I have two identical openwrt routers, BT Home Hub 5A, one in the office (router A) and one at home (router B).
I need the same office external ip (ex 80.10.20.30, it is dynamic) at home in order to access certain hardware and software.
I looked at several instructions and believe that wireguard is the best option, however most of them also suggest using a DNS service, such as freedns.afraid. After wireguard has been setup, the guides suggest connecting any devices using a QR code. Unfortunately, this is not the answer I'm looking for.
My goal is to connect a few devices to my router B at home, so they can see the office's external IP address (router A).
Thank you
The QR code is a feature that helps input the wireguard peer setup information into another device so you wouldn’t have to manually input it, that’s all.
You’ll want to setup DDNS for your office router so that your dynamic ip in the office has a host name you can easily use as the destination zone for your peer clients at home and vice versa.
It sounds like what you want to achieve is a ‘site-to-site’ connection with wireguard. If it’s just a few devices at home you want, you could also go with a ‘site-to-road warrior’ setup on a per device basis. Depending on your utility will determine your best option. A site-to-site setup will allow all devices at home to connect to the office.
Do you control the whole office network (i.e. you can adjust the firewall settings on the main office router)? Is the 5A in the office actually the main router, or is there another router upstream?
This should be pretty straight forward -- a "road warrior" type config will do the trick. Your home router can setup a tunnel such that all (or, if you desire, specific) traffic is sent through to your office and then appears to be originating from your office from the perspective of the internet. But, the first question about your office setup is key.
I appreciate all of your responses.
I read a site-to-site configuration guide and set up both locations (I can use vnc/pc to work on the office router).
I have the following settings on the office router (Site_A):
config interface 'Site_A'
option proto 'wireguard'
option private_key '1234xyz'
option listen_port '51820'
list addresses '80.XX.119.223/32' <- This is the IP that I need to have on my home router (Site_B)
config wireguard_Site_A
option description 'Site_B' <- Home router
option public_key '4567qwe'
list allowed_ips '80.XX.119.223/24'
list allowed_ips '192.168.1.1/24'
option endpoint_host '80.XX.119.223'
option endpoint_port '51820'
option persistent_keepalive '25'
Please see below the settings for the home router (Site_B):
config interface 'Site_B'
option proto 'wireguard'
option private_key '1234xyz'
option listen_port '51820'
list addresses '80.XX.119.223/32'
config wireguard_Site_B
option description 'SITE_A'
option public_key '4567qwe'
list allowed_ips '80.XX.119.0/24'
list allowed_ips '192.168.1.77/24' <- home router ip address
option endpoint_host '80.XX.119.223'
option endpoint_port '51820'
option persistent_keepalive '25'
Where is the error? Between the routers, there is no handshake.
What will also happen when the external IP 80.XX.119.223 changes?
One more thing.
Both routers are VDSL-connected to the isp modem through the wan port.
Many thanks
This first section is about the Site A (work) configuration
This is incorrect. This needs to be an RFC1918 address. Not only that, the interface address must be larger than a /32 -- typically a /24 is used (although that is not required).
The allowed IPs here should be a /32 RFC1918 address in the range of the interface address (discussed above). The endpoint host and port should not be included here. Delete those.
Now, for the home side (Site B)
On this side, the listen port should be omitted, and the address must match the address in the peer config section from site A.
Finally , here the allowed IPs are wrong...
It depends on what traffic you are trying to send through the tunnel. If you want to route all traffic through the tunnel, it would be 0.0.0.0/0. For now, you could do this, and then refine as needed once you have things working.
We also need to have route_allowed_IPs in order to get traffic to move (unless you want to manually set routes).
Putting it all together:
Your configs should look something like this:
Site A Wireguard Config
config interface 'Site_A'
option proto 'wireguard'
option private_key '1234xyz'
option listen_port '51820'
list addresses '192.168.25.1/24'
config wireguard_Site_A
option description 'Site_B'
option public_key '4567qwe'
list allowed_ips '192.168.25.2/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
Site B Wireguard Config
config interface 'Site_B'
option proto 'wireguard'
option private_key '1234xyz'
list addresses '192.168.25.2/32'
config wireguard_Site_B
option description 'SITE_A'
option public_key '4567qwe'
list allowed_ips '0.0.0.0/0'
option endpoint_host '80.XX.119.223'
option endpoint_port '51820'
option persistent_keepalive '25'
option route_allowed_ips '1'
I really appreciate you helping me.
I changed the configurations as advised, but the isn't any handshake between the routers.
Furthermore, I believe that the firewall port forwards may be uncorrected configured.
Please see the configurations below.
Site_A
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_A'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'wan'
config redirect
option dest 'vpn'
option target 'DNAT'
option name 'wg'
list proto 'udp'
option src 'wan'
option src_dport '51820'
option dest_ip '80.XX.109.223/32'
option dest_port '51820'
Site_B
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option name 'Wireguard'
option src_dport '51820'
option src 'wan'
option dest_ip '192.168.1.1'
list proto 'udp'
option dest 'vpn'
option dest_port '51820'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_B'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'wan'
Thank you again for your precious help.
This is incorrect here. You want a basic rule that looks like this:
config rule
option name 'Allow-Wireguard-Inbound'
list proto 'udp'
option target 'ACCEPT'
option src 'wan'
option dest_port '51820'
You will probably also want to have this fowarding rule on Site A:
config forwarding
option src 'vpn'
option dest 'lan'
On Site B, remove this entirely...
and you can also remove this:
Once you're done, let's see the latest firewall and network files for each of the sites.
Thanks again.
No handshaking. As requested, please find below the Site_A and Site_B network and firewall configs.
(Btw, I lost internet connection on router Site_B)
Site_A
Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda3:3746:ee7f::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'lan1'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan2'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan3'
option macaddr '90:72:82:83:57:1e'
config device
option name 'lan4'
option macaddr '90:72:82:83:57:1e'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'dsl0'
option macaddr '90:72:82:83:57:1f'
config interface 'wan'
option proto 'dhcp'
option device 'wan'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config interface 'Site_A'
option proto 'wireguard'
option private_key 'WAjXXXbWI='
option listen_port '51820'
list addresses '192.168.25.1/24'
config wireguard_Site_A
option description 'SITE_B'
option public_key '0KPbgPsL5+WsmY='
list allowed_ips '192.168.25.2/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_A'
option forward 'ACCEPT'
config forwarding
option src 'vpn'
option dest 'lan'
config rule
option name 'Allow-Wireguard-Inbound'
list proto 'udp'
option target 'ACCEPT'
option src 'wan'
option dest_port '51820'
Site_B
Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb9:0afe:6277::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'lan1'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan2'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan3'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan4'
option macaddr '64:66:24:de:8d:f8'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.77'
config device
option name 'dsl0'
option macaddr '64:66:24:de:8d:f9'
config interface 'wan'
option proto 'dhcp'
option device 'wan'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config interface 'Site_B'
option proto 'wireguard'
option private_key 'iD7phS/cuBzH4='
option listen_port '51820'
list addresses '192.168.25.2/32'
config wireguard_Site_B
option description 'SITE_A'
option public_key 'WAjXXXbWI='
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '80.XX.109.223'
option endpoint_port '51820'
option persistent_keepalive '25'
Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Site_B'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'
Thank you
remove the listen port from site B's wireguard interface config.
But I think the real problem is here:
I think you have a key issue... I know you've redacted your keys (which is good... don't publish the keys ![]() ), but it appears that the private key of site A is the same as the value used in site B's peer config...
), but it appears that the private key of site A is the same as the value used in site B's peer config...
Keys are the most common issue for handshake problems.
Each peer will have a pair of keys.
- The private key belongs in the interface configuration
- The public key is derived from the private key and is used in the other peer's peer configuratoin
What this means is:
(removing all but the general structure to illustrate they keys)
config interface 'Site_A'
option proto 'wireguard'
option private_key 'SiteA_PrivateKey'
...
config wireguard_Site_A
option description 'SITE_A'
option public_key 'SiteB_PublicKey'
config interface 'Site_B'
option proto 'wireguard'
option private_key 'SiteB_PrivateKey'
...
config wireguard_Site_B
option description 'SITE_A'
option public_key 'SiteA_PublicKey'
I made the necessary adjustments, but the router Site B (at home) is still not connected to the internet.
Starting over would that make sense? If necessary, I could rapidly restore both routers.
Once again, I appreciate your assistance.
what is the output of
wg show
I appreciate the help, but despite the configuration file having the following settings, Site B's listen port is not 52180 and its change at every reboot.
interface: Site_A
public key: d9IEa23dv1ekI=
private key: (hidden)
listening port: 51820
peer: 0KPb+0+WsmY=
allowed ips: 192.168.25.2/32
persistent keepalive: every 25 seconds
interface: Site_B
public key: 0KPbgP+WsmY=
private key: (hidden)
listening port: 42331
peer: d9IEeF/v4etdv1ekI=
endpoint: 80.1.109.223:51820
allowed ips: 0.0.0.0/0
transfer: 0 B received, 1.30 KiB sent
persistent keepalive: every 25 seconds
/etc/config/network
config interface 'Site_B'
option proto 'wireguard'
option private_key 'iD7phSuBzH4='
option endpoint_port '51820'
config wireguard_Site_B
option description 'SITE_A'
option public_key 'd9IEa21ekI='
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '80.XX.109.223'
option endpoint_port '51820'
option persistent_keepalive '25'
The listen port of site B doesn't matter because it is not accepting inbound connection requests (Site A listens for a connection from site B, not the other way around).
By the output of wg show we can see that the handshake isn't happening.
Remove the endpoing port from here, and add the address (192.168.25.2) into the site B wireguard interface config.
Once more, many thanks. Still no handshaking.
interface: Site_B
public key: 0KPbl+0+WsmY=
private key: (hidden)
listening port: 54455
peer: d9IEa23Ftv1ekI=
endpoint: 80.XX.109.223:51820
allowed ips: 0.0.0.0/0
transfer: 0 B received, 7.66 KiB sent
persistent keepalive: every 25 seconds
Since Site B (house router) lost internet access, I believe this is the reason for no handshaking.
I've just added the network config below.
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb9:0afe:6277::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config device
option name 'lan1'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan2'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan3'
option macaddr '64:66:24:de:8d:f8'
config device
option name 'lan4'
option macaddr '64:66:24:de:8d:f8'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.77'
config device
option name 'dsl0'
option macaddr '64:66:24:de:8d:f9'
config interface 'wan'
option proto 'dhcp'
option device 'wan'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config interface 'Site_B'
option proto 'wireguard'
option private_key 'iD7phS/uBzH4='
option endpoint_port '192.168.25.2'
config wireguard_Site_B
option description 'SITE_A'
option public_key 'd9tdv1ekI='
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '80.XX.109.223'
option endpoint_port '51820'
option persistent_keepalive '25'
Try stopping the wireguard interface on site B (home).
Then run the following ping tests from the router itself:
ping 192.168.0.1
ping 8.8.8.8
ping google.com
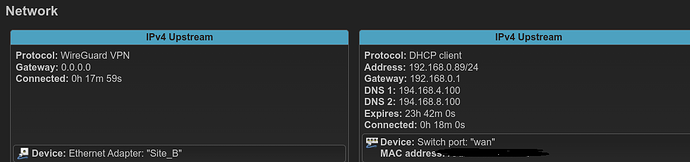
Even after turning off the WireGuard interface, I can only ping the internal IP address (192.168.0.1), not the other ones (external).
Try restarting the wan interface and then try that ping test again.
No luck... I have also rebooted the router, but there is still no connection.
If you connect a computer to the upstream network (192.168.0.0/24), does it access the internet properly?
Nope, no access at all.