ok, post output from terminal. and show me where you connected GND, resistance should be 0 i guess not infinite
I used the single GND pin marked in the picture in your original post, the one not inside the 14pin JTAG, but in the 4pin serial. However, that pin has inf resistance to JTAG grounds.
I will try to flash uboot now and report back later!
Just a short update (im in vacation now, didnt had time yet to test much): Uboot flashed succesfully and i have indeed a working bootloader, however, my devices MAC, ID (i got that fixed by hexediting the firmware) and some other things are pretty messed up. Also i cant flash openwrt, itll bootload instantly (edit: i wanted to say its bootlooping instantly, my bad).
Am i correct assuming that the MAC address and other stuff was written into the uboot-env?
MAC,ID, WPS pin are present at the end of u-boot partition only as far as i know, thus offsets 1FC, 1FD, 1FE and are needed to be entered manually unless you flash backed-up u-boot bin.
about instant bootload, check your uart cable and interface (you said it had some GND problems), but hitting tpl within one second should interrupt boot process. otherwise it could be hw fault such as disconnected rx line
The ground pins should have (practically) zero ohms to grounded parts of the board like the shield boxes and antenna outer conductors.
I misspelled, wanted to say that it bootloops instantly after attempting to flash it. My bad! Ill start trouble shooting in a week once im back home, just wanted to give an update that the procedure of recovering uboot via jtag is working on v2 as well and maybe hear an opinion with how to procede with my uboot env. Is there anything else important in the uboot env (and if yes, should i copy a different archer c7v2 uboot env first and then change MAC/WPS? Does the MAC even matter as long as i have one?) is there a checksum/hash to protect the MAC/uboot-env?
How the hell do i even have a MAC, is there a fallback value coded into the uboot.bin i extracted from their stock firmware? Or is it just some random junk data that was there from whatever also messed up my bootloader in the first place?
The GND problem was a bad solder joint. I dont know how i messed that up, i even used extra flux, however, the solder did not connect to pin even though looking good from the outside. Was confused because i expected even a bad solder joint to give some kind of connection.
MAC should not be relevant to this problem. at least i could flash u-boot without any MAC and ID and it still flashed and booted firmware as usual, only showing random mac addresses on each boot.
did it print any messages on the console when you attempted to flash fw?
It did, the usual stuff when tftp recovering, pulling file, installing, rebooting. From there it bootloops. As mentioned, i didnt had any time to troubleshoot myself, if youre saying that it should work and has nothing to do with my messed up uboot-env then thats what im going to do first before asking for more help. If i cant figure it out ill come back in roughly a week with detailed UART logs.
I really appreciate both your indepth tutorial and your replies, thanks a lot!
When you direct flash OpenWrt using bootloader TFTP and write commands, use the sysupgrade image not the factory.
Factory has an extra header that should not be commited to flash. It will cause a "Bad Magic Number" error. The sysupgrade starts directly with the kernel header that the bootloader expects when booting.
good catch. i also forget about that sometimes
Cant exactly reproduce what i did wrong in the first place, but now got OpenWRT running fine after flashing Bootloader again, then installing stock firmware and installing openwrt from webinterface. Thanks for your help.
u-boot still running until showing "Autobooting in"
then it's hang , no kernel loaded and no command i can type on serial console
Can i use this method for rewrite u-boot?
yes, but are you sure kernel is flashed properly? best to run md5sum on file you flashed and then dump back content you flashed. it should match the md5sum
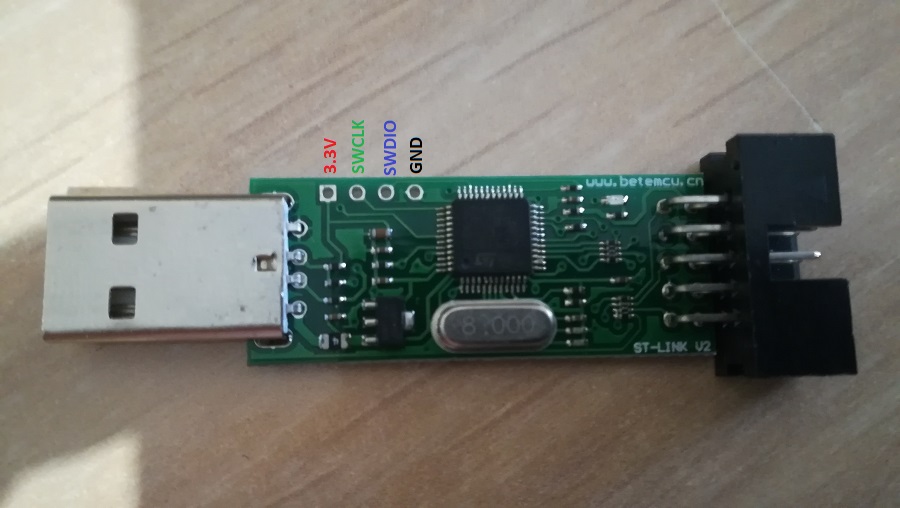
Hi everyone
I also have a st-link v2 and i would like to load this firmware
the card has perforated pitches at the bottom as you can see from the photo can I make the connections in those pitches or are they different?
Do you think I was able to identify the right pinouts from the photo?
I can use the same openwrt to upload the firmware with a usb to uart CP210x card, what packages should I install on openwrt?
these are different. you need to solder wires to the bottom part of the board. see details here: https://wiki.cuvoodoo.info/doku.php?id=jtag
Hi psyborg I flashed and it seems to be fine, I replaced /dev/ttyUSB0 with COM3 with windows 10
I would like to restore a brick router, an aztech hw550-3g
I found this cfg file
set _CHIPNAME rt3052
set _ENDIAN little
set _CPUTAPID 0x1305224F
#daemon configuration
telnet_port 4444
gdb_port 3333
#interface
#interface ft2232
#ft2232_device_desc "Olimex OpenOCD JTAG ARM-USB-TINY-H"
#ft2232_layout olimex-jtag
#ft2232_vid_pid 0x15ba 0x002a
if { [info exists PARPORTADDR] } {
set _PARPORTADDR $PARPORTADDR
} else {
set _PARPORTADDR 0
}
interface parport
parport_port $_PARPORTADDR
parport_cable dlc5
#jtag_speed
adapter_khz 500
adapter_nsrst_delay 100
jtag_ntrst_delay 100
echo on
# jtag scan chain
# format L IRC IRCM IDCODE (Length, IR Capture, IR Capture Mask, IDCODE)
jtag newtap $_CHIPNAME cpu -irlen 5 -ircapture 0x1 -irmask 0x3 -expected-id $_CPUTAPID
set _TARGETNAME [format "%s.cpu" $_CHIPNAME]
target create $_TARGETNAME mips_m4k -endian $_ENDIAN -chain-position $_TARGETNAME
# flash size will be probed
set _FLASHNAME $_CHIPNAME.flash
# format flash bank name driver base size chip_width bus_width target
flash bank $_FLASHNAME cfi 0xBF000000 8388608 2 2 $_TARGETNAME
#flash bank $_FLASHNAME cfi 0x0 8388608 2 2 $_TARGETNAME
echo "allocating work area"
$_TARGETNAME configure -work-area-phys 0x80040000 -work-area-size 4096
echo "allocation complete"
#Folloing code may not work, in that case you need to manually reset init
#and manually load your u-boot.bin at starting address (0x0) of flash (not RAM).
#starting Address of flash can be found in old dump of serial console or at ddwrt forum/openwrt forum
$_TARGETNAME configure -event reset-init {
#reset
echo "halting the target!!!!!!!!!!!!!!!!!!!!!!!!!!!"
halt
echo "init SDRAM controller..........................@@@@@@@@@@@@@@@@@@@@"
mww 0x10000300 0xd1825272
mww 0x10000304 0xe0120300
echo "Find flash..."
flash probe 0
echo "Load u-boot .."
load_image uboot_aztc.bin 0x80000000 bin
# resume 0x80000000
}
how do I replace DLC5 cable with vsllink in settings?
Please open a new topic for your questions regarding HW550-3G.
Thanks!
Hello,
I have a bricked TP-Link Archer C7 v2. I have wired as shown in the picture and flashed the ST-Link v2 USB adapter with Versaloon. Created a ath79.cfg file with the additions found in this topic. When I start the router with pin shorted to ground I successfully connect to the router. Get error message: Info : JTAG tap: ath79.cpu tap/device found: 0x00000001 (mfg: 0x000 (<invalid>), part: 0x0000, ver: 0x0) . I can connect by using telnet 127.0.0.1 4444. On submitting reset I get message:
JTAG tap: ath79.cpu tap/device found: 0x00000001 (mfg: 0x000 (<invalid>), part: 0x0000, ver: 0x0). Submitting "halt" I get: Failed to enter Debug Mode!
isa info not available, failed to read cp0 config register: 0
target halted in MIPS32 mode due to debug-request, pc: 0x00000000 .
Does anyone have an idea what I am doing wrong? Thanks for your reply in advance.
I am in need of some help,......
TP-LINK Archer C7 V2 with J-Link V9.4 JTAG PROBE
C:\openocd-0.11.0-rc2>openocd -f ./scripts/interface/jlink.cfg -f ./scripts/target/ath79.cfg
Open On-Chip Debugger 0.11.0-rc2
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
adapter speed: 6000 kHz
Info : auto-selecting first available session transport "jtag". To override use 'transport select <transport>'.
Info : Listening on port 6666 for tcl connections
Info : Listening on port 4444 for telnet connections
Info : J-Link V9 compiled Jun 2 2222 22:22:22
Info : Hardware version: 9.40
Info : VTarget = 2.528 V
Info : clock speed 6000 kHz
Info : JTAG tap: ath79.cpu tap/device found: 0x00000001 (mfg: 0x000 (<invalid>), part: 0x0000, ver: 0x0)
MIPS32 with MIPS16 support implemented
Info : starting gdb server for ath79.cpu on 3333
Info : Listening on port 3333 for gdb connections
Info : accepting 'telnet' connection on tcp/4444
Info : JTAG tap: ath79.cpu tap/device found: 0x00000001 (mfg: 0x000 (<invalid>), part: 0x0000, ver: 0x0)
target halted in MIPS32 mode due to undefined, pc: 0xbfc008e8
Info : JTAG tap: ath79.cpu tap/device found: 0x00000001 (mfg: 0x000 (<invalid>), part: 0x0000, ver: 0x0)
target halted in MIPS32 mode due to debug-request, pc: 0xbfc008e8
Info : Found flash device 'gd gd25q128c' (ID 0x001840c8)
Info : writing 256 bytes to flash page @0x00000000
Info : writing 256 bytes to flash page @0x00000100
etc.
I am trying to Restore UBOOT and ART to an empty flash for
BARE BONE recovery with TFTP with Original TP-LINK Firmware......
UBOOT is restored in the correct addresses. (See below LOG).
ART is NOT restored in the correct addresses (See below LOG).
Somehow the addressing is going wrong !!!!
What is the issue here ?
Open On-Chip Debugger
> halt
> reset
JTAG tap: ath79.cpu tap/device found: 0x00000001 (mfg: 0x000 (<invalid>), part: 0x0000, ver: 0x0)
target halted in MIPS32 mode due to undefined, pc: 0xbfc008e8
> reset init
JTAG tap: ath79.cpu tap/device found: 0x00000001 (mfg: 0x000 (<invalid>), part: 0x0000, ver: 0x0)
target halted in MIPS32 mode due to debug-request, pc: 0xbfc008e8
> flash info 0
Found flash device 'gd gd25q128c' (ID 0x001840c8)
#0 : ath79 at 0xbf000000, size 0x01000000, buswidth 0, chipwidth 0
# 0: 0x00000000 (0x10000 64kB) protected
# 1: 0x00010000 (0x10000 64kB) protected
2 to 252 >> OK
#253: 0x00fd0000 (0x10000 64kB) protected
#254: 0x00fe0000 (0x10000 64kB) protected
#255: 0x00ff0000 (0x10000 64kB) protected
ATH79 flash information:
Device 'gd gd25q128c' (ID 0x001840c8)
> flash protect 0 0 255 off
cleared protection for sectors 0 through 255 on flash bank 0
> flash info 0
#0 : ath79 at 0xbf000000, size 0x01000000, buswidth 0, chipwidth 0
# 0: 0x00000000 (0x10000 64kB) not protected
# 1: 0x00010000 (0x10000 64kB) not protected
2 to 252 >> OK
#253: 0x00fd0000 (0x10000 64kB) not protected
#254: 0x00fe0000 (0x10000 64kB) not protected
#255: 0x00ff0000 (0x10000 64kB) not protected
ATH79 flash information:
Device 'gd gd25q128c' (ID 0x001840c8)
> flash erase_sector 0 0 255
erased sectors 0 through 255 on flash bank 0 in 126.738251s
> flash write_image uboot.bin 0xbf000000
writing 256 bytes to flash page @0x00000000
writing 256 bytes to flash page @0x00000100
200 to 1fd00 >> OK
writing 256 bytes to flash page @0x0001fd00
writing 256 bytes to flash page @0x0001fe00
wrote 131072 bytes from file uboot.bin in 2426.323486s (0.053 KiB/s)
>>>>>>>HERE IT STARTS GOING WRONG<<<<<<<<
>>>>>>> ADDRESSING NOT CORRECT <<<<<<<<
> flash write_image art.bin 0xbfff0000
writing 256 bytes to flash page @0x00ff1000
writing 256 bytes to flash page @0x00ff1100
writing 256 bytes to flash page @0x00ff1200
writing 256 bytes to flash page @0x00ff1300
writing 256 bytes to flash page @0x00ff1400
writing 256 bytes to flash page @0x00ff5000
writing 256 bytes to flash page @0x00ff5100
writing 256 bytes to flash page @0x00ff5200
writing 256 bytes to flash page @0x00ff5300
writing 256 bytes to flash page @0x00ff5400
writing 256 bytes to flash page @0x00ff5500
writing 256 bytes to flash page @0x00ff5600
writing 256 bytes to flash page @0x00ff5700
writing 256 bytes to flash page @0x00ff5800
wrote 65536 bytes from file art.bin in 72.637207s (0.881 KiB/s)
>
16777216(DEC)=1000000(HEX) OR FFFFFF(HEX)
16777216(DEC)-65536(DEC)=FF0000(HEX)
Must be:
flash write_image art.bin 0xb0ff0000