Hello OpenWRT community,
I am new to OpenWRT world and I need some help, so I hope somebody can help me 
My final goes it to have 2 VLANS on same port, but for starters I am just trying to create 2 VLANS with two subnets.
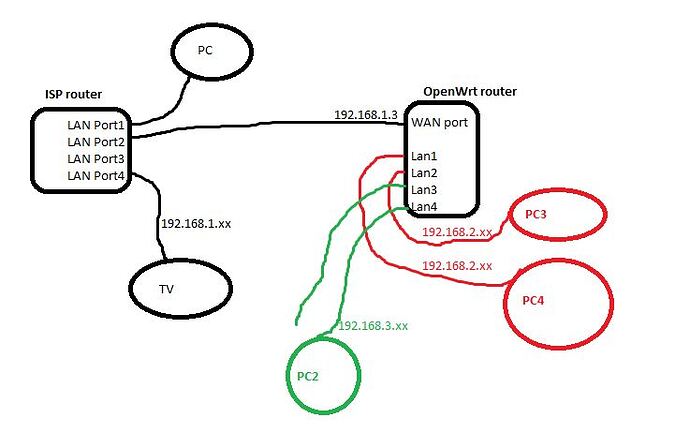
So, this router on which is OpenWRT is connected to primary router(from ISP) which is on 192.168.1.1(LAN cable goes from port 2 ISP router on port 4 OpenWrt router).
The setup I have dones so far:
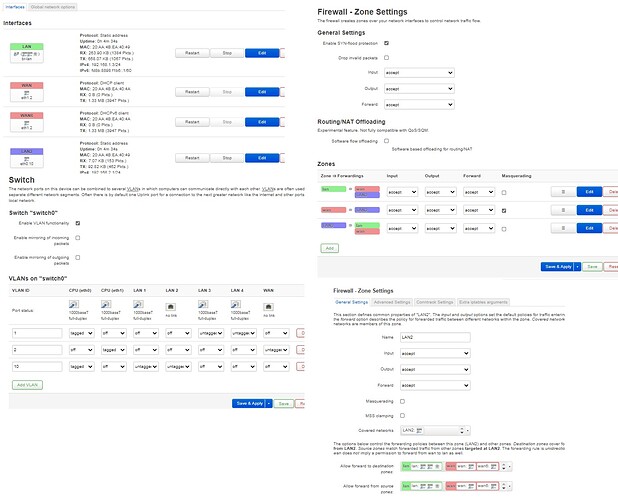
Standard LAN interface is set to 192.168.1.3 and DHCP is disabled(since it is getting it from ISP router) and VLAN 1 is attached to eth0(CPU) and lan3 and lan4 port.
I have also added LAN2(192.168.2.1, DHCP enabled) interface and VLAN 10, which is attched to lan1 and lan2 and eth0(cpu) port.
I have also created firewall zone LAN2 and for covered interfcaes I have set LAN2, and I have also set that it allsows forward to and from other zones.
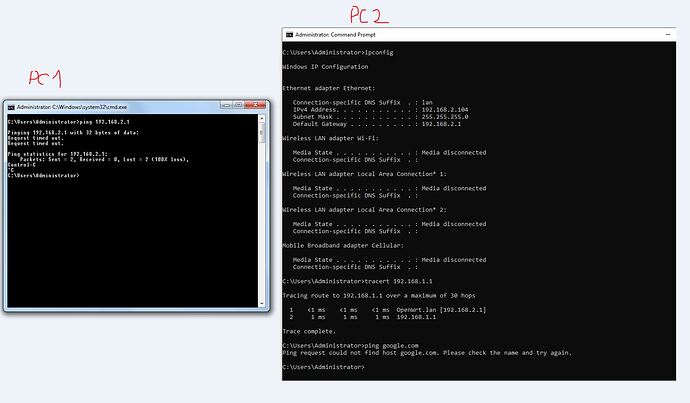
So far, when I connect with my PC to lan1 or lan2 port, I get IP adress, I can enter Luci interface via 192.168.2.1 but that is all. This PC does not want to go to the internet(which is what I want)
I think the problem is in routing tables?
Or mabye it is the ISP router which does not recognize VLANs(do I need additonal interVLAN-ing?)?
Here is a screenshot, and some config files, if you need anything else let me know.
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd8b:8898:f1b6::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.3'
option gateway '192.168.1.1'
option ifname 'eth0.1 eth0.10'
option stp '1'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '5t 2 3'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '6t 4'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '10'
option ports '5t 0 1'
config interface 'LAN2'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option ifname 'eth0.10'
config route
option interface 'LAN2'
option netmask '255.255.255.0'
option gateway '192.168.1.3'
option target '192.168.2.1'
and firewall rules:
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'LAN2'
option network 'LAN2'
option input 'ACCEPT'
option forward 'ACCEPT'
list device 'eth0.1'
list device 'eth0.10'
list device 'eth0'
list device 'eth1'
option output 'ACCEPT'
config forwarding
option dest 'lan'
option src 'LAN2'
config forwarding
option dest 'wan'
option src 'LAN2'
config forwarding
option dest 'LAN2'
option src 'lan'
config forwarding
option dest 'LAN2'
option src 'wan'
root@OpenWrt:~#