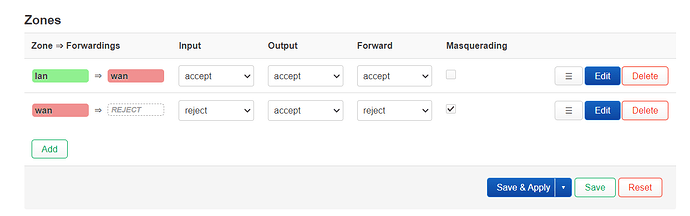
Here are the logs and some screenshots of my configuration in LuCI :
Sat Jul 15 12:59:58 2023 daemon.info dnsmasq-dhcp[1]: DHCPOFFER(br-lan) 192.168.1.127 98:29:a6:48:05:a1
Sat Jul 15 12:59:58 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.127 98:29:a6:48:05:a1
Sat Jul 15 12:59:58 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.127 98:29:a6:48:05:a1 LAPTOP-BOVVFERS
Sat Jul 15 13:03:39 2023 user.info : luci: accepted login on / for root from 192.168.1.127
Sat Jul 15 13:09:49 2023 user.info kernel: [ 695.746622] kmodloader: loading kernel modules from /etc/modules.d/*
Sat Jul 15 13:09:49 2023 kern.info kernel: [ 695.764896] tun: Universal TUN/TAP device driver, 1.6
Sat Jul 15 13:09:49 2023 user.info kernel: [ 695.782925] kmodloader: done loading kernel modules from /etc/modules.d/*
Sat Jul 15 13:20:49 2023 daemon.warn openvpn(CH)[5254]: DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: OpenVPN 2.5.7 mips-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: library versions: OpenSSL 1.1.1u 30 May 2023, LZO 2.10
Sat Jul 15 13:20:49 2023 daemon.warn openvpn(CH)[5254]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: TCP/UDP: Preserving recently used remote address: [AF_INET]185.159.157.7:5060
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: Socket Buffers: R=[180224->180224] S=[180224->180224]
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: UDP link local: (not bound)
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: UDP link remote: [AF_INET]185.159.157.7:5060
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: TLS: Initial packet from [AF_INET]185.159.157.7:5060, sid=77261639 06a03a1e
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: VERIFY OK: depth=2, C=CH, O=ProtonVPN AG, CN=ProtonVPN Root CA
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: VERIFY OK: depth=1, C=CH, O=ProtonVPN AG, CN=ProtonVPN Intermediate CA 1
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: VERIFY KU OK
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: Validating certificate extended key usage
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: ++ Certificate has EKU (str) 1.3.6.1.5.5.8.2.2, expects TLS Web Server Authentication
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: ++ Certificate has EKU (oid) 1.3.6.1.5.5.8.2.2, expects TLS Web Server Authentication
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: VERIFY EKU OK
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: VERIFY OK: depth=0, CN=node-ch-03.protonvpn.net
Sat Jul 15 13:20:49 2023 daemon.warn openvpn(CH)[5254]: WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1633', remote='link-mtu 1634'
Sat Jul 15 13:20:49 2023 daemon.warn openvpn(CH)[5254]: WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo'
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, signature: RSA-SHA256
Sat Jul 15 13:20:49 2023 daemon.notice openvpn(CH)[5254]: [node-ch-03.protonvpn.net] Peer Connection Initiated with [AF_INET]185.159.157.7:5060
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: SENT CONTROL [node-ch-03.protonvpn.net]: 'PUSH_REQUEST' (status=1)
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: PUSH: Received control message: 'PUSH_REPLY,dhcp-option DNS 10.39.0.1,sndbuf 524288,rcvbuf 524288,redirect-gateway def1,explicit-exit-notify,comp-lzo no,route-gateway 10.39.0.1,topology subnet,ping 10,ping-restart 60,socket-flags TCP_NODELAY,ifconfig 10.39.0.7 255.255.0.0,peer-id 1507333,cipher AES-256-GCM'
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: timers and/or timeouts modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: explicit notify parm(s) modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: compression parms modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: --sndbuf/--rcvbuf options modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: Socket Buffers: R=[180224->360448] S=[180224->360448]
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: --socket-flags option modified
Sat Jul 15 13:20:50 2023 daemon.warn openvpn(CH)[5254]: NOTE: setsockopt TCP_NODELAY=1 failed
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: --ifconfig/up options modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: route options modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: route-related options modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: peer-id set
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: adjusting link_mtu to 1656
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: OPTIONS IMPORT: data channel crypto options modified
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: Data Channel: using negotiated cipher 'AES-256-GCM'
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: net_route_v4_best_gw query: dst 0.0.0.0
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: net_route_v4_best_gw result: via 192.168.1.1 dev eth1
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: TUN/TAP device tun0 opened
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: net_iface_mtu_set: mtu 1500 for tun0
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: net_iface_up: set tun0 up
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: net_addr_v4_add: 10.39.0.7/16 dev tun0
Sat Jul 15 13:20:50 2023 daemon.notice openvpn(CH)[5254]: /usr/libexec/openvpn-hotplug up CH tun0 1500 1584 10.39.0.7 255.255.0.0 init
Sat Jul 15 13:20:51 2023 daemon.notice openvpn(CH)[5254]: net_route_v4_add: 185.159.157.7/32 via 192.168.1.1 dev [NULL] table 0 metric -1
Sat Jul 15 13:20:51 2023 daemon.notice openvpn(CH)[5254]: net_route_v4_add: 0.0.0.0/1 via 10.39.0.1 dev [NULL] table 0 metric -1
Sat Jul 15 13:20:51 2023 daemon.notice openvpn(CH)[5254]: net_route_v4_add: 128.0.0.0/1 via 10.39.0.1 dev [NULL] table 0 metric -1
Sat Jul 15 13:20:51 2023 daemon.warn openvpn(CH)[5254]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sat Jul 15 13:20:51 2023 daemon.notice openvpn(CH)[5254]: Initialization Sequence Completed
I googled my problem and browsed a lot of topics on this forum concerning the issue but I can't seem to find the issue.
I am super grateful for any help you guys could give to me ![]()