To verify, is this site A (office) that we're working with in the latest screenshot?
Yes correct.
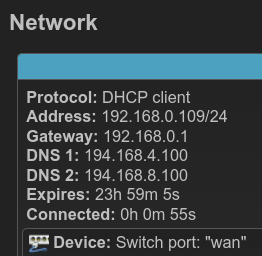
If I change to DCHP client, I'll have the connection back.
What address does it get when it's set to DHCP client?
- address
- subnet
- gateway
- dns
Are you able to set DHCP reservations in the main router at Site A (this way the WG router always gets the same address)?
If not, do you know the DHCP pool range for the main router's DHCP server and the available (unused) IP addresses that are outside that range (you must ensure that the address does not conflict with other static devices and the DHCP pool).
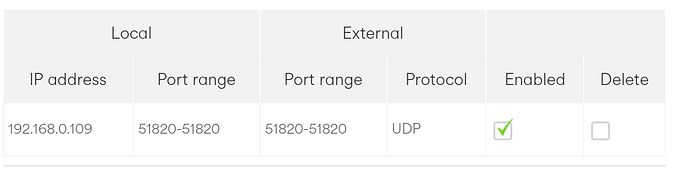
Ok... just leave that as it is for now.
Meanwhile, make sure the port forwarding is set correctly...
The correct address here is 192.168.0.109
Great. Now try to connect again from site b.
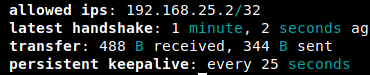
There is a handshake ![]()
Fantastic.
Now, you need to make sure that the main router at Site A has a DHCP reservation so that the WG router never changes addresses.
The other thing to do is to make sure that your apparent IP at Site B (when behind the WG router) is showing up the same as if you were at site B.
Thanks again for your invaluable assistance.
Although the two routers shakehands, Site B (home) does not have the assigned endpoint IP address 80.XX.109.223. But on Site A wireguard page, I can see the external ip from Site B 149.XX.XX.189:32375.
Let’s see the latest network and firewall config files from each side.
Yeap, not a problem.
Site_A - Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda3:3746:ee7f::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'lan1'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan2'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan3'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan4'
option macaddr '90:72:82:83:57:1e'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'dsl0'
option macaddr '90:72:82:83:57:1f'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config interface 'Site_A'
option proto 'wireguard'
option private_key 'WAjXXbWI='
option listen_port '51820'
list addresses '192.168.25.1/24'
config wireguard_Site_A
option description 'SITE_B'
option public_key '0KPWsmY='
list allowed_ips '192.168.25.2/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
Site_A - Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_A'
option forward 'ACCEPT'
config forwarding
option src 'vpn'
option dest 'lan'
config rule
option name 'Allow-Wireguard-Inbound'
list proto 'udp'
option target 'ACCEPT'
option src 'wan'
option dest_port '51820'
Site_B - Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb0:1819:3a56::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'lan1'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan2'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan3'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan4'
option macaddr '64:66:24:de:8d:f8'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.77'
config device
option name 'dsl0'
option macaddr '64:66:24:de:8d:f9'
config interface 'wan'
option proto 'dhcp'
option device 'wan'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config interface 'Site_B'
option proto 'wireguard'
option private_key 'iD7BzH4='
option endpoint_port '192.168.25.2'
config wireguard_Site_B
option description 'SITE_A'
option public_key 'd9IEa/v4etdv1ekI='
option route_allowed_ips '1'
option endpoint_host '80.XX.109.223'
option endpoint_port '51820'
option persistent_keepalive '25'
Site_B - Firewall (Since the router was reset, this file has not been touched)
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
Uncomment this line to disable ipv6 rules
option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
We need to accept udp packets on port 68,
see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
Allow DHCPv6 replies
see https://github.com/openwrt/openwrt/issues/5066
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
EXAMPLE CONFIG SECTIONS
do not allow a specific ip to access wan
#config rule
option src lan
option src_ip 192.168.45.2
option dest wan
option proto tcp
option target REJECT
block a specific mac on wan
#config rule
option dest wan
option src_mac 00:11:22:33:44:66
option target REJECT
block incoming ICMP traffic on a zone
#config rule
option src lan
option proto ICMP
option target DROP
port redirect port coming in on wan to lan
#config redirect
option src wan
option src_dport 80
option dest lan
option dest_ip 192.168.16.235
option dest_port 80
option proto tcp
port redirect of remapped ssh port (22001) on wan
#config redirect
option src wan
option src_dport 22001
option dest lan
option dest_port 22
option proto tcp
FULL CONFIG SECTIONS
#config rule
option src lan
option src_ip 192.168.45.2
option src_mac 00:11:22:33:44:55
option src_port 80
option dest wan
option dest_ip 194.25.2.129
option dest_port 120
option proto tcp
option target REJECT
#config redirect
option src lan
option src_ip 192.168.45.2
option src_mac 00:11:22:33:44:55
option src_port 1024
option src_dport 80
option dest_ip 194.25.2.129
option dest_port 120
option proto tcp
Add forwarding from the vpn zone > wan zone in site A.
config forwarding
option src 'vpn'
option dest 'wan'
For Site B, add the allowed IPs back (0.0.0.0/0) -- you had removed them at one point:
config wireguard_Site_B
option description 'SITE_A'
option public_key 'd9IEa/v4etdv1ekI='
option route_allowed_ips '1'
option endpoint_host '80.XX.109.223'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '0.0.0.0.0/0'
Also for site B, add a firewall zone for the WG interface, and allow forwarding from lan > vpn.
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_B'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'
That is not how it works. Site A's routing system doesn't actually have Site B's public IP or even need to know what it is-- other than to send encrypted packets to it. Users of the LAN at Site A have all their Internet usage forwarded with private IPs inside the tunnel to Site B, then site B sends it to the Internet using its public IP.
There is the Site_A ip address 80.XX.109.223 on wg show on Site_B, but there is no internet connectivity. I can ping 1.1.1.1, but I am unable to open any other websites or "curl ifconfig.co"
I attempted to remove the list allowed_ips '0.0.0.0.0/0' but it had no effect.
I restored the network and firewall configuration files to default settings, but the issue still exists. I'm still not connected. I have no idea where is the problem....
Let’s see the latest network and firewall config files, as well as the output from wg show for both routers.
Hi, I was attempting to figure out the cause of every network issue these days. I attempted to give the office's Openwrt router (Site_A) a static internal ip or reserve the ip address in the isp modem.
When the openwrt router reboots, the mac address changes and a new ip address is assigned, despite my attempts to reserve the IP address from the isp modem.
I also attempted to add a static IP address to the WAN, but I had to add the DNS address 1.1.1.1 to the DCHP and DNS in order to establish a connection. The issue with this technique is that the router of the ISP does not display the device (or the IP address).
Which approach should I adopt based on your experience? Is it possible to block the WAN mac address in any way? Will wireguard function if I open the 51820 port on the openwrt IP address even though it is not visible on the router?
This is unusual... the MAC shouldn't change. If it is really the case, though, maybe OpenWrt is unable to read the factory data. Try adding this:
config device
option name 'wan'
option macaddr '90:72:82:83:57:1d'
If you set a static IP, that is fine, but you do of course need to include all of the following:
- IP address
- Subnet mask
- Gateway
- DNS
And if you set a static IP, it is true that the ISP router device won't show it in the DHCP lease table since it isn't using DHCP. That doesn't cause any problems, though.
Either way is fine -- DHCP (if you can keep the MAC from changing), or static. Both are equally valid, but if static, make sure that IP is outside the DHCP pool and that it is not used by any other devices.
I don't understand this question... what are you trying to do?
It's not that the IP is not visible to the router, it's simply just not visible in the DHCP lease table. Some routers may show the ARP tables, but most don't.
But yes, as long as the port forwarding points to the IP address that OpenWrt is using on that network, it will work just fine.
Thank you for your response.
By adding the option macaddr '90:72:82:83:57:1d' I was able to fix the issue where the IP address would change at each reboot. I also opened the 51820 udp port on the isp modem.
The other (significant) issue I resolved on the router Site B (home) was the absence of internet.
By adding 1.1.1.1 on the DHCP and DNS page, the internet connection was established.
Now that both routers are connected, but the handshake is not taking place.
Please find the network and firewall configuration files listed below.
Site_A - Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda3:3746:ee7f::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'lan1'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan2'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan3'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan4'
option macaddr '90:72:82:83:57:1e'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'dsl0'
option macaddr '90:72:82:83:57:1f'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option macaddr 'E6:FD:07:EC:7F:A0'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config interface 'Site_A'
option proto 'wireguard'
option private_key 'WAjXXbWI='
option listen_port '51820'
list addresses '192.168.25.1/24'
config wireguard_Site_A
option description 'SITE_B'
option public_key '0KWsmY='
list allowed_ips '192.168.25.2/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
Site_A - Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_A'
option forward 'ACCEPT'
config forwarding
option src 'vpn'
option dest 'wan'
config rule
option name 'Allow-Wireguard-Inbound'
list proto 'udp'
option target 'ACCEPT'
option src 'wan'
option dest_port '51820'
Site_B - Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb0:1819:3a56::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'lan1'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan2'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan3'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan4'
option macaddr '64:66:24:de:8d:f8'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.77'
config device
option name 'dsl0'
option macaddr '64:66:24:de:8d:f9'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config interface 'Site_B'
option proto 'wireguard'
option private_key 'iD7phcuBzH4='
option endpoint_port '192.168.25.2'
list allowed_ips '0.0.0.0.0/0'
config wireguard_Site_B
option description 'SITE_A'
option public_key 'd9Idv1ekI='
option route_allowed_ips '1'
option endpoint_host '80.XX.109.223'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '0.0.0.0.0/0'
Site_B - Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_B'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'