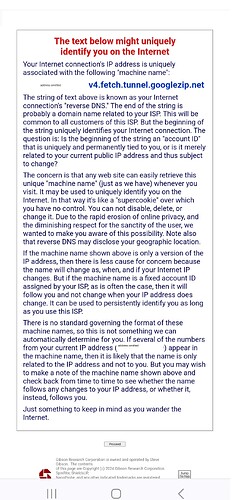
Hi,
I am unable to access the following port scanner on any of my devices on my home network.
I was able to access the scanner yesterday at 1pm CT.
If I connect to VPN I am able to access the page and run the port scanner. I do not get the message from google.
URL: https://www.grc.com/x/ne.dll?bh0bkyd2
Home Page: http://grc.com/default.htm
I omitted the IP address for security reasons.
Error:
<center>
<!-- OPEN THE PAGE-LENGTH CONTAINMENT TABLE -->
<table width="85%" border="0" cellpadding="0" cellspacing="0"><tr><td><font color="#000080" face="Verdana,Arial,Helvetica,Sans-Serif,MS Sans Serif" size="-1"><img src="/image/transpixel.gif" width=1 height=15 border="0">
<br>
<center><font color="#707070" size="+1">The Network Administrators for:<br><font color="#900050" size="+2"><b>Google Web Accelerator</b></font><br>have asked us not to probe their network.</font>
<br><img src="/image/transpixel.gif" width=1 height=10 border="0"><br><img src="/image/reddot.gif" width=33 height=34 border="0"></center>
<p>
The IP address we have found for your machine (<b>**ip.add.ress.omitted**</b>) resides within the network belonging to <b>Google Web Accelerator</b>. The administrators of this network detected the scans and probings of this ShieldsUP! site and have asked us to please desist from any future contact with systems within their network. Thus, we are unable to provide you with any additional information.
<p>
You should feel confident, however, in the knowledge that your network administration is actively monitoring external Internet access, including all "scans and probes" of the machines within their network. Your machine's connection to the Internet is, therefore, being well managed and tended by your network's administrators.
<p>
<img src="/image/darkredpixel.gif" width="100%" height=4 border="0">
<img src="/image/transpixel.gif" width=1 height=5 border="0"><br>
<b>If you wish to explore this ShieldsUP! site further</b>, with the understanding that it's active probing technology will not be available to you, you may use the following link to skip past the active content, entering at page #2 of the site, to read through the balance of the site's content.
<p>
<center><font size="+2"><b><a href="/su-explain.htm">Passive ShieldsUP! Entry</a></b></font></center>
<p>
And thanks for your interest in our work!
<!-- ------------ CLOSE THE PAGE-LENGTH CONTAINMENT TABLE ---------------- -->
</font></td></tr></table>
</center><br /><table border="0" cellpadding="0" cellspacing="0"><tr><td><a href="#top"><img src="/image/grc-icon.gif" width="51" height="51" border="0" alt="Jump to top of page" title="Jump to top of page" /></a></td><td><div style="margin:0 20px;"><font size="-2" color="#777777">Gibson Research Corporation is owned and operated by Steve Gibson. The contents<br />of this page are Copyright (c) 2024 Gibson Research Corporation. SpinRite, ShieldsUP,<br />NanoProbe, and any other indicated trademarks are registered trademarks of Gibson<br />Research Corporation, Laguna Hills, CA, USA. GRC's web and customer <a href="https://www.grc.com/privacy.htm" target="_top">privacy policy</a>.</font></div></td><td><a href="#top"><img src="/image/jumptotop.png" width="52" height="38" border="0" alt="Jump to top of page" title="Jump to top of page" /></a></td></tr></table><br />
</center></body></html>
Do I need to whitelist 4.79.142.192 - 4.79.142.207 in my OpenWRT router?
Output of this command: cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
list network 'wan'
option masq '1'
option input 'DROP'
option forward 'DROP'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option family 'ipv4'
list icmp_type 'echo-request'
option target 'DROP'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option family 'ipv4'
config zone
option name 'iot'
option output 'ACCEPT'
list network 'iot'
option input 'DROP'
option forward 'DROP'
config forwarding
option src 'iot'
option dest 'wan'
config rule
option name 'IOT-DHCP-DNS'
option src 'iot'
option target 'ACCEPT'
option dest_port '53 67'
list proto 'udp'
config forwarding
option src 'lan'
option dest 'iot'
output of cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
config device
option name 'eth1'
option macaddr 'omitted'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option delegate '0'
option ipaddr '192.168.1.1'
option ipv6 'off'
option device 'eth1'
config device
option name 'eth0'
option macaddr 'Omitted'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
option ipv6 '0'
option peerdns '0'
option delegate '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
config interface 'iot'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option device 'eth1.10'
output of nft list ruleset
table inet fw4 {
ct helper ftp {
type "ftp" protocol tcp
l3proto inet
}
chain input {
type filter hook input priority filter; policy accept;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
ct state invalid drop comment "!fw4: Drop flows with invalid conntrack state"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname "eth1" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "eth0" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic"
iifname "eth1.10" jump input_iot comment "!fw4: Handle iot IPv4/IPv6 input traffic"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
ct state invalid drop comment "!fw4: Drop flows with invalid conntrack state"
iifname "eth1" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "eth0" jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
iifname "eth1.10" jump forward_iot comment "!fw4: Handle iot IPv4/IPv6 forward traffic"
jump handle_reject
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
ct state invalid drop comment "!fw4: Drop flows with invalid conntrack state"
oifname "eth1" jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "eth0" jump output_wan comment "!fw4: Handle wan IPv4/IPv6 output traffic"
oifname "eth1.10" jump output_iot comment "!fw4: Handle iot IPv4/IPv6 output traffic"
}
chain prerouting {
type filter hook prerouting priority filter; policy accept;
iifname "eth1" jump helper_lan comment "!fw4: Handle lan IPv4/IPv6 helper assignment"
iifname "eth1.10" jump helper_iot comment "!fw4: Handle iot IPv4/IPv6 helper assignment"
}
chain handle_reject {
meta l4proto tcp reject with tcp reset comment "!fw4: Reject TCP traffic"
reject comment "!fw4: Reject any other traffic"
}
chain syn_flood {
limit rate 25/second burst 50 packets return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
chain input_lan {
meta nfproto ipv4 meta l4proto igmp counter packets 748 bytes 26064 accept comment "!fw4: ubus:igmpproxy[instance1] rule 3"
jump accept_from_lan
}
chain output_lan {
jump accept_to_lan
}
chain forward_lan {
jump accept_to_wan comment "!fw4: Accept lan to wan forwarding"
jump accept_to_iot comment "!fw4: Accept lan to iot forwarding"
jump accept_to_lan
}
chain helper_lan {
tcp dport 21 ct helper set "ftp" comment "!fw4: FTP passive connection tracking"
}
chain accept_from_lan {
iifname "eth1" counter packets 3008 bytes 213475 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain accept_to_lan {
oifname "eth1" counter packets 489 bytes 15648 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain drop_to_lan {
oifname "eth1" counter packets 0 bytes 0 drop comment "!fw4: drop lan IPv4/IPv6 traffic"
}
chain input_wan {
meta nfproto ipv4 meta l4proto igmp counter packets 16 bytes 576 accept comment "!fw4: ubus:igmpproxy[instance1] rule 0"
meta nfproto ipv4 udp dport 68 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCP-Renew"
icmp type echo-request counter packets 0 bytes 0 drop comment "!fw4: Allow-Ping"
meta nfproto ipv4 meta l4proto igmp counter packets 0 bytes 0 accept comment "!fw4: Allow-IGMP"
jump drop_from_wan
}
chain output_wan {
jump accept_to_wan
}
chain forward_wan {
meta l4proto udp ip daddr 239.255.255.250 counter packets 0 bytes 0 jump drop_to_lan comment "!fw4: ubus:igmpproxy[instance1] rule 1"
meta l4proto udp ip daddr 224.0.0.0/4 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: ubus:igmpproxy[instance1] rule 2"
meta nfproto ipv4 meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
meta nfproto ipv4 udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
jump drop_to_wan
}
chain accept_to_wan {
oifname "eth0" counter packets 4872 bytes 1219138 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain drop_from_wan {
iifname "eth0" counter packets 1391 bytes 199563 drop comment "!fw4: drop wan IPv4/IPv6 traffic"
}
chain drop_to_wan {
oifname "eth0" counter packets 0 bytes 0 drop comment "!fw4: drop wan IPv4/IPv6 traffic"
}
chain input_iot {
udp dport { 53, 67 } counter packets 128 bytes 15091 accept comment "!fw4: IOT-DHCP-DNS"
jump drop_from_iot
}
chain output_iot {
jump accept_to_iot
}
chain forward_iot {
jump accept_to_wan comment "!fw4: Accept iot to wan forwarding"
jump drop_to_iot
}
chain helper_iot {
tcp dport 21 ct helper set "ftp" comment "!fw4: FTP passive connection tracking"
}
chain accept_to_iot {
oifname "eth1.10" counter packets 18 bytes 3944 accept comment "!fw4: accept iot IPv4/IPv6 traffic"
}
chain drop_from_iot {
iifname "eth1.10" counter packets 1271 bytes 55412 drop comment "!fw4: drop iot IPv4/IPv6 traffic"
}
chain drop_to_iot {
oifname "eth1.10" counter packets 0 bytes 0 drop comment "!fw4: drop iot IPv4/IPv6 traffic"
}
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname "eth0" jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic"
}
chain srcnat_wan {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic"
}
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
}
chain raw_output {
type filter hook output priority raw; policy accept;
}
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
}
chain mangle_output {
type route hook output priority mangle; policy accept;
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "eth0" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 ingress MTU fixing"
oifname "eth0" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 egress MTU fixing"
}
}
When I run fw4 restart, I do not get any errors.
I am not sure how to check the status of the firewall via command line but I think I got it. See below.
When I run /etc/init.d/firewall status
active with no instances
I am not sure if I have ipban installed or something similar.
Any assistance would be greatly appreciated.
Let me know if you need me to run any other commands to troubleshoot.
@pavelgl would you be able to take a quick look at this?