Hello!
Recently I woke up with an idea, to split my network into smaller chunks, specifically to detach my cameras/iot devices from my "home" or "management" devices/servers. I could just simply leave it as br-lan, having the devices in different subnets and then make a firewall rule to block any outgoing traffic from cameras to "home" but I guess it's not a "good practice" (even if it works).
So I created two vlans, sacrificed some ports on my router to those vlans, connected everything together, but event though it "should" work, it does not. Every device can see the other devices, even if these vlans are different firewall zones, and has packets rejected on input. How can I avoid that?
Imagine I have a REST API on the server with address 192.168.1.115/24 and the device 192.168.2.100/24 can still reach that server, which I don't want.
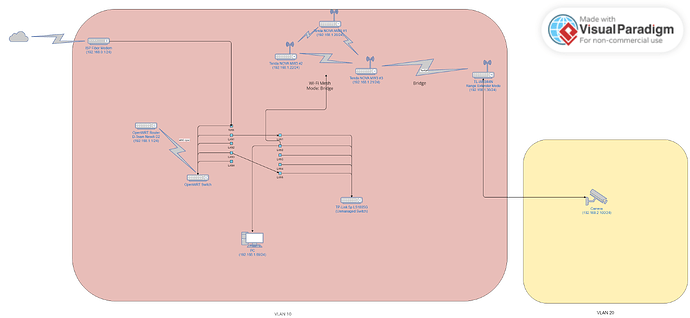
Here is the simplified version of my networking. There is a bunch of other devices not shown in the diagram, but they don't matter.
Maybe the problem is by having unmanaged switch, which still "connects" the devices physically, allowing them to communicate?
ubus call system board
{
"kernel": "5.15.137",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "D-Team Newifi D2",
"board_name": "d-team,newifi-d2",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05-SNAPSHOT",
"revision": "r23633-c7b6cfac40",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05-SNAPSHOT r23633-c7b6cfac40"
}
}
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxxxx::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
option ipv6 '0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
option igmp_snooping '1'
config interface 'lan'
option device 'br-vlans.10'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
list dns '1.1.1.1'
option delegate '0'
config interface 'wan'
option device 'wan'
option proto 'static'
option ipaddr '192.168.0.100'
option netmask '255.255.255.0'
option gateway '192.168.0.1'
list dns '1.1.1.1'
list dns '8.8.8.8'
config interface 'cam'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option device 'br-vlans.20'
config device
option type 'bridge'
option name 'br-vlans'
option igmp_snooping '1'
option ipv6 '0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config bridge-vlan
option device 'br-vlans'
option vlan '10'
list ports 'lan1'
list ports 'lan2'
config bridge-vlan
option device 'br-vlans'
option vlan '20'
list ports 'lan3'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'local'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list rebind_domain 'free.aero2.net.pl'
list server '1.1.1.1'
list server '8.8.8.8'
config dhcp 'lan'
option interface 'lan'
option start '15'
option limit '100'
option leasetime '6h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
option start '100'
option limit '150'
option leasetime '12h'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option mac '00:D8:61:54:CB:35'
option ip '192.168.1.69'
config dhcp 'cam'
option interface 'cam'
option start '40'
option limit '90'
option leasetime '12h'
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src '*'
option proto 'icmp'
option family 'ipv4'
option target 'ACCEPT'
list icmp_type 'echo-request'
option dest '*'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'cam'
option input 'REJECT'
option output 'REJECT'
option forward 'REJECT'
list network 'cam'
config forwarding
option src 'lan'
option dest 'cam'