Hello All,
First a little background on my current situation. I am new to OpenWrt. In our office we currently have two separate ISPs. One fiber and one adsl. We purchased a Linksys WRT3200AC in hopes of installing OpenWRT so we could use the multiwan3 package.
I installed the latest openwrt package OpenWrt 18.06.2 and proceeded to start the setup
To start the process of moving both connections on the router I started first with the adsl line as to not impede the day to day operations of the office. I managed to place the router provided by the first isp to bridge mode.
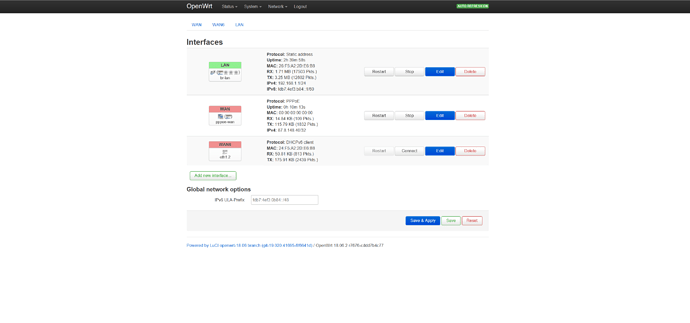
Going back to the router I set up the wan connection on the router as PPPoE protocol with the user and password and after restarting both routers, I got a connection with a public ip address. Everything was going well from here, I managed to setup the firewall and the dhcp server, and proceeded to start adding all the devices to the network. At this point the first connection was done and it was working fine, everything was talking to everything.
Now came time to add the second wan to the equation. I used vlans to make another wan port and hooked that up to the other isp router. Being a piece of shit Vodafone router it dose not allow to do a classic pppoe connection but it forces you to use host-uniq command. Not knowing how to set that up, I googled a bunch and came across some old form from 2017 saying I needed to add another package to offer the support for host-uniq. So I added the packages, restarted the router...….. and nothing. The initial network (one I made first stopped getting internet). I tried to troubleshoot, deleted the packages (nothing happened), I went over all I made trying to figure out why I lost internet on my lan network.
Finally I went crazy and decided to start from scratch... so I reset everything all the routers. On the openwrt router I ran the command firstboot. I then started retracing my steps to get back to where I was before. Come to that point, when setting up the PPPoE for the first network again, the connection was being established, even getting a public ip address. But as soon as i wanted to ping anything... it said that the request timed out. Playing around with the settings lead me nowhere.
I then decided to flash the system with a sysupgrade bin which lead me back to where I started.
Now I am stuck.
Please can someone help me troubleshoot this, ive now wasted 4 full days trying to get this to work. Why cant I go back to the situation where the internet was connecting ?
here is the config flies please let me know if you need anything else.
Also thank you in advance for any help offered. I know ur awesome peeps
root@OpenWrt:~# vi /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'config globals 'globals'
option ula_prefix 'fdb7:4ef3:0b84::/48'config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'config interface 'wan'
option ifname 'eth1.2'
option proto 'pppoe'
option username 'aliceadsl'
option password 'aliceadsl'
option service 'Alice'
option ipv6 'auto'config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
option auto '0'config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5t'config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
root@OpenWrt:~# vi /etc/config/firewall
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECTconfig zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPTconfig zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1config forwarding
option src lan
option dest wanconfig rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPTconfig rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPTconfig rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPTconfig rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPTconfig rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option sequential_ip '1'config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'config dhcp 'wan'
option interface 'wan'
option ignore '1'config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'