Yes the new router will be running openWRT: I want all my routers and network devices at home running openWRT when possible, as it is so flexible and lets me make changes or adapt to future network changes and technologies.
Even ir that supposes a slight drop in performance with respect to the stock firmware (may be sometimes there is that drop in performance, for example with new routers wit ACX or in aspects like beamforming).
For example: with my old tplink, I can now use a WPA3 authentification if I want, just upgrading openWRT. I am sure tplink does not provide that funcionality with the original firmware. It has long abandoned firmware upgrades for that router.
(By the way: Happy christmas to everybody and specially to you and many thanks for your time and answers)
I think I have mastered what you say about a too wide network.
There is no problem when you interconnect two networks with same IP addresses through routing in internet.
I can have 192.168.0.1 in may PC in my private net and connect to a server in another net with same IP, as long as they connect through routers and there is a NAT beetween (there is allways a NAT when you interconnect private networks, or the servers in the other net has a public unique IP address).
The problem arrives when you use a VPN.
If i am in a network outside home (a friend's network) and he has the default config for home routers I will have given a local IP as 192.168.0.2 for example, and when I create the VPN to home and try to connect to my home server with an address like 192.168.0.1, for example (if I have left the default config) there would be a collision, as I cannot create routes for accessing my net through VPN without destroying the routes that provide me local access to my friend's network.
So when interconnecting networks through VPN there are 3 network address involved: the IP addresses in the source network, the IP address in the destination network and the IP addresses used in the tunnel itself.
Any collision in addresses (combination of IP and mask) will create a proble and don't let you do the connection.
So the narrower your network less probability of colliding.
So selecting a non so usual IP network for your home network and for the tunnel itself is a good idea too (192.168.0.XXX or 192.168.1.XXX won't be a good idea as are the defaults in many routers).
Now lets go to the point of selecting an appropiate network for my home and vpn in order to reduce the probability of collision.
But I would like to have a network with more than 254 address in order to be able to organize IPs given to devices by class.
I am thinking of 10 bits for the IP range, that would provide 1023 addresses for the devices, more than needed in a home network. So it would be a /22 "class" network.
That let me have 4 ranges of devices to logically separate the adresses (but in the same network, just as a reminder for me) with 254 devices in each, using the 2 upper bits of the 10bits.
So:
- computers and ordinary leases would be in 0.XXX (0-254) range.
This is the range that will be assigned by the DHCP server with more than enough leases for the number of devices you can get at home.
The other adresses in other ranges will be assigned manually or using DHCP with reserved leases based in MAC.
- Routers, gateways, switches and so in 3.XXX (768-1022 range, 1023 would be all 1's and as so is the broadcast address of the net).
- Servers and docker services and the like in 1.XXX (256-511).
- Printers, scanners or other devices like that in 2.XXX (512-767) (I would like to put here the mobiles and tablets too, but don't know how to configure DHCP to assign ranges based on the type of devices, so they would be in the
Thus I would have enough space in each range to assign new devices to any of the categories. And let me easily remember the type of device looking at its address in decimal format.
Now the time to select a network /22 range.
Being a home network the usual network range would be something beginning by 192.168.XXX.XXX.
There is a whole /16 bit of private IP adresses there, from 192.168.0.0 to 192.168.255.255.
So it is supposed I can select a /22 subrange in that /16 range to assign to my nework.
But most places and IPv4 network calculators list that network range as being /24 class C network.
I don't know if there may be a problem using a /22 bit network there.
In order to reduce collisions with usual assigned IP networks like 192.168.0.xxx or 192.168.1.xxxx I can select something less usual like 192.168.180.0/22.
So:
- standard devices would be 192.168.180.XXX.
- routers, gateways, switches and the like: 192.168.183.XXX
- servers and services: 192.168.181.XXX
- printers, etc: 192.182.XXX
But as said I don't know if there can be problems using 192.168.0.0 as a class wider then the class C /24.
And there would be collision problemes with other nets that are class C, so using a /22 class instead of /16 does not make any difference in the goal of eluding collitions, I think.
If I am in a home that uses the typical 192.168.1.0/24 network (configured in so many routers), I think I will have problems too as the 1 will be interpreted in my network as part of the device adresses and not the network address).
One route will try to stablish a /24 network and other a /22.
Won't there be problems with that?
Selecting 192.168.180.0/22 as my network will have problem for sure with class C networks from 192.168.180-183.0 but that is expected, as that ranges are internally used in my network.
At least ther wont be problems with other networks like 192.168.126.0/24.
May be it is better to do the same but using a 10.0.0.0/8 network narrowing it to a /22 network (instead of trying to widen what usually is treaten like a /24 class C network) and selecting a not so usual and evident network, like 10.211.164/22 and having so:
- routers 10.211.167.xxx
- standard leases: 10.211.164.XXX
- services: 10.211.165.XXX
- printers and the like: 10.211.165.XXX
I think this solution will be better, and less prone to collitions when being connected to other private network and trying to connect home, and with addresses as easy to remember as the usual 192.168.xxx.xxx.
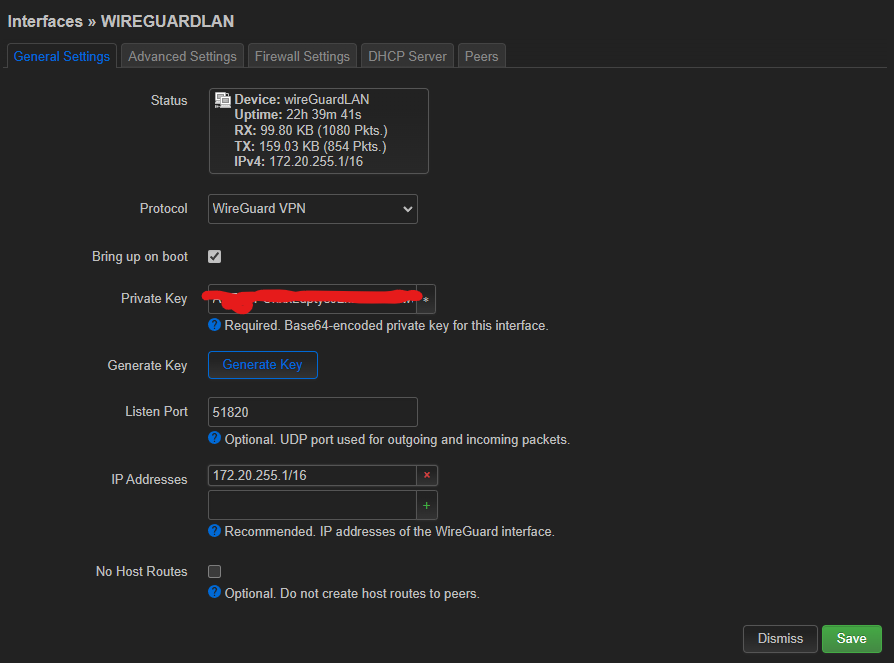
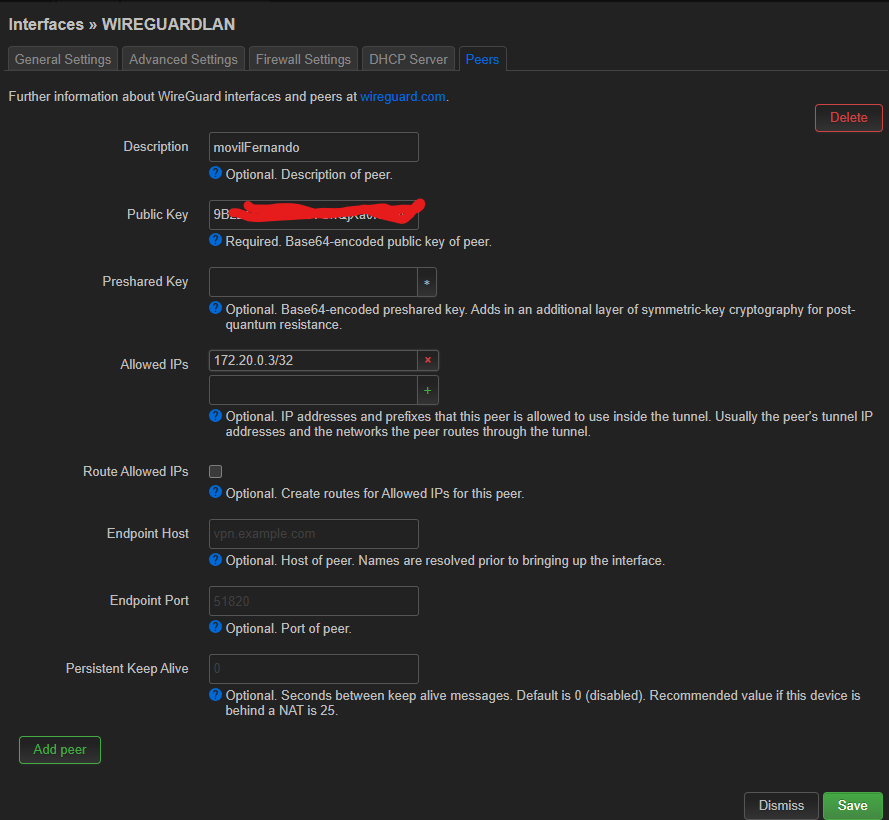
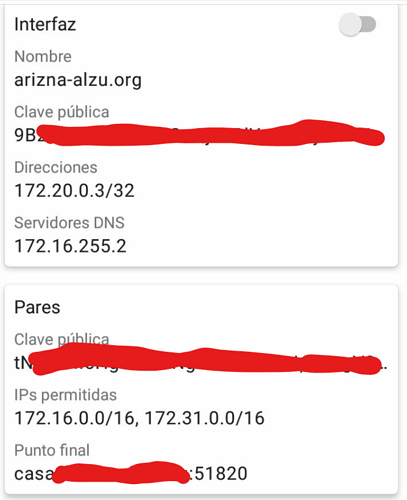
For the VPN network to stablish the wireGuard connection, I think I should use just a 172.16-31.0.0 net treated like a /24 class C like 172.20.20.0/24 with the server in 172.20.20.1 being the server and devices with upgoing address, as there cannot be so many devices connected and the address is only used to stablishg the link.