Thank you
I had to put the commands into a shell script so I could write the output to a file, but it generated some error I believe may be ignored.
root@openwrt:~# ./route.sh >> route.txt
head: /etc/firewall.user: No such file or directory
./route.sh: line 6: ip6tables-save: command not found
head: /tmp/resolv.conf.d: I/O error
root@openwrt:~#
This is the content of route.txt
{
"kernel": "5.10.134",
"hostname": "openwrt",
"system": "Intel(R) Core(TM) i7 CPU M 620 @ 2.67GHz",
"model": "Dell Inc. Latitude laptop",
"board_name": "dell-inc-latitude-laptop",
"rootfs_type": "ext4",
"release": {
"distribution": "OpenWrt",
"version": "22.03.0-rc6",
"revision": "r19590-042d558536",
"target": "x86/64",
"description": "OpenWrt 22.03.0-rc6 r19590-042d558536"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb5:xx:xx::/48'
config interface 'WAN'
option proto 'dhcp'
option device 'eth0'
option hostname '*'
config interface 'LAN'
option proto 'static'
option device 'eth1'
option ipaddr '10.x.x.1'
option netmask '255.x.x.192'
list dns '1.1.1.1'
config interface 'wireguard'
option proto 'wireguard'
option private_key 'privateKey'
option auto '0'
option listen_port '51820'
list addresses '10.x.x.7/32'
option force_link '1'
config wireguard_wireguard
option description 'bubble'
option public_key 'publicKey'
option preshared_key 'presharedKey'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host 'dynamicDNS.org'
option persistent_keepalive '25'
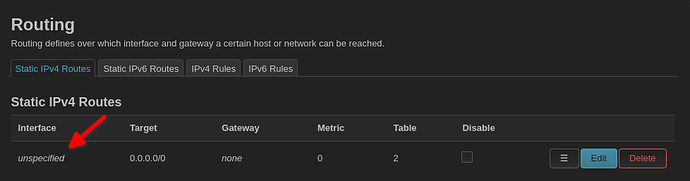
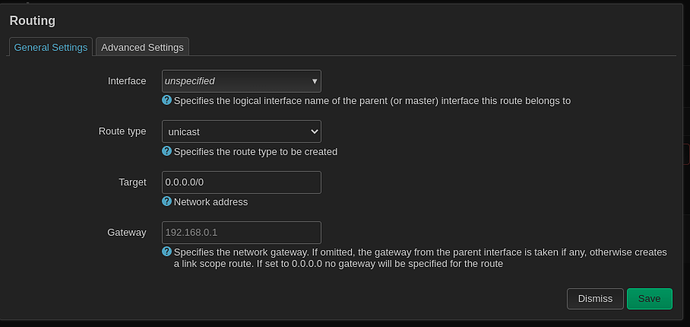
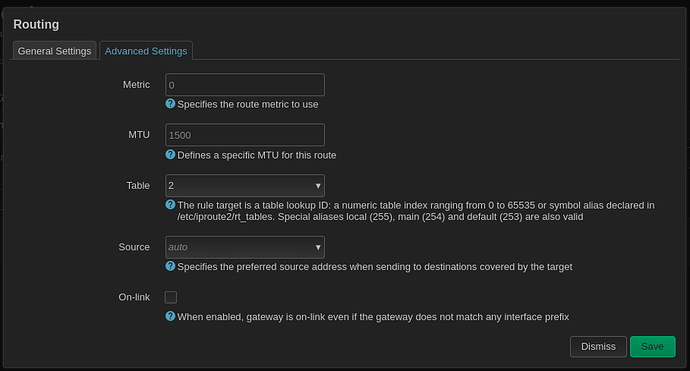
config route
option table '2'
option gateway '216.x.x.1'
option target '0.0.0.0/0'
option interface 'WAN'
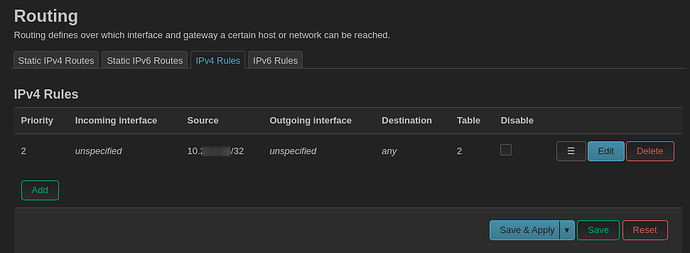
config rule
option src '10.x.x.27/32'
option lookup '2'
option priority '2'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
option confdir '/tmp/dnsmasq.d'
option noresolv '1'
option doh_backup_noresolv '-1'
list doh_backup_server ''
list server '/use-application-dns.net/'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
option sequential_ip '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'LAN'
option interface 'LAN'
option start '100'
option limit '150'
option leasetime '12h'
config host
option name 'accessPoint-1'
option dns '1'
option mac 'B0:xx:xx:xx:xx:CC'
option ip '10.x.x.2'
config host
option name 'accessPoint-2'
option dns '1'
option mac 'B2:xx:xx:xx:xx:75'
option ip '10.x.x.3'
config host
option name 'iphone-1'
option dns '1'
option mac '90:xx:xx:xx:xx:60'
option ip '10.x.x.15'
config host
option name 'laptop-x-os'
option dns '1'
option mac '00:xx:xx:xx:xx:54'
option ip '10.x.x.23'
config host
option name 'e7250-x'
option dns '1'
option mac '5C:xx:xx:xx:xx:7E'
option ip '10.x.x.24'
config host
option name 'desktop'
option dns '1'
option mac 'B2:xx:xx:xx:xx:8F'
option ip '10.x.x.25'
config host
option name 'tablet'
option dns '1'
option mac '7C:xx:xx:xx:xx:32'
option ip '10.x.x.26'
config host
option name 'kodi-x'
option mac '00:xx:xx:xx:xx:40'
option ip '10.x.x.27'
config host
option name 'TV'
option dns '1'
option mac '08:xx:xx:xx:xx:2E'
option ip '10.x.x.28'
config host
option mac '5C:xx:xx:xx:xx:61'
option name 'iphone-2'
option dns '1'
option ip '10.x.x.16'
config host
option name 'E094947.lan'
option dns '1'
option mac 'A8:xx:xx:xx:xx:8C'
option ip '10.x.x.38'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'LAN'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'WAN'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'bcp38'
option type 'script'
option path '/usr/lib/bcp38/run.sh'
option family 'IPv4'
option reload '1'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'katz 01'
list proto 'tcp'
option src 'wan'
option src_dport '4xx2'
option dest_ip '10.x.x.23'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'katz 02'
list proto 'udp'
option src 'wan'
option src_dport '4x7x'
option dest_ip '10.x.x.23'
config zone
option name 'wireguard'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wireguard'
config forwarding
option src 'lan'
option dest 'wireguard'
# Generated by iptables-save v1.8.7 on Sat Nov 19 15:34:09 2022
*raw
:PREROUTING ACCEPT [5188245:5022574081]
:OUTPUT ACCEPT [1414588:374865041]
COMMIT
# Completed on Sat Nov 19 15:34:09 2022
# Generated by iptables-save v1.8.7 on Sat Nov 19 15:34:09 2022
*mangle
:PREROUTING ACCEPT [5188245:5022574081]
:INPUT ACCEPT [2022478:2291218705]
:FORWARD ACCEPT [3165740:2731350342]
:OUTPUT ACCEPT [1414588:374865041]
:POSTROUTING ACCEPT [4580154:3106204247]
:qos_Default - [0:0]
:qos_Default_ct - [0:0]
[0:0] -A qos_Default -j CONNMARK --restore-mark --nfmask 0xf --ctmask 0xf
[0:0] -A qos_Default -m mark --mark 0x0/0xf -j qos_Default_ct
[0:0] -A qos_Default -p udp -m mark --mark 0x0/0xf0 -m length --length 0:500 -j MARK --set-xmark 0x22/0xff
[0:0] -A qos_Default -p icmp -j MARK --set-xmark 0x11/0xff
[0:0] -A qos_Default -p tcp -m mark --mark 0x0/0xf0 -m tcp --sport 1024:65535 --dport 1024:65535 -j MARK --set-xmark 0x44/0xff
[0:0] -A qos_Default -p udp -m mark --mark 0x0/0xf0 -m udp --sport 1024:65535 --dport 1024:65535 -j MARK --set-xmark 0x44/0xff
[0:0] -A qos_Default -j CONNMARK --save-mark --nfmask 0xff --ctmask 0xff
[0:0] -A qos_Default_ct -p tcp -m mark --mark 0x0/0xf -m tcp -m multiport --ports 22,53 -m comment --comment "ssh, dns" -j MARK --set-xmark 0x11/0xff
[0:0] -A qos_Default_ct -p udp -m mark --mark 0x0/0xf -m udp -m multiport --ports 22,53 -m comment --comment "ssh, dns" -j MARK --set-xmark 0x11/0xff
[0:0] -A qos_Default_ct -p tcp -m mark --mark 0x0/0xf -m tcp -m multiport --ports 20,21,25,80,110,443,993,995 -m comment --comment "ftp, smtp, http(s), imap" -j MARK --set-xmark 0x33/0xff
[0:0] -A qos_Default_ct -p tcp -m mark --mark 0x0/0xf -m tcp -m multiport --ports 5190 -m comment --comment "AOL, iChat, ICQ" -j MARK --set-xmark 0x22/0xff
[0:0] -A qos_Default_ct -p udp -m mark --mark 0x0/0xf -m udp -m multiport --ports 5190 -m comment --comment "AOL, iChat, ICQ" -j MARK --set-xmark 0x22/0xff
[0:0] -A qos_Default_ct -j CONNMARK --save-mark --nfmask 0xff --ctmask 0xff
COMMIT
# Completed on Sat Nov 19 15:34:09 2022
# Generated by iptables-save v1.8.7 on Sat Nov 19 15:34:09 2022
*filter
:INPUT ACCEPT [2009420:2287948543]
:FORWARD ACCEPT [3165566:2731339206]
:OUTPUT ACCEPT [1414588:374865041]
COMMIT
# Completed on Sat Nov 19 15:34:09 2022
table inet fw4 {
chain input {
type filter hook input priority filter; policy accept;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname "eth1" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "eth0" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic"
iifname "wireguard" jump input_wireguard comment "!fw4: Handle wireguard IPv4/IPv6 input traffic"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname "eth1" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "eth0" jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
iifname "wireguard" jump forward_wireguard comment "!fw4: Handle wireguard IPv4/IPv6 forward traffic"
jump handle_reject
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
oifname "eth1" jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "eth0" jump output_wan comment "!fw4: Handle wan IPv4/IPv6 output traffic"
oifname "wireguard" jump output_wireguard comment "!fw4: Handle wireguard IPv4/IPv6 output traffic"
}
chain prerouting {
type filter hook prerouting priority filter; policy accept;
iifname "eth1" jump helper_lan comment "!fw4: Handle lan IPv4/IPv6 helper assignment"
}
chain handle_reject {
meta l4proto tcp reject with tcp reset comment "!fw4: Reject TCP traffic"
reject comment "!fw4: Reject any other traffic"
}
chain syn_flood {
limit rate 25/second burst 50 packets return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
chain input_lan {
ct status dnat accept comment "!fw4: Accept port redirections"
jump accept_from_lan
}
chain output_lan {
jump accept_to_lan
}
chain forward_lan {
tcp dport 853 counter packets 150 bytes 9600 jump handle_reject comment "!fw4: ubus:https-dns-proxy[instance1] rule 1"
udp dport 853 counter packets 0 bytes 0 jump handle_reject comment "!fw4: ubus:https-dns-proxy[instance1] rule 1"
jump accept_to_wan comment "!fw4: Accept lan to wan forwarding"
jump accept_to_wireguard comment "!fw4: Accept lan to wireguard forwarding"
ct status dnat accept comment "!fw4: Accept port forwards"
jump accept_to_lan
}
chain helper_lan {
}
chain accept_from_lan {
iifname "eth1" counter packets 45472 bytes 10460478 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain accept_to_lan {
oifname "eth1" counter packets 26 bytes 8675 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain input_wan {
ct status dnat accept comment "!fw4: Accept port redirections"
jump reject_from_wan
}
chain output_wan {
jump accept_to_wan
}
chain forward_wan {
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
ct status dnat accept comment "!fw4: Accept port forwards"
jump reject_to_wan
}
chain accept_to_wan {
oifname "eth0" counter packets 19 bytes 6020 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain reject_from_wan {
iifname "eth0" counter packets 8582 bytes 417802 jump handle_reject comment "!fw4: reject wan IPv4/IPv6 traffic"
}
chain reject_to_wan {
oifname "eth0" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject wan IPv4/IPv6 traffic"
}
chain input_wireguard {
jump reject_from_wireguard
}
chain output_wireguard {
jump accept_to_wireguard
}
chain forward_wireguard {
jump reject_to_wireguard
}
chain accept_to_wireguard {
oifname "wireguard" counter packets 14006 bytes 1776596 accept comment "!fw4: accept wireguard IPv4/IPv6 traffic"
}
chain reject_from_wireguard {
iifname "wireguard" counter packets 66 bytes 3755 jump handle_reject comment "!fw4: reject wireguard IPv4/IPv6 traffic"
}
chain reject_to_wireguard {
oifname "wireguard" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject wireguard IPv4/IPv6 traffic"
}
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
iifname "eth1" jump dstnat_lan comment "!fw4: Handle lan IPv4/IPv6 dstnat traffic"
iifname "eth0" jump dstnat_wan comment "!fw4: Handle wan IPv4/IPv6 dstnat traffic"
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname "eth1" jump srcnat_lan comment "!fw4: Handle lan IPv4/IPv6 srcnat traffic"
oifname "eth0" jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic"
oifname "wireguard" jump srcnat_wireguard comment "!fw4: Handle wireguard IPv4/IPv6 srcnat traffic"
}
chain dstnat_lan {
meta nfproto ipv4 tcp dport 53 counter packets 4 bytes 240 redirect to :53 comment "!fw4: ubus:https-dns-proxy[instance1] redirect 0"
meta nfproto ipv4 udp dport 53 counter packets 22921 bytes 1588369 redirect to :53 comment "!fw4: ubus:https-dns-proxy[instance1] redirect 0"
ip saddr 10.x.x.0/26 ip daddr 216.x.x.229 tcp dport 4xx2 dnat ip to 10.x.x.23:4xx2 comment "!fw4: katz 01 (reflection)"
ip saddr 10.x.x.0/26 ip daddr 216.x.x.229 udp dport 4x7x dnat ip to 10.x.x.23:4x7x comment "!fw4: katz 02 (reflection)"
}
chain srcnat_lan {
ip saddr 10.x.x.0/26 ip daddr 10.x.x.23 tcp dport 4xx2 snat ip to 10.x.x.1 comment "!fw4: katz 01 (reflection)"
ip saddr 10.x.x.0/26 ip daddr 10.x.x.23 udp dport 4x7x snat ip to 10.x.x.1 comment "!fw4: katz 02 (reflection)"
}
chain dstnat_wan {
meta nfproto ipv4 tcp dport 4xx2 counter packets 0 bytes 0 dnat ip to 10.x.x.23:4xx2 comment "!fw4: katz 01"
meta nfproto ipv4 udp dport 4x7x counter packets 0 bytes 0 dnat ip to 10.x.x.23:4x7x comment "!fw4: katz 02"
}
chain srcnat_wan {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic"
}
chain srcnat_wireguard {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wireguard traffic"
}
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
}
chain raw_output {
type filter hook output priority raw; policy accept;
}
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
}
chain mangle_output {
type route hook output priority mangle; policy accept;
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "eth0" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 ingress MTU fixing"
oifname "eth0" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 egress MTU fixing"
iifname "wireguard" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wireguard IPv4/IPv6 ingress MTU fixing"
oifname "wireguard" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wireguard IPv4/IPv6 egress MTU fixing"
}
}
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
inet 216.x.x.229/24 brd 216.x.x.255 scope global eth0
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
inet 10.x.x.1/26 brd 10.x.x.63 scope global eth1
valid_lft forever preferred_lft forever
9: wireguard: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
inet 10.x.x.7/32 brd 255.255.255.255 scope global wireguard
valid_lft forever preferred_lft forever
default dev wireguard proto static scope link
10.x.x.0/26 dev eth1 proto kernel scope link src 10.x.x.1
76.x.x.90 via 216.x.x.1 dev eth0 proto static
216.x.x.0/24 dev eth0 proto kernel scope link src 216.x.x.229
local 10.x.x.7 dev wireguard table local proto kernel scope host src 10.x.x.7
broadcast 10.x.x.0 dev eth1 table local proto kernel scope link src 10.x.x.1
local 10.x.x.1 dev eth1 table local proto kernel scope host src 10.x.x.1
broadcast 10.x.x.63 dev eth1 table local proto kernel scope link src 10.x.x.1
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 216.x.x.0 dev eth0 table local proto kernel scope link src 216.x.x.229
local 216.x.x.229 dev eth0 table local proto kernel scope host src 216.x.x.229
broadcast 216.x.x.255 dev eth0 table local proto kernel scope link src 216.x.x.229
0: from all lookup local
2: from 10.x.x.27 lookup 2
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Jul 31 08:12 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 118 Nov 18 17:41 /tmp/resolv.conf
-rw-r--r-- 1 root root 113 Nov 18 17:40 /tmp/resolv.conf.d/resolv.conf.auto
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 113 Nov 18 17:40 resolv.conf.auto
==> /etc/resolv.conf <==
# /tmp/resolv.conf generated by Unbound UCI 2022-11-18T17:41:17-08:00
nameserver 127.0.0.1
nameserver ::1
search lan.
==> /tmp/resolv.conf <==
# /tmp/resolv.conf generated by Unbound UCI 2022-11-18T17:41:17-08:00
nameserver 127.0.0.1
nameserver ::1
search lan.
==> /tmp/resolv.conf.d <==
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface LAN
nameserver 1.1.1.1
# Interface WAN
nameserver 8.8.8.8
nameserver 8.8.4.4
nameserver 209.x.x.13