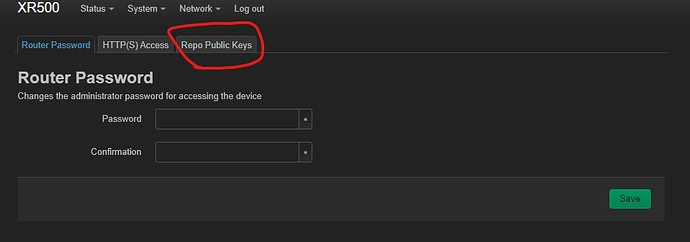
Hi everyone,
After today's update on 21-06-2025, this menu appeared in the administration section.
Is this normal, or has someone else's organization app been installed on my router?
I would be thankful if you could help me and explain what it is.
What update?
ubus call system board
i use software update section to update packages.
That is not good.
Upgrading packages (via the CLI opkg upgrade command or the LuCI Upgrade... button) can result in major problems. It is generally highly discouraged, unless you know what you are doing or if there is specific instruction to do so.
Is it part of the system? i mean Repo public Keys section?
Can you provide this, please:
i am sorry how can do this?
Login via ssh to your router and run that command.
You are probably on snapshot, I assume.
i removed dropbear for security. give 2 min i fix it. back soon
That is not a good thing to do. It doesn’t improve security by any significant amount. The web server (for LuCI) is actually the thing that would be more beneficial to remove if you want to improve security, but that is not relevant if you trust your local network.
Given that you may have some misunderstandings about the best practices for configuring and using openwrt, let’s review your config to make sure nothing is wrong.
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
here is it:
root@XR500:~# ubus call system board
{
"kernel": "6.6.86",
"hostname": "XR500",
"system": "ARMv7 Processor rev 0 (v7l)",
"model": "Netgear Nighthawk XR500",
"board_name": "netgear,xr500",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "24.10.1",
"revision": "r28597-0425664679",
"target": "ipq806x/generic",
"description": "OpenWrt 24.10.1 r28597-0425664679",
"builddate": "1744562312"
oh boy to much info to let you know:
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
list dns '1.1.1.1'
option delegate '0'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option hostname '*'
option peerdns '0'
list dns '1.1.1.1'
option delegate '0'
config device
option name 'phy1-ap0'
option ipv6 '0'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'eth1'
option ipv6 '0'
config device
option name 'lan1'
option ipv6 '0'
config device
option name 'lan3'
option ipv6 '0'
config device
option name 'lan2'
option ipv6 '0'
config device
option name 'lan4'
option ipv6 '0'
config device
option name 'wan'
option ipv6 '0'
root@XR500:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'soc/1b700000.pci/pci0001:00/0001:00:00.0/0001:01:00.0'
option band '2g'
option channel '1'
option disabled '1'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'sae-mixed'
option key 'xxxxxxxxxxxxxxxxx'
option ocv '0'
option wpa_disable_eapol_key_retries '1'
config wifi-device 'radio1'
option type 'mac80211'
option path 'soc/1b500000.pci/pci0000:00/0000:00:00.0/0000:01:00.0'
option band '5g'
option channel '36'
option htmode 'VHT80'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'xxxxxxxxxxxx'
option encryption 'sae-mixed'
option key 'xxxxxxxxxxx'
option ocv '0'
option wpa_disable_eapol_key_retries '1'
option macfilter 'allow'
list maclist 'xxxxxxxxxxx'
list maclist 'xxxxxxxxxxx'
list maclist 'xxxxxxxxxxx'
list maclist 'xxxxxxxxxxx'
root@XR500:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option dhcpleasemax '5'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'xxxxxxxxxxxxxxx'
option ip '192.168.1.100'
list mac 'xxxxxxxxxx'
config host
option name 'xxxxxxx'
option ip '192.168.1.114'
list mac 'xxxxxxxxxx'
config host
option name 'xxxxxxxxxx'
option ip '192.168.1.170'
list mac 'xxxxxxxxxxxxx'
config host
option name 'xxxxxxxx'
option ip '192.168.1.209'
list mac 'xxxxxxxxxxxxxx'
config host
option name 'xxxxxxxxx'
option ip '192.168.1.157'
list mac 'xxxxxxxxxxxx'
root@XR500:~# cat /etc/config/firewall
config defaults
option input 'DROP'
option output 'ACCEPT'
option forward 'DROP'
option synflood_protect '1'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'DROP'
list network 'lan'
config zone
option name 'wan'
option input 'DROP'
option output 'ACCEPT'
option forward 'DROP'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
There are certainly a lot of unnecessary changes relative to the defaults and several things that are suboptimal.
Why have you made so many changes to the firewall?
i like my firewall settings it is working fine i dont have any issues with it.
I’m asking why you made the changes, though.
security measures
I don’t think you have made your device more secure. The defaults are secure by design and each of the rules is there for a good reason.
Did you understand all of those rules and config items in full detail before you changed them?
yes, alot allow icmp rules i do not want it.