So I have been working w/ TorGuard support past day or so just confirming their config generator and as of right now I am successfully getting a 3-way handshake connection working on my new VPN interface.
Goal is to route all devices LAN > WAN > LAN via VPN.
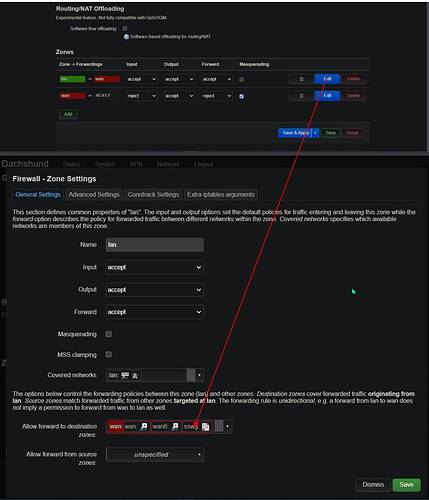
Right now I am looking for more direction on, how to apply VPN to LAN Traffic exiting and returning back from WAN.
I am presuming I need to set up some sort of default gateway/IP rules now?
(Attached is current router config, redacting all public IP addresses, however should be sufficient)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt SNAPSHOT, r19327-5959c46456
-----------------------------------------------------
~# uci export network; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; wg
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxxxxxxxxxxxxxxx'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.0.50.1'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option peerdns '0'
list dns '8.8.8.8'
config interface 'wg0'
option proto 'wireguard'
option private_key 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx'
option listen_port '51820'
list addresses 'xxxxxxxxxxxxxx'
option force_link '1'
option mtu '1292'
option peerdns '0'
list dns '8.8.8.8'
config wireguard_wg0
option description 'Butters'
option public_key 'P/ww/R0OlFyh1NQudHXDy3nLzrt6tNFjPkusZy9MCDo='
list allowed_ips '0.0.0.0/0'
option endpoint_host 'xxxxxxxxxxxxxxx'
option endpoint_port '1443'
option persistent_keepalive '25'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'WgVPN'
option output 'ACCEPT'
list network 'wg0'
option masq '1'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'WgVPN'
head: /etc/firewall.user: No such file or directory
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
7: wan@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet xxxxxxxxxxxxxxxx brd xxxxxxxxxxxxxxx scope global wan
valid_lft forever preferred_lft forever
10: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 10.0.50.1/24 brd 10.0.50.255 scope global br-lan
valid_lft forever preferred_lft forever
12: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1292 qdisc noqueue state UNKNOWN qlen 1000
inet xxxxxxxxxxxxxxx brd xxxxxxxxxxxxxxx scope global wg0
valid_lft forever preferred_lft forever
default via xxxxxxxxxxxxx dev wan src xxxxxxxxxxxxxxxxxxx
10.0.50.0/24 dev br-lan scope link src 10.0.50.1
xxxxxxxxxxxxxx dev wg0 scope link src xxxxxxxxxxxx
xxxxxxxxxxxxxxxxx via xxxxxxxxxxxxxxxxxx dev wan
xxxxxxxxxxxxxxxxxx dev wan scope link src xxxxxxxxxxxxxxxxxx
broadcast 10.0.50.0 dev br-lan table local scope link src 10.0.50.1
local 10.0.50.1 dev br-lan table local scope host src 10.0.50.1
broadcast 10.0.50.255 dev br-lan table local scope link src 10.0.50.1
broadcast xxxxxxxxxxxxxx dev wg0 table local scope link src xxxxxxxxxxxxxxx
local xxxxxxxxxxxxxxxx dev wg0 table local scope host src xxxxxxxxxxxxx
broadcast xxxxxxxxxxxxxxxxxxx dev wg0 table local scope link src xxxxxxxxxxxxxxx
broadcast xxxxxxxxxxxxxxxxxxx dev wan table local scope link src xxxxxxxxxxxxxxxxxxxx
local xxxxxxxxxxxxxxxxx dev wan table local scope host src xxxxxxxxxxxxxxxxxxxxxxxxx
broadcast xxxxxxxxxxxxxxxxxxxx dev wan table local scope link src xxxxxxxxxxxxxxxxxxxxx
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
interface: wg0
public key: 4smHOrLLU10f6DAvoU5KzKtn0isAIABj1YFx+j8HQS4=
private key: (hidden)
listening port: 51820
peer: P/ww/R0OlFyh1NQudHXDy3nLzrt6tNFjPkusZy9MCDo=
endpoint: xxxxxxxxxxxxxxxx:1443
allowed ips: 0.0.0.0/0
latest handshake: 1 minute, 34 seconds ago
transfer: 92 B received, 276 B sent
persistent keepalive: every 25 seconds