I've created a DMZ for one of my servers essentially creating an interface, a firewall zone and assigning a VLAN in the DSA. Currently the firewall's zone input is set to ACCEPT, however, I would like to lockdown the firewall further by setting the input to REJECT and using traffic rules to allow specific traffic through such as DNS, DHCP, ICMP etc.
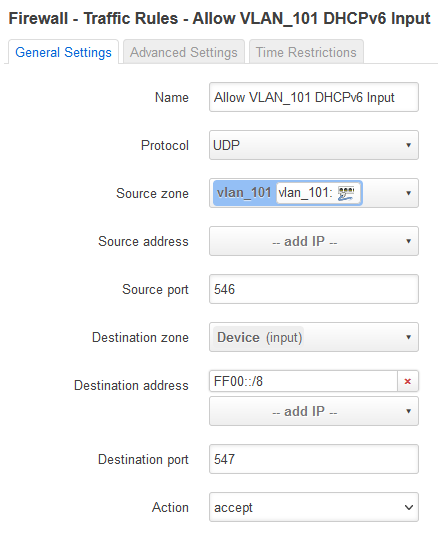
DNS. DHCP and ICMP seem to work but I'm unable to request an IPv6 address from the server as it seems the DHCPv6 traffic rule doesn't seem to be working. The rule I have created to allow DHCPv6 is called Allow VLAN_101 DHCPv6 Input which is shown in the configuration below.
**/
/etc/config/firewall
...
config zone 'vlan_101'
option name 'vlan_101'
list network 'vlan_101'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
config forwarding
option src 'vlan_101'
option dest 'wan'
config rule
option target 'ACCEPT'
option dest_port '53'
option name 'Allow VLAN_101 DNS Input'
option src 'vlan_101'
list proto 'udp'
config rule
option target 'ACCEPT'
option dest_port '67-68'
option name 'Allow VLAN_101 DHCP Input'
option src 'vlan_101'
option proto 'udp'
option family 'ipv4'
config rule
option target 'ACCEPT'
option name 'Allow VLAN_101 DHCPv6 Input'
option family 'ipv6'
list proto 'udp'
option src 'vlan_101'
option dest_port '546-547'
config rule
list proto 'icmp'
option target 'ACCEPT'
option dest 'vlan_101'
option name 'Allow VLAN_101 Ping from Private'
option src 'private'
config rule
option name 'Allow Private SSH to vlan_101'
list proto 'tcp'
option src 'private'
option dest 'vlan_101'
option dest_port '22'
option target 'ACCEPT'
...
Where am I going wrong?